


On January 15th, the FSOCIETY ransomware group published on their official DLS (data leak site) that they have begun a partnership with the rising Funksec group.
The FunkSec ransomware group first emerged publicly in late 2024 and rapidly gained prominence by publishing over 85 claimed victims—more than any other ransomware group in the month of December. Presenting itself as a new Ransomware-as-a-Service (RaaS) operation, FunkSec appears to have no known connections to previously identified ransomware gangs, and little information is currently available about its origins or operations.
FunkSec’s data leaks often recycle information from previous hacktivist campaigns, casting doubt on the authenticity of their claims. Despite these limitations, their Tor-based operations and low ransom demands have drawn widespread attention in cybercrime forums. Learn more about them on the Check Point blog.
Flocker ransomware is a relatively new ransomware strain, first identified in April 2024. It operates as ransomware-as-a-service (RaaS), which allows cybercriminals to leverage its capabilities without needing extensive technical knowledge. Developed by the group known as FSociety, Flocker utilizes advanced encryption techniques to lock victims’ data, demanding ransoms to release access. This strain is linked to double extortion tactics, where attackers threaten to leak sensitive data in addition to encrypting it. In addition, the group manages a Telegram group and an Onion site – their official DLS.
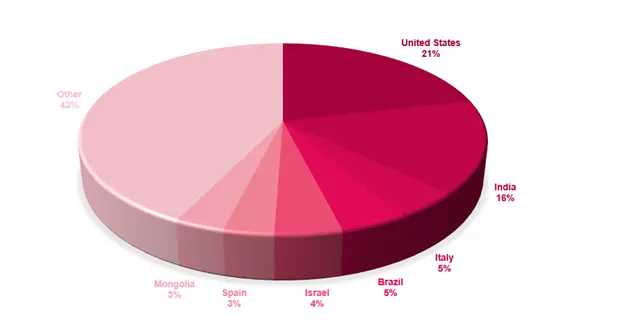
As Check Point published last week, the main country that Funksec targets is the United States as seen in the figure below. Moreover, India is also a main target of the group with double digit attacks in December only.
The most targeted sectors are currently the Business Services and Retail sectors, with over 30% of their total attacks since the beginning of Funksec’s operations.
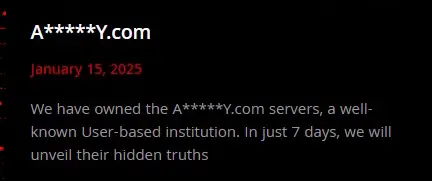
FSOCIETY is a bit different, they publish their victims without their full name, and hide it from the public, as seen in the example below. As a result, it’s harder to map the victims’ countries and industries. From what we know about the 20 victims in 2024, two are from the United States, one from Canada, and another one from Taiwan. They are related to the Financial, Construction and Governmental industries.
It is not surprising that the United States is the main target of both groups. In addition, organizations from the Business Services, Retail, Governmental and Financial sectors, will probably be targeted more than others.
Collaboration between ransomware groups can significantly amplify the scale, complexity, and impact of cyberattacks, or in our case, ransomware attacks, posing a heightened threat to organizations worldwide. By pooling resources, expertise, and infrastructure, these groups can develop more sophisticated ways to execute attacks on a broader scale.
For instance, sharing advanced malware scripts, encryption algorithms, can lead to harder-to-detect and more effective ransomware attacks. This collaboration also enables faster attack cycles, as groups can leverage shared botnets, compromised networks, and initial access broker services to target victims more efficiently.
These developments underline the growing sophistication and organization within the ransomware ecosystem, elevating the risks for potential victims. As collaboration among threat actors becomes more prevalent, organizations must adopt proactive cybersecurity measures, strengthen threat intelligence sharing, and foster international cooperation to address this evolving menace effectively. The emergence of such alliances highlights the urgent need for a coordinated and robust defense against the increasingly organized and resourceful ransomware landscape.
Cyberint, now a Check Point company, reduces risk by helping organizations detect and mitigate external cyber threats before they have an adverse impact. The Check Point External Risk Management solution provides superior visibility through continuous discovery of the evolving attack surface, combined with the automated collection and analysis of vast quantities of intelligence from across the open, deep and dark web.
A team of global military-grade cybersecurity experts work alongside customers to rapidly detect, investigate, and disrupt relevant threats – before they have the chance to develop into major incidents. Global customers, including Fortune 500 leaders across all major market verticals, rely on Check Point External Risk Management to protect themselves from an array of external risks, including vulnerabilities,
misconfigurations, phishing, impersonation attacks, malware infections, exposed credentials, data leaks, fraud, and 3rd party risks.

©1994–2026 Check Point Software Technologies Ltd. All rights reserved.
Copyright | Privacy Policy | Cookie Settings | Get the Latest News
Fill in your business email to start


