


Rhadamanthys, an info stealer, written in C++, was first seen on August 22, 2022. This stealer, still gets updates and patched regularly (Figure 1). Version 0.5.0 shifted towards a more customizable framework allowing threat actors to counter security measures and exploit vulnerabilities by deploying targeted plugins, such as ‘Data Spy,’ which monitors RDP logins.
Version 0.5.0 also brought enhancements in stub construction, client execution, fixes for cryptocurrency wallet targeting, and adjustments in Discord token acquisition.
Version 0.5.1 included new stealing capabilities and enhanced evasion, including a new plugin system allowing for increased customization for various distribution needs. It has become more modular and customizable.
0.5.1 already included a new Clipper plugin, the ability to recover deleted Google account cookies, Telegram notification options and an ability to evade Windows Defender.
0.5.2 is the current working version.
Rhadamanthys is operated on a Malware as a Service (MaaS) model. The malware is compatible with XP-Win11, and adaptively supports X86 & X64 architecture. The developers declare that all network communications are encrypted. Each structure has a unique encryption key.
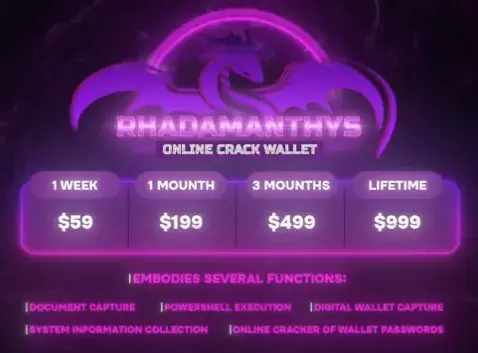
Rhadamanthys is programmed to extract a range of data, including Registry information, computer-specific details, and browser data. The stealer is being sold in a dedicated Telegram channel and its price varies between $59 and $999 for a lifetime subscription (Figure 2).
The most common delivery method for Rhadamanthys is through Google Ads (malvertising). Campaigners of this stealer often create Google Ads that leads to fake download pages of a commonly used apps such as Notepad++, which contains a malicious loader.
The loaders responsibility is to load and run Rhadamanthys in the victim’s machine, either by downloading it or by dynamically load it to memory – it depends on the campaigner’s creativity and abilities.
In addition, Rhadamanthys is also being delivered through malspam campaigns that urges the victim to sign a PDF document regarding business related issues. The PDF is often a malicious loader that eventually run the Rhadamanthys stealer within the victim’s machine.
In late 2023, reports emerged of malware operations exploiting an undocumented Google Chrome API, specifically the OAuth “MultiLogin” endpoint, to generate fresh authentication cookies for Google accounts. Lumma and Rhadamanthys initially used this technique, and later it was adopted by Stealc, Medusa, RisePro, and Whitesnake.
Like most stealers, Rhadamanthys is no different in its impact on the victims it claims. When compromised, the victim will loos all private information and other relevant assets the threat actors behind Rhadamanthys configured the stealer to obtain.
The information Rhadamanthys usually aim to obtain are saved passwords, cookies and sessions from various browsers. In addition, it will obtain credentials and session keys of Discord and Telegram. It also targets files within the victim’s machine, mostly in the desktop along with taking screenshots. Finally, Rhadamanthys also stealer crypto wallets within the victim’s machine.
| Tactic | Technique |
|---|---|
| Initial Access | T0862 – Supply Chain Compromise |
| Credential Access | T1414 – Clipboard Data |
| Collection | T1414 – Clipboard Data |
| Collection | T1115 – Clipboard Data |
| Initial Access | T0819 – Exploit Public-Facing Application |
| Reconnaissance | T1592 – Gather Victim Host Information |
| Initial Access | T1195 – Supply Chain Compromise |
| Collection | T1113 – Screen Capture |
| Collection | T1513 – Screen Capture |
| Initial Access | T0817 – Drive-by Compromise |
| Initial Access | T1474 – Supply Chain Compromise |
| Initial Access | T1190 – Exploit Public-Facing Application |
| Persistence | T0859 – Valid Accounts |
| Lateral Movement | T0859 – Valid Accounts |
| Credential Access | T1417 – Input Capture |
| Collection | T1417 – Input Capture |
| Initial Access | T1566 – Phishing |
| Initial Access | T1456 – Drive-By Compromise |
| Credential Access | T1056 – Input Capture |
| Collection | T1056 – Input Capture |
| Initial Access | T1199 – Trusted Relationship |
| Reconnaissance | T1591 – Gather Victim Org Information |
| Initial Access | T1189 – Drive-by Compromise |
| Collection | T0852 – Screen Capture |
| Reconnaissance | T1590 – Gather Victim Network Information |
| Privilege Escalation | T1078 – Valid |

©1994–2026 Check Point Software Technologies Ltd. All rights reserved.
Copyright | Privacy Policy | Cookie Settings | Get the Latest News
Fill in your business email to start


