

In 2023, international law enforcement agencies intensified their efforts against ransomware, resulting in the decline of groups such as Hive, Ragnar Locker, and the collapse of ALPHV (BlackCat). These actions underscore the growing challenges faced by ransomware groups.
The significant operation in February 2024 targeting LockBit, which included arrests and the seizure of data leak sites and servers, represents one of the largest law enforcement actions taken against a major ransomware operation.
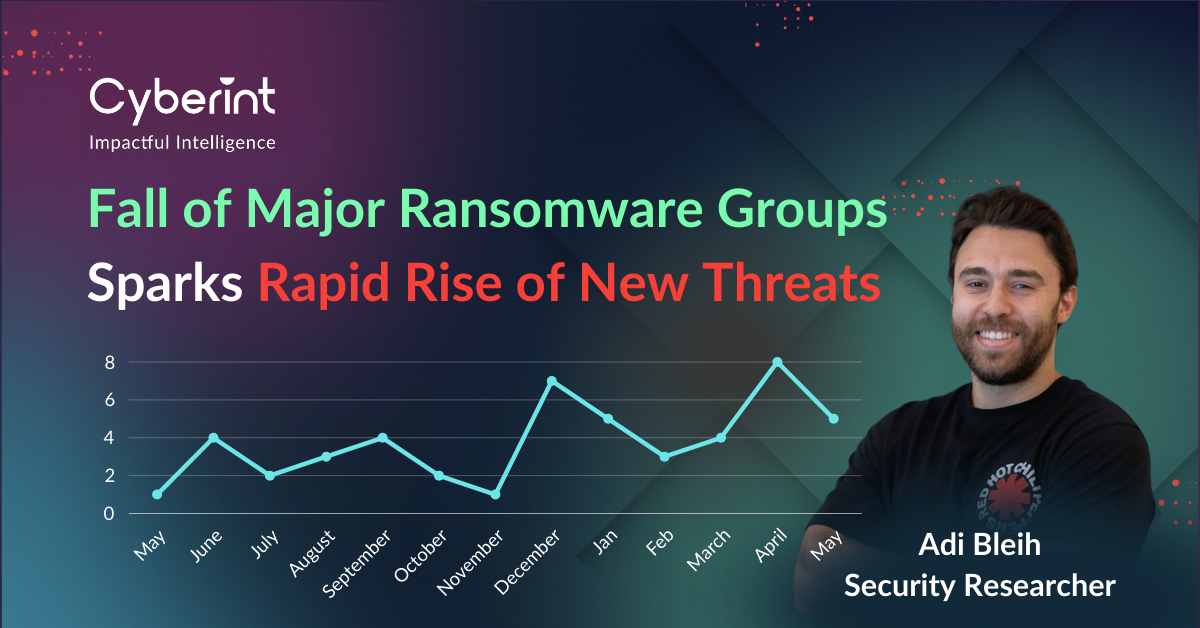
Data from leak sites revealed the emergence of at least 25 new ransomware groups in 2023, highlighting the ongoing appeal of ransomware as a lucrative criminal activity. However, despite the appearance of new groups like Toufan, Darktrace, and CryptNet, many of these threat actors disappeared during the second half of the year.
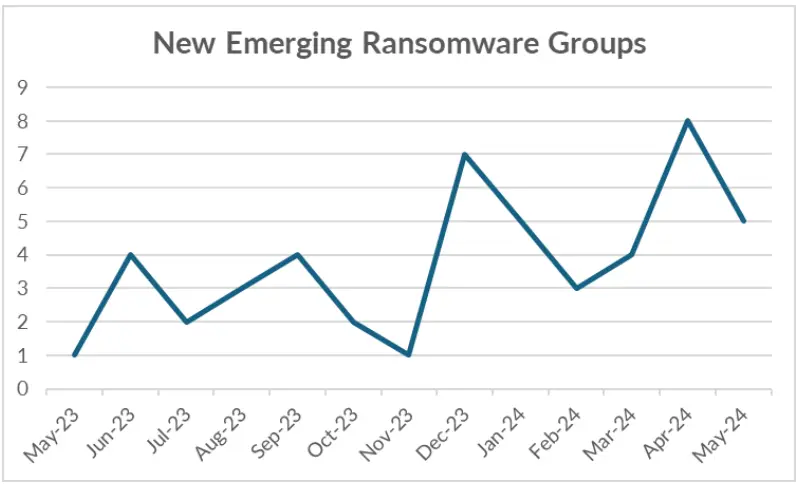
We are just in middle of the second quarter of 2024, and we’ve already seen 25 new ransomware groups that posted at least one victim on their data leak site.
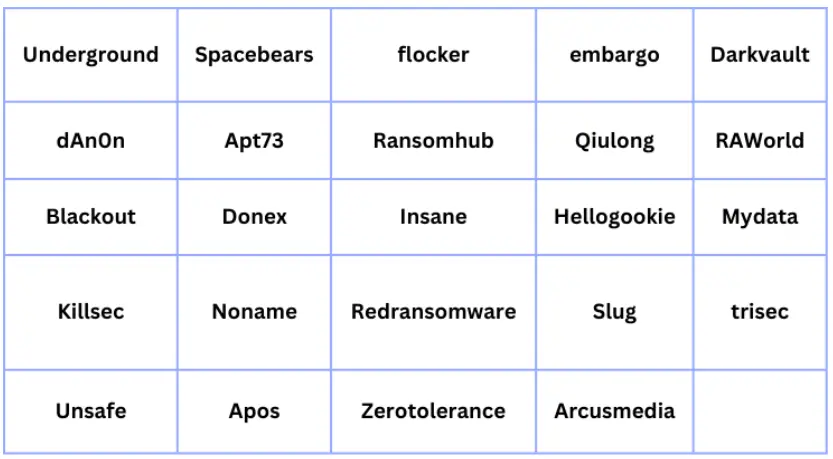
The full list:
This group surfaced at the end of April and has since posted information about 12 victims on their data leak site. Of these victims, 10 are based in the United States, with business services the primary targeted sector.
A notable observation from their data leak site is the apparent lack of emphasis on design or a visible logo, which may suggest that the group prioritizes attack methodologies over branding and has a smaller team.
In contrast to other naming conventions used by researchers to identify threat actors, this group has chosen to refer to themselves as “APT” (Advanced Persistent Threat) followed by a number, specifically APT73, which is a ransomware group modeled on LockBit. This was observed through similarities in their “Contact Us,” “How to Buy Bitcoin,” and “Web Security & Bug Bounty” pages, which closely resemble the layout of the LockBit Data Leak Site (DLS).
The content on these pages mirrors that of LockBit, indicating that this is essentially a LockBit-style Ransomware Data Leak Site (DLS). One notable difference is the “Mirrors” section, which lacks any active mirrors unlike LockBit, highlighting a level of amateurism within this group.
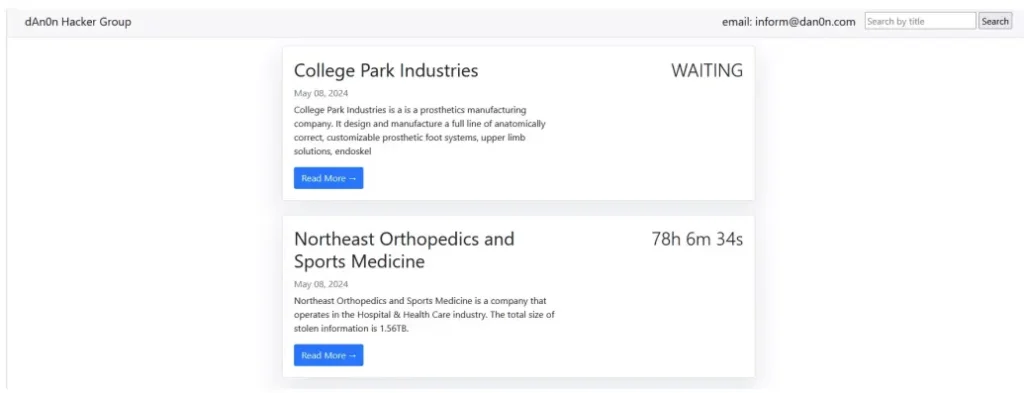
To date, the group has targeted a total of 5 victims in various locations worldwide, including Germany, Canada, the Czech Republic, and the United States (twice). Their attacks have been exclusively focused on the business services sector.

Since December 2023, a new ransomware variant known as DragonForce has been detected. It utilizes a leaked ransomware builder originally associated with the notorious LockBit ransomware group. The DragonForce ransomware group specifically targets organizations in sectors including manufacturing, technology, healthcare, finance, construction, and real estate. Their victims are located in countries including the United States, the United Kingdom, Switzerland, Argentina, and Australia.
The emergence of DragonForce ransomware, linked to the leaked builder of LockBit Black ransomware, highlights the escalating threat posed by the exploitation of leaked malware-building tools in cyberattacks. The availability of these tools allows threat actors to tailor and deploy ransomware payloads more effectively, increasing the risk for organizations worldwide. DragonForce’s use of double extortion tactics underscores the evolving strategiesemployed by ransomware actors to enhance their impact and profits.
There have been several significant operations in 2023 and 2024, focusing on prominent actors in the ransomware landscape. Following are some of the key operations:
The ongoing saga involving the BlackCat/AlphV ransomware gang took another turn as news surfaced that the group had shut down its servers following a contentious hack of an American healthcare service provider. The incident involved an affiliate allegedly receiving a substantial $22 million payment after orchestrating a data theft and ransomware attack that disrupted Change Healthcare’s services. However, the gang reportedly retrieved this paymentfrom the affiliate’s digital wallet before ceasing operations.
The closure of the gang’s servers raises questions about whether this is an exit scam or an attempt to rebrand under a different name, similar to how BlackCat emerged from the DarkSide ransomware operation. This development follows a previous crackdown by American cyber authorities in December, during which they seized several of the gang’s data leak and communications sites and provided victims with a decrypter to regain access to their encrypted data.
The attack on Change Healthcare indicates a shift in strategy by BlackCat/AlphV, especially after the December crackdown prompted the gang to remove restrictions on affiliates targeting critical infrastructure like the healthcare sector. This incident suggests that the group has rebounded from the setbacks it faced earlier in December.
Since December 2023, the number of Alphv attacks decreased significantly to 53 attacks over two months. However, starting from March 3, there have been no reported victims of Alphv attacks.
Law enforcement dismantled LockBit’s infrastructure, which included 34 servers hosting the data leak site and its copies, along with stolen victim data, cryptocurrency addresses, 1,000 decryption keys, and the affiliate panel. This operation, known as “Operation Cronos,” involved an international coalition of 10 countries and resulted in the arrests of two individuals in Poland and Ukraine, as well as the seizure of 200 cryptocurrency accounts.
Subsequently, the UK, US, and Australia revealed the identity of Dmitry Khoroshev, a Russian national and the leader of the once-notorious LockBit ransomware group, following an international disruption campaign led by the National Crime Agency (NCA). Khoroshev, also known as LockBitSupp, who previously operated anonymously, offered by the FBI a $10 million reward to uncover his identity, is now facing sanctions imposed by the FCDO in coordination with the US Department of the Treasury’s Office of Foreign Assets Control (OFAC) and the Australian Department of Foreign Affairs.
These sanctions include asset freezes and travel bans. Additionally, the US has unsealed an indictment against Khoroshev and is offering a reward of up to $10 million for information leading to his arrest or conviction.
In addition to uncovering the true identity of LockBitSupp, the Operation Cronos investigation has provided the NCA and its partners with detailed insights into LockBit’s operations and network. The National Crime Agency also disclosed that the number of LockBit affiliates was 194 until February 2024 before Operation Cronos. Since then, the assessment indicates a significant reduction in active affiliates to 69.
An international operation involving the National Crime Agency has dismantled a ransomware service used by cybercriminals to target and extort businesses globally. Led by the FBI and German law enforcement, with support from NCA cybercrime investigators, the operation resulted in the takedown of servers associated with the HIVE ransomware strain on January 26.
HIVE, available for purchase on the dark web, facilitated ransomware attacks by cybercriminals. Typically delivered via phishing emails with malicious attachments, HIVE would infect victims’ computers and encrypt their systems until a ransom was paid. Since June 2021, the HIVE ransomware group has victimized over 1,300 organizations worldwide, collecting more than $100 million in ransom payments.
The FBI developed tools to bypass HIVE encryption, and NCA cybercrime investigators assisted UK victims in mitigating the impact of the ransomware. Approximately 50 corporate victims in the UK, including in housing, haulage, commercial, and education sectors, have been affected by HIVE since its detection in April 2021.
The collaborative efforts of international law enforcement agencies in 2023 and 2024 have significantly disrupted major ransomware operations, illustrating the increasing challenges faced by cybercriminal groups. Operations targeting groups like Hive, Alphv (BlackCat), and LockBit have demonstrated the resolve of law enforcement to combat ransomware threats on a global scale.
Looking ahead, the emergence of new ransomware groups in 2024, as evidenced by the proliferation of 25 new groups by the second quarter, suggests a sustained and evolving threat landscape. These groups, such as dAn0n, APT73, and DragonForce, pose fresh challenges to cybersecurity professionals and organizations worldwide.
Despite law enforcement successes, the cyber threat landscape remains dynamic, with ransomware actors adapting their strategies and tactics. Continued vigilance, collaboration, and innovative cybersecurity measures will be essential in mitigating the impact of ransomware and other cyber threats in the future.
Cyberint, the Impactful Intelligence company, reduces risk by helping organizations detect and mitigate external cyber threats before they have an adverse impact. The Cyberint Argos platform’s patented technology provides superior visibility through continuous discovery of the evolving attack surface, combined with the automated collection and analysis of vast quantities of intelligence from across the open, deep and dark web. A team of global military-grade cybersecurity experts work alongside customers to rapidly detect, investigate, and disrupt relevant threats – before they have the chance to develop into major incidents.
Global customers, including Fortune 500 leaders across all major market verticals, rely on Cyberint to protect themselves from an array of external risks, including vulnerabilities, misconfigurations, phishing, impersonation attacks, malware infections, exposed credentials, data leaks, fraud, and 3rd party risks.

Fill in your business email to start.
©1994–2026 Check Point Software Technologies Ltd. All rights reserved.
Copyright | Privacy Policy | Cookie Settings | Get the Latest News
Fill in your business email to start


