


Following high profile headlines of critical vulnerabilities affecting Microsoft Exchange servers, as detailed in our previous blog [1], proof-of-concept exploits have become publicly available and appear to have been utilized by a financially-motivated threat actor in the seemingly manual deployment of a new ransomware threat dubbed ‘Dearcry’.
First identified by Michael Gillespie (@demonslay225) in an 11 March 2021 tweet[2] (Figure 1), submissions to the researcher’s online service ‘ID Ransomware’ [3] were observed as originating from Microsoft Exchange server IP addresses and featured identifiers including a .CRYPT file extension and an encrypted file header of DEARCRY!.
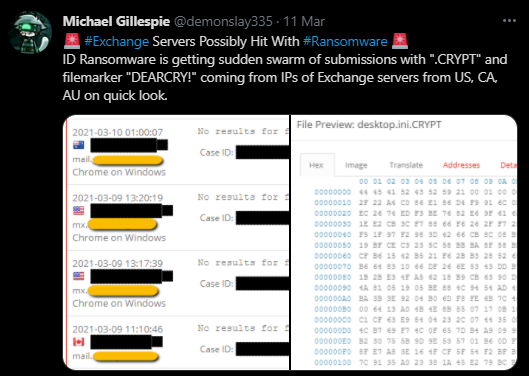
Figure 1 – Initial observation by Michael Gillespie (Twitter: @demonslay335)
Current observations suggest that those behind these attacks are attempting to infect as many vulnerable Microsoft Exchange servers as possible which, given readily available exploits, could be considered ‘low hanging fruits’ with the potential for a lucrative return should victims pay the ransom demands.
Unlike big game hunter ransomware attacks, ‘steal, encrypt and leak’ or double extortion tactics do not appear to have be used and ransom demands are reportedly in the region of sixteen thousand US dollars ($16,000).
Based on our analysis, this ransomware threat appears to have been written hastily, likely in an attempt to capitalize on the immediate Microsoft Exchange vulnerability situation, and is therefore lacking in functionality or incomplete.
Specifically, there is no attempt to terminate any running processes prior to commencing the encryption phase and therefore security and backup solutions will continue to run, potentially allowing the threat to be detected and thwarted. Furthermore, the failure to terminate processes prevents the ransomware from encrypting ‘open’ files whilst the method of reading the original file into memory for encryption, writing this data to a new file and then deleting the original file could allow data recovery in some cases.
Whilst these ‘deficiencies’ may offer a modicum of relief to victims, the wide selection of file types that are encrypted will no doubt cause considerable damage to any affected host.
Utilizing the Open SSL library rather than the Windows CryptoAPI as favoured by many threat actors, the ransomware appears to encrypt data using AES-256 with the key being encrypted by an embedded RSA public key. Subsequently, this public key appears to be cryptographically hashed and this resulting value is embedded within the ransom note to allow a ‘decryptor’ to be provided by threat actor to a paying victim.
Of the samples we analysed, the RSA public key appears to be unique to each ransomware binary and it is therefore possible that threats are generated on a ‘per-victim’ basis.
Theoretically, if this is not the case and the same RSA public key is used for multiple victims, one paying victim would be able to share the decryption method with others targeted by the same threat.
Based on what is known so far, Microsoft Exchange servers targeted with this ransomware threat have been compromised via the following vulnerabilities as seen in the high-profile HAFNIUM attacks:
SYSTEM privileges.Notably, CVE-2021-26857 provides code execution which, in this instance, is likely exploited by the threat actor to execute the Dearcry payload with elevated privileges.
Upon execution the ransomware appears to have basic anti-analysis capabilities that attempt to determine if the process is being ‘debugged’ and, if not, proceeds to utilize the Windows Service Control Manager (SCM) via the OpenSCManagerA function to create and start a service named msupdate (Figure 2).
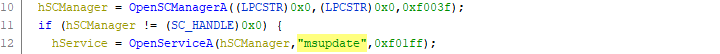
Figure 2 – Create of a Windows service named ‘msupdate’
In addition to providing an element of persistence, the creation of a service may be an attempt to ‘hide’ the ransomware process from casual inspection.
Having created the ‘msupdate’ process, the ransomware makes use of the opensource ‘OpenSSL’ library to perform a cryptographic hash process on the embedded RSA public key which is then embedded into a ransom note template along with the threat actor email addresses (Figure 3).
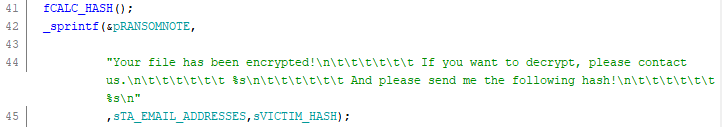
Figure 3 – Ransom note creation (email addresses and victim hash replace the %s placeholders)
Highlighting the lack of complexity in this threat, the strings used within this process, and others, are clearly visible (Figure 4) within the ransomware executable demonstrating that the threat has not been ‘packed’ or ‘crypted’, tactics commonly used to evade detection by antivirus solutions.
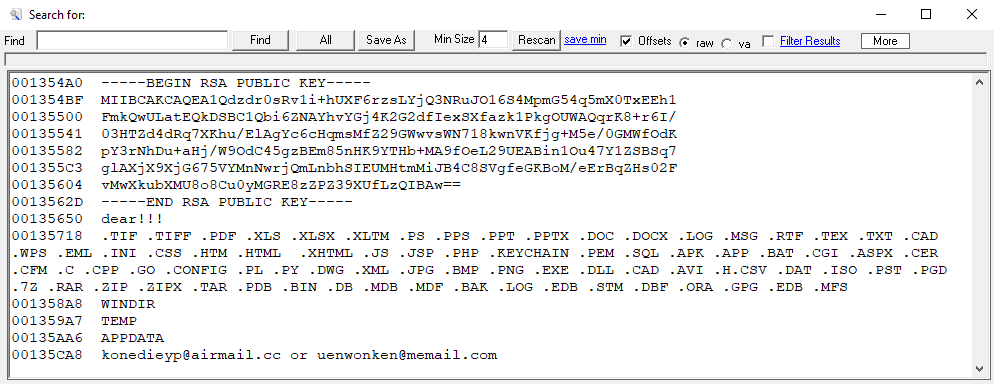
Figure 4 – Strings clearly visible within the ransomware executable
Subsequently, the Windows directory is identified using the C++ _getenv() function to query the %WINDIR% environment variable prior to enumerating the logical drives available on the compromised host (Figure 5) using the GetLogicalDrives() and GetLogicalDriveStringsA() functions.
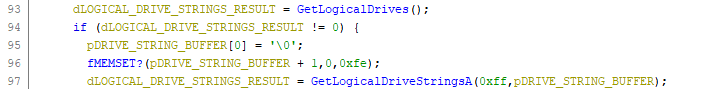
Figure 5 – Drive enumeration
Having determined which drives are available, the file enumeration process traverses each folder looking for potential files to encrypt, comparing file extensions against a fixed list of target file extensions. Notably, it appears that the threat actor responsible for this threat has updated the list of target file extensions on or around 8 March 2021, possibly to target a specific victim or to increase the effectiveness of their threat:
Once a file match has been found, the file appears to be opened, presumably in an attempt to determine if the file is ‘locked’ by some other process, and the first eight characters are read to determine if the file has already been encrypted as indicated by a DEARCRY! file header, 44 45 41 52 43 52 59 21 in hexadecimal (Figure 6/7).
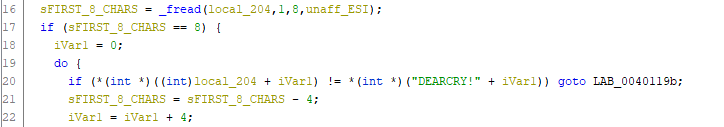
Figure 6 – Determine if the file is already encrypted with a DEARCRY! header
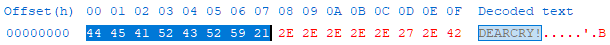
Figure 7 – Encrypted file header
Whilst more advanced ransomware threats utilize methods such as the Windows Restart Manager to handle open files, such as seen in Babuk Locker [4], open files appear to be ignored by Dearcry and will not be encrypted.
Again demonstrating an apparent lack of sophistication, the original filename is copied into a new string and .CRYPT appended in preparation for the creation of a new ‘encrypted’ file (Figure 8).
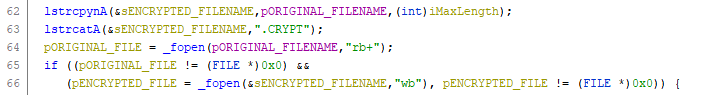
Figure 8 – New ‘encrypted’ file creation process
This method appears to read the original file into memory and encrypted before being written to a ‘new’ encrypted file, rather than modifying the original file ‘in-place’, and the original being deleted (Figure 9).

Figure 9 – Encrypted file closed and original file deletion
Given this approach, and likely dependant on the disk configuration of the compromised host, it may be possible to recover some encrypted data directly from disk.
Finally, once the encryption process is complete the ransom note, as prepared earlier, is written to the desktop in a file named readme.txt (Figure 10).
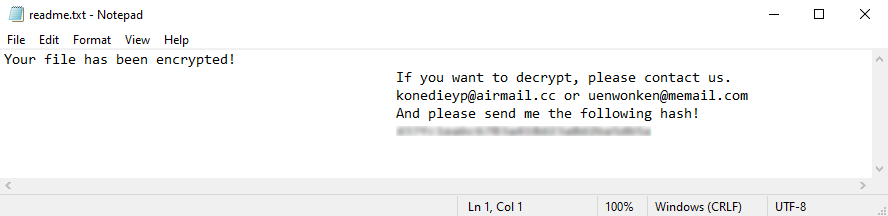
Figure 10 – Ransom note
SYSTEM privileged process can provide an early indication of compromise or nefarious activity.The following file hashes have been observed as recent Dearcry samples and are provided for reference.
10BCE0FF6597F347C3CCA8363B7C81A8BFF52D2FF81245CD1E66A6E11AEB25DA17c5161451b5edd31d903fb020afc7f9f2f130fea8fbd9248e069dde7f80efa32B9838DA7EDB0DECD32B086E47A31E8F5733B5981AD8247A2F9508E232589BFFE044D9F2D0F1260C3F4A543A1E67F33FCAC265BE114A1B135FD575B860D2B8C6FDEC933CA1DD1387D970EEEA32CE5D1F87940DFB6A403AB5FC149813726CBD65FEB3E6D30BA573BA23F3BD1291CA173B7879706D1FE039C34D53A4FDCDF33EDE6834d9f4a9e1888d82c70b72f30ced8aa68c009b55d03efffc94c466fbb3d047027119161d11ba87acc908a1d284b93a6bcafccc012e52ce390ecb9cd745bf27Based on strings observed within the initial Dearcry samples, the following basic YARA rule will match similar samples.
rule dearcry_ransomware
{
strings:
$str1 = "msupdate" // Service name
$str2 = "DEARCRY!" // Encrypted file header
$str3 = "EncryptFile.exe.pdb" // PDB artefact
$str4 = "/readme.txt" // Ransom note filename
$str5 = "Your file has been encrypted!" // Ransom note content
$str6 = "please send me the following hash!" // Ransom note content
condition:
all of them
}
readme.txt.CRYPTkonedieyp@airmail[.]ccuenwonken@memail[.]comNotably, airmal[.]cc redirects to ovo[.]sc, a domain hosted on a suspected malicious Romanian ASN (Figure 11).
Figure 11 – OVO Systems
Analysis of the DNS associated with this service indicates that it resolves to cock[.]li (Figure 12), a ‘privacy’ email service with the SPF records pointing to mail[.]cock[.]li, hosted on a suspected malicious Serbian ASN, M247 Ltd Belgrade (Figure 13) .
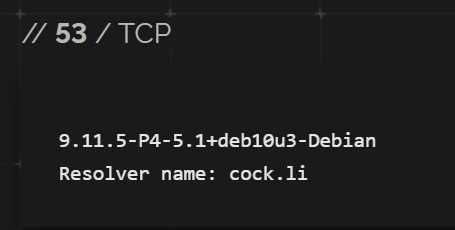
Figure 12 – DNS resolution
Figure 13 – Mail.Cock[.]li
The following list of IP’s was observed to be exploiting vulnerable Exchange servers in the wild, infecting them with Dearcry. However, since the publication of the exploits, it is safe to assume that this list may not be complete and likely include proxy, Tor exit nodes and/or VPN endpoints.
103.137.63.195103.212.223.210103.213.247.41104.248.49.97118.189.41.34130.255.189.21137.116.145.209139.162.98.150139.59.56.239157.230.221.198161.35.1.207161.35.1.225161.35.51.41165.232.154.116167.99.239.29168.63.134.28178.20.181.209182.153.128.230182.239.123.241182.239.124.180185.250.151.192The ransom note is represented within the threat binary as a string containing \n newlines, \t tabs and two %s string variables, the first of which being the threat actor contact email addresses and the second being a victim identifier:
"Your file has been encrypted!\n\t\t\t\t\t\t If you want to decrypt, please contactus.\n\t\t\t\t\t\t %s\n\t\t\t\t\t\t And please send me the following hash!\n\t\t\t\t\t\t%s\n"
027119161d11ba87acc908a1d284b93a6bcafccc012e52ce390ecb9cd745bf27fdec933ca1dd1387d970eeea32ce5d1f87940dfb6a403ab5fc149813726cbd65E044D9F2D0F1260C3F4A543A1E67F33FCAC265BE114A1B135FD575B860D2B8C610bce0ff6597f347c3cca8363b7c81a8bff52d2ff81245cd1e66a6e11aeb25dafeb3e6d30ba573ba23f3bd1291ca173b7879706d1fe039c34d53a4fdcdf33ede 17c5161451b5edd31d903fb020afc7f9f2f130fea8fbd9248e069dde7f80efa32b9838da7edb0decd32b086e47a31e8f5733b5981ad8247a2f9508e232589bff6834d9f4a9e1888d82c70b72f30ced8aa68c009b55d03efffc94c466fbb3d047Algo RSA
Format X.509
ASN1 Dump
RSA Public Key [86:d4:44:54:d9:7f:b4:90:94:2a:da:7f:a9:48:cc:06:82:62:dd:e8]
modulus: c8b042973f61b051917fd7e4df3d33998dabcf6275aaa19f578f034a33d5e257309e10a2e3fe7e0ba52c02193f748e3fe47c1b7d904088cc925cd0770f1541da13ab8c38c8795024163420675f41f8a4055a44a8d6e6de55d1e3c1dbfbe1ebc4feeafd2eff4733ef3d89977312954f3be023393b6c42014db6655e702daf9b0f66eb4760c91ff508941283a3286e5a36355179d002b77081b6fe5561f3679b81e757b1b549a6354c734dda4cf595e2c3568d33b7a3e697e99f951952e3baf7297cb0d96f7b58a6992a6730077eb0adee5574a8ee3b155f2c14296dba83623462a23f4f38288edbdd71097a96d2241dd45b8a380b8cc716baa67723a85259ea71
public exponent: 3
C:\Users\john\Documents\Visual Studio 2008\Projects\EncryptFile -svcV2\Release\EncryptFile.exe.pdb[1] https://blog.cyberint.com/hafnium-microsoft-exchange-server-vulnerability-bulletin
[2] https://twitter.com/demonslay335/status/1370125343571509250
[3] https://id-ransomware.malwarehunterteam.com/
Fill in your business email to start

