


2023 was full of cases, campaigns, arrests and developments worldwide in the cybersecurity world.
Through continued research and monitoring of various threats and risks worldwide, the Cyberint Research Team forecasts how they will affect our lives in 2024.
Cyberint considered many factors in our predictions for 2024 as we wanted to emphasize how these risks will react to technological, political and strategic trends.
When we consider these developments and look forward to 2024, we can see several main key themes:
2023 witnessed several high-profile cyber incidents, underlining the massive financial incentives for attackers. The trend indicates a concerning trajectory where cybercrime becomes more common and more lucrative.
With a 55.5% rise in cases compared to 2022, the ransomware industry is only one example. The entire cybercrime industry, including access brokers, info stealer campaigners, and scammers, is getting more profitable with relatively low risk for threat actors.
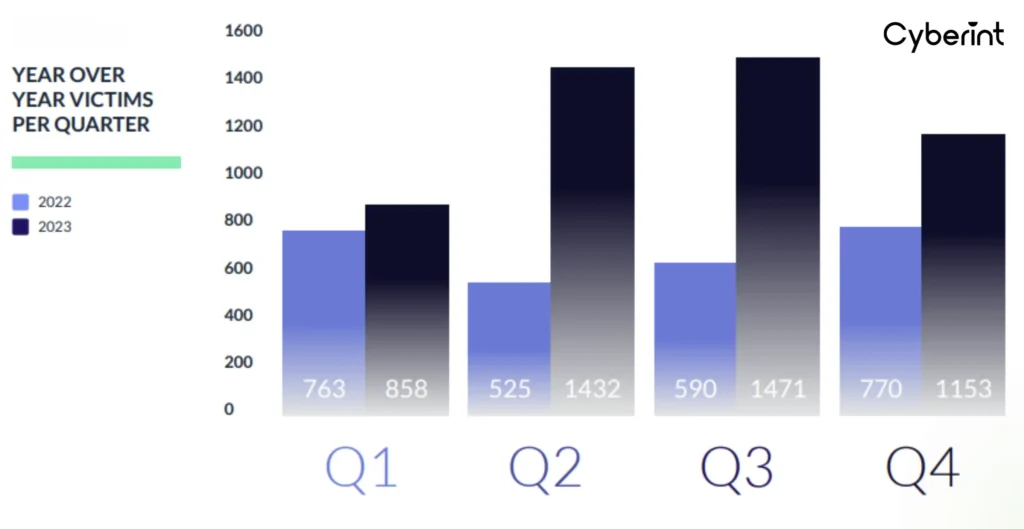
A combination of factors, including technological advancements, the growing digital economy, and the expansion of cybercriminal capabilities, drives this trend.
Finally, in recent years, the Ransomware-as-a-Service (RaaS) business model has proved very effective among ransomware groups and allowed new types of threat actors from all levels to join this industry.
Unfortunately, the Cyberint Research Team doesn’t see anything that will mitigate or stop the ransomware industry from growing in 2024. As this industry becomes very lucrative for threat actors, we are likely going to see some new bold faces in the ransomware industry along with comebacks of some groups that disappeared in 2023, such as HIVE.
The digital asset landscape is another aspect we should consider. Cryptocurrencies and NFTs presents a fertile ground for cybercriminals. Their anonymity, coupled with their increasing value, makes them attractive targets. The decentralized nature of these assets often leaves regulatory gaps, which cybercriminals exploit for profit.
The cryptocurrency industry, along with its community, was one of the most successful playgrounds for threat actors of all kinds this year as we saw NFT scamming campaigns, info stealers’ initial infections through crypto Discord communities, blockchain vulnerability exploitations and many more.
As with all new technologies, threat actors will always look to utilize it to their benefit, especially when this technology becomes mainstream. At the beginning of 2024, the crypto ETFs got approved by the feds, which might lead to the ETF funds being a main target for major threat groups such as Lazarus as they will obtain huge amounts of cryptocurrency.
In 2024, the Cyberint Research Team expects to see a rise in ransomware and cybercrime activities targeting financial institutes related to the cryptocurrency ETFs. A rise of crypto scams revolving around the ETFs trend, given that the NFT trend died somewhere in mid-2023 is forecast.
The adoption of Artificial Intelligence (AI) by threat actors marks a significant shift in the cyber threat landscape. AI’s capabilities, when harnessed for malicious purposes, can lead to highly sophisticated cyber-attacks.
AI is currently employed in various cyber attacks, most notably in advanced phishing operations, malware and tool development, QA and identification testing and much more. AI algorithms can tailor phishing messages based on user behavior, significantly increasing the success rates of these attacks. Similarly, AI-driven tools can analyze and find vulnerabilities in security systems more efficiently than human hackers.
Several examples of how threat actors can use this technology depend on the motivation:
• Hacktivists might use this technology to spread fake news, create deep fake videos and utilize this technology to control social media botnets.
• Initial access brokers and scammers will utilize this technology as it will make their lives easier by creating very reliable phishing pages, social media profiles and pages, and even fake company websites.
• With more advanced access, brokers and ransomware operators will use it to improve their code, find bugs in their code, research vulnerabilities, find easy ways to exploit it, and much more.
• Finally, as A.I helps us shorten our design and development times for software products and other projects; It also helps threat actors optimize and improves productivity when developing a new exploit or malware.
While the future of AI in 2024 sounds alarming, threat actors will have a harder time developing their LLMs and GPT engines, given the high costs today. At the same time, security and big tech companies can afford to invest in these technologies to improve their defense mechanisms and surpass most threat actors’ capabilities. With that, we must not forget that state-sponsored and well-funded opponents can and will use these technologies in various sophisticated ways.
Geopolitical tensions have a significant impact on the cyber threat landscape. Nation-states often use cyber operations as tools for espionage, sabotage, and influence, particularly during conflicts.
In addition, these conflicts tend to draw massive attention from hacktivist groups. These activities range from data leaks and DDoS campaigns targeting government, popular organizations, and critical infrastructure entities within the targeted country.
In 2022, Russia-Ukraine showed us just how a physical conflict between two countries might start a whole different war in the cyber world; in 2023, it also happened with the Israel-Hamas war that is still ongoing.
Looking forward to 2024, we have two major conflicts that can lead to even greater cyber warfare than Russia- Ukraine. The Israel-Hamas war will still draws the attention of threat actors mostly to Israel and we might see more sophisticated campaigns targeting Israel rather than DDoS attacks that Israel has experienced ever since the beginning of the war.
The second potential conflict that might take place in 2024 is the Taiwan elections, which are a growing concern and might lead to a new geopolitical conflict between China and Taiwan. This conflict will likely include massive activities of Russian and Chinese APTs, mostly hacktivists that will perform DDoS and data leak campaigns, supporting Taiwan.
Cyber operations may become a standard part of warfare and diplomatic strategy, leading to a more complex and dangerous global cyber threat landscape. The potential for cyber warfare to escalate conflicts or be used as a covert form of aggression is high.
Major and popular events in our lives tend to be the best playground for threat actors. Contrary to the wars and conflicts, “events” are large-scale ceremonies, competitions, and celebrations, such as the Olympics, elections, Black Friday, etc.
There is evidence of large spikes in various types of cyber-attacks surrounding major events, including scamming, phishing, espionage, DDoS, data leaks and defacements.
Some events are more potentially dangerous than others. In 2024, the U.S. elections are one of the events that can draw the attention of many threat actors, including state-sponsored ones.
The U.S. elections in 2020 and 2016 were already events leveraged by threat actors to promote their motivation and dominance. Russian entities, including military and intelligence units are suspected to have engaged in various cyber activities aimed at influencing the U.S. political process, spreading disinformation, and sowing discord among the electorate.
Threat actors can potentially do the same to the upcoming 2024 U.S. elections for malicious purposes in several ways.
During this politically charged time, they may employ tactics like disinformation campaigns, social engineering, and cyberattacks to sow discord, manipulate public opinion, or compromise the integrity of the electoral process.
Disinformation campaigns, particularly through social media platforms, can spread false narratives to manipulate voters’ perceptions and create confusion. Phishing emails and spoofed websites could impersonate legitimate election-related entities to trick individuals into revealing sensitive information or installing malware.
Cyberattacks targeting critical infrastructure, voter databases, or campaign organizations could disrupt the electoral process or compromise the confidentiality of voter data. In extreme cases, this can lead to altering the future of a country and the beginning of an era the citizens of that country did not choose or planned.
For many reasons the 2024 Paris Olympics, Paralympic Games, and the UEFA Euro Cup are hot targets for threat actors this year, exploiting the high visibility, global interest, and significant digital infrastructure involved in such events.
Threat actors can leverage these events for gain, targeting digital infrastructure, like scoring systems, ticketing platforms, and broadcasting networks, disrupting these systems and causing chaos. They can damage the event’s reputation, potentially leading to financial losses.
Another technique that can be used in these events is targeting individuals through phishing. This could involve stealing tourists’ personal data through phishing sites, pretending to be sites for buying tickets or ordering AirBNBs.
Finally, non-state actors, like terrorist organizations, might use global attention to disseminate propaganda and recruit members.

Fill in your business email to start.
The Lunar New Year, an event celebrated by billions of people worldwide, especially in East and Southeast Asian cultures, can be leveraged by threat actors in various ways for their campaigns, considering its cultural significance and widespread observance.
When considering this event, we can see that most ways for threat actors to exploit or take advantage of this event revolve around financially motivated campaigns such as phishing and shopping scams, traveling scams, and impersonation.
Given the fact that this is a big event in Asia, certain hacktivist groups might choose this event to launch attacks, mostly DDoS, against Asian entities.
The recent results in Taiwan’s elections and the threats of China might lead hacktivists to target Chinese entities as a result on this particular day, given that it is a very symbolic day for China and other Asian countries.
Unlike the U.S. Elections or the Olympic games, some cases are repetitive and happen every year. One great example for these events is the sale days that happen towards the end of every year such as Black Friday, Cyber Monday and Chinese Singles’ Day.
Threat actors can take advantage of the frenzy of these sales days to their advantage in various cyberattacks. With consumers eagerly searching for discounted deals online, cybercriminals may use tactics like phishing emails, fake shopping websites, and malicious advertisements to lure unsuspecting shoppers.
These fraudulent schemes can lead users to enter sensitive personal information, such as credit card details, into fake websites, enabling identity theft or financial fraud. Additionally, cybercriminals can capitalize on the increased web traffic during these days to distribute malware through deceptive downloads or exploit vulnerabilities in popular shopping apps and websites.
While third-party services have become a prominent tool for every organization worldwide, they sometimes bring with them massive risks. The growing dependency of organizations on global supply chain services has exposed new cybersecurity vulnerabilities.
In 2023, we saw just how devastating a supply-chain attack can be and how broad an impact it can have with the successful MOVEit campaign, mostly initiated by Cl0p.
Targeting supply chain services was started, as most attack trends, by APTs, with the SolarWinds campaign. As threat actors look to evolve and improve their craft, they look at espionage and other APT activities to follow their techniques.
After major success in 2023 with the MOVEit campaign by Cl0p and other supply chain campaigns during the year, it seems inevitable that ransomware and other cybercrime groups will most likely look to compromise supply chain services. Given the simplicity and the higher success rate due to misconfigurations and other security issues, Cyberint forecasts a steep rise in supply chain attacks.
In 2023, the winds of change were felt in the vision and execution of law authorities worldwide fighting cybercrime in general and the ransomware industry in particular.
One of the most relevant strategic moves by law authorities was to merge efforts and resources between everyone to fight the cybercrime industry and see it as a global threat rather than a national threat. By doing so, the reach of the law’s hand was way greater than any year before. We have already seen some success with major arrests of key players and affiliates of various threat and ransomware groups in 2023.
In addition to that, some intelligence entities such as the MI6, the FBI and the CIA took more of an “aggressive” approach and, in a way, left some traditional techniques behind as they turned to more offensive solutions against threat groups and their infrastructures.
During the past year, we have seen many cases of law authorities compromising and taking down forums, data leak sites and marketplaces, along with fully compromising and shutting down threat actors’ infrastructures.
In 2024, the Cyberint Research Team looks to see more of these cases where law authorities compromise threat actors’ infrastructures and force them to shut down. As arresting individuals is not always possible due to geolocation, offensive solutions seem more possible and might be easier to apply. Although the individuals and main criminals are not always arrested, these actions force them to go off grid for some time and buy precious time where they are not active.
Cyberint, the Impactful Intelligence company, reduces risk by helping organizations detect and mitigate external cyber threats before they have an adverse impact. The Cyberint Argos platform’s patented technology provides superior visibility through continuous discovery of the evolving attack surface, combined with the automated collection and analysis of vast quantities of intelligence from across the open, deep and dark web. A team of global military-grade cybersecurity experts work alongside customers to rapidly detect, investigate, and disrupt relevant threats – before they have the chance to develop into major incidents. Global customers, including Fortune 500 leaders across all major market verticals, rely on Cyberint to protect themselves from an array of external risks, including vulnerabilities, misconfigurations, phishing, impersonation attacks, malware infections, exposed credentials, data leaks, fraud, and 3rd party risks.

©1994–2026 Check Point Software Technologies Ltd. All rights reserved.
Copyright | Privacy Policy | Cookie Settings | Get the Latest News
Fill in your business email to start


