


Highly motivated, problem solver, dot connector, energetic multi-dimensional & professional management with commercially oriented, customer service skills & PMO abilities in high-growth, fast-paced organizations.
Within the context of the recent Conti leaks, we have seen the Jabber chats, indicating the size, scope, order, and structure of the Conti group. The subsequent leaks contained screenshots, documents, and the holy-grail – the source code itself.
Browsing around in the leaked archives, we noticed a file called “техника безопасности”, which according to Google translate, means “safety techniques”. The document holds 12 (well, 13, since it counts from 0…) points, as seen in Figure 1. After translating the document’s content, it turned out to be safety precautions and general security instructions for new members recruited to the Conti organization.
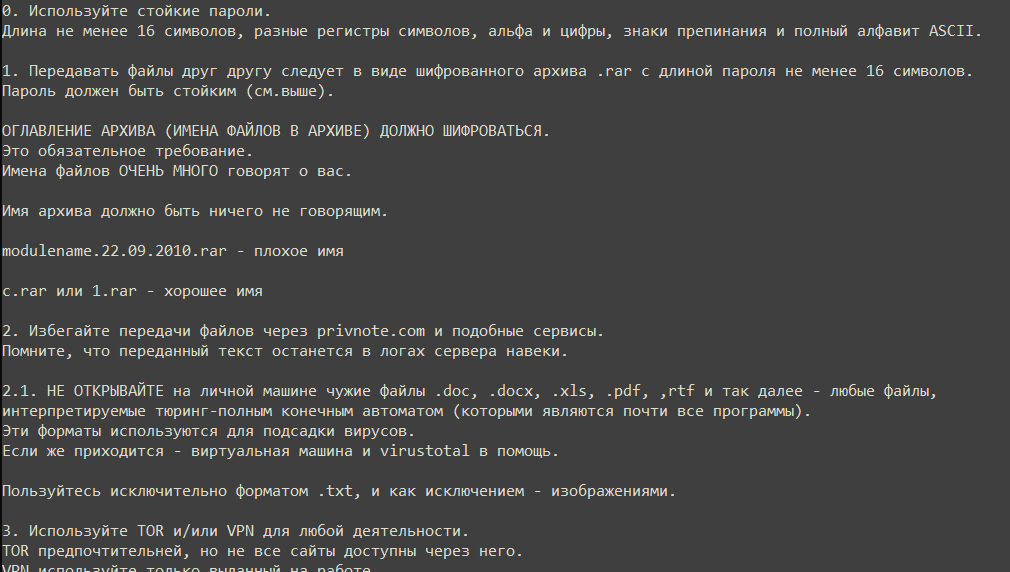
Cyberint’s research team thought we could shed the light on these points, and maybe use them as a guide to successful must-do’s for all personal use, or even a company wanting its employees to be vigilant, and know the risks and how to be well protected. If you will, these are Conti’s 12 commandments for cyber security.

Well, isn’t that obvious!? 2022 is here, and everyone should surely be aware of this first pretty obvious point by now.
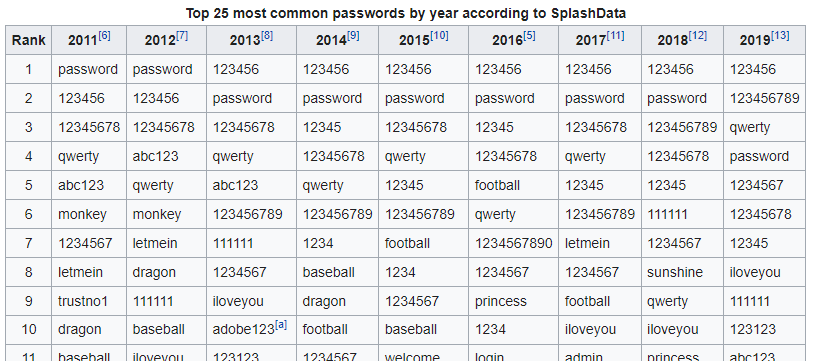
However, we’ve browsed online for the most used passwords for 2022, which surprisingly, continue to be “123456”, “password”, and other, we must say, annoyingly simple, passwords.
Out of the top 10 passwords for 2022, all are either only numeric, or relate to the words “password”, “qwerty”, or “iloveyou”. All are lowercase, without any appearance of an uppercase letter, not to mention a special sign.
Nothing has changed in the past decade or so, as you can see in Figure 2.
As the Conti group suggests, it’s better to use passwords that are complex, long, mixed cases, with a sign, as they could make the difference between a 10-minute successful brute force attack and, for example, a 10-month long brute force attack.
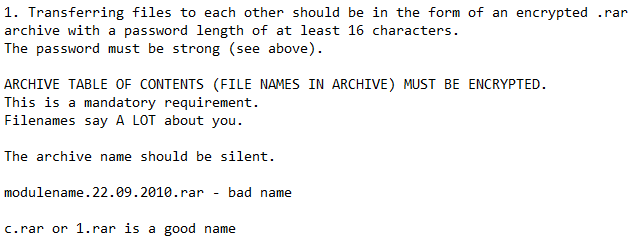
Looking at Conti’s second point, which relates to encrypting archives with passwords and using non-distinctive names, is very “Conti-like” behavior. However, we could also suggest avoiding too obvious, or overly “generous” file names, folders, or any mentions of slightly secret information within open archives.
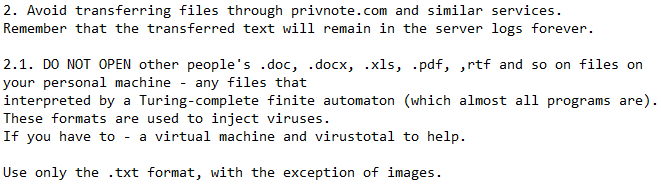
Well, most users will not use ‘privnote.com’ for their day-to-day usage. However, some will use pastebin.com, or other paste sites, that will hold somewhat sensitive data. This even goes to different online repositories, which could store private data or hardcoded credentials. This data could be valuable to a threat actor looking for a way in and trying to harvest any piece of information he could find. Try and avoid public 3rd party services that could hold companies’ data online, as these could be logged, without the company’s knowledge.
Section 2.1, although only a sub-section of point 2, relates to a broader subject, which involves file execution and infecting a machine. This point should be THE point in the entire doc. Trust no-one. If you’re not sure of the origin of a doc, pdf, or any other file delivered to you, ask your company’s IT or security team for their assistance on this matter.
This use case arises most frequently when dealing with threat actors successfully finding a way into an organization. It’s the human factor – trust no one.

This section, again, talks specifically about Conti’s group and using TOR or VPN for any activity, to support anonymity. Looking at it from a broader perspective, a VPN is used to change the IP you are currently use. It will, in a company’s use case, allow you to access assets that require a specific IP, usually the one used at your office. It will also allow you to use your company’s security systems since traffic will be directed throughout these security controls.
If your company’s work module, specifically in the COVID era and work-from-home methodology, uses VPN, you also need to understand the consequences of a threat actor accessing to your VPN creds, for example, which could basically provide him with an entry into the company’s assets.
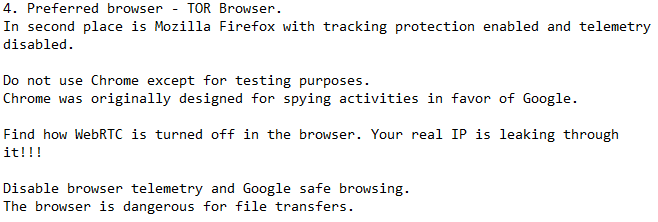
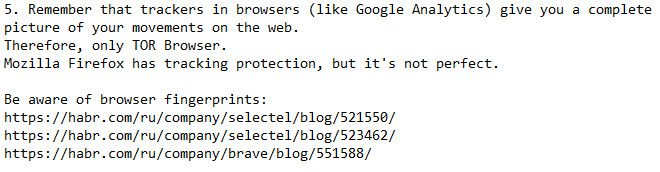
Every employee with an internet connection leaves a trail of bread-crumbs behind him, which holds sensitive data. Again, no one is expected to use a TOR-browser for their day-to-day work, however, do understand that every website you visit, every forum you post on, tracks your behavior, your likes, dislikes, and obviously, your IP.
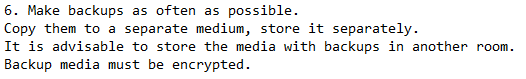
Isn’t this ironic? Conti’s group, one of the most notorious groups out there, suggests its “employees” have backups. Often. This shows the great deal a ransomware attack could cause, and eventually, shut down an operation. This could be risky, even for a ransomware group, just as with any company.
Have a backup plan on hand, and obviously a restore plan, so you won’t get caught with without the ability to use your backup.
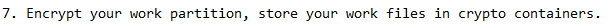

Use encryption wherever you can. This goes a long way to help you battle a threat actor who gains access to your network, looks for valuable data, and comes across a “wall” of encrypted content. Without being able to decrypt it, he has nothing and will either try other locations internally in your network or move along to other victim entirely.
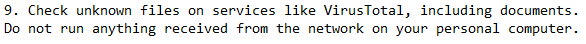
This point correlates to the important sub-section 2.1. Every file being sent to you could be malicious. So act accordingly. Check files with Virustotal, or other services that scan for suspicious files. However, note that what is being uploaded to 3rd party vendors could end up publicly available to all. As they state: “Do not run anything received from the network on your personal computer”.

The Conti group needs to avoid being detected. That’s not the case for you, however, their instructions could also hold true for password reuse. Avoid reuse of passwords online. Have different passwords for every service, and try and refresh them from time to time. Often, databases get leaked, and the same password you use could be the entry to other services.
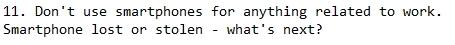
Smartphones are used on a daily basis and are an important part of today’s work practice. Obviously, this rule can’t be enforced with most companies, with the possible exception of government secret services. But we do feel we can generalize, and mention mobile malware, and untrusted installation of applications.
Using only trusted sources, such as Google Play Store or Apple Store, will keep you safer, even if not 100% safe, since we do hear about an occasional application slipping past the gates of these two giant applications stores. For example, just last week, SharkBot malware was found after successfully infiltrating the Google Play Store, posing as an Android antivirus app.
Don’t talk. As simple as that. Don’t give out any information you do not need to. Be cautious. There are no free gifts, especially not online. If it sounds too good to be true, then it probably is.
As it appears, ransomware groups, and Threat Actors in general, are not that different from any other employee, let alone security researchers. Both tend to keep to themselves, avoid sharing too many personal details about themselves, and if they do, they make completely sure they understand the consequences of public exposure. In today’s world, we all should be extremely cautious online, understand the risks, both personal as well as to our company as employees.
Fill in your business email to start


