


For both white-hat and black-hat operators, the infamous “RockYou” lists have been a staple of the cyber-security landscape for well over a decade. They are lists of passwords, compiled and repeatedly expanded upon with data leaked over the years to form, in its most recent iteration, a list of approximately 10 billion plain-text passwords. (supposedly… but we’ll get to that…)
This most recent incarnation of the “RockYou” lists, dubbed “rockyou2024.txt”, has been uploaded to a cybercrime-related forum by a user named “ObamaCare” on July 4th, and has since been “making the rounds” in various other forums and telegram channels, drawing attention from media and security vendors.
In this post we will review and discuss this most recent “rockyou” development.
“ObamaCare” has been active in the aforementioned forum since May 29th, with 4 previous “data dump” postings to his name prior to his posting of “rockyou2024”.
Other than this – not much else is currently known regarding “ObamaCare”.
One use for such a list, albeit wildly impractical, is for “credential-stuffing” type attacks for login purposes. This is impractical for several reasons – one of which is the numerous protection mechanisms prevalent, such as rate limiting and multiple attempts limiting, intended to prevent just that. Another is the sheer size of such a list… for simplicity’s sake, let’s assume a single threaded approach, 100ms of network latency and 50ms of server response time, and do some quick math:
Converting to minutes:
To hours:
To days:
To years:
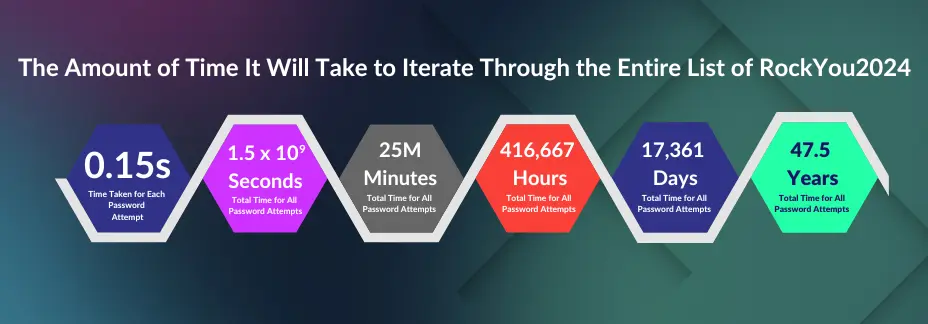
That’s right… assuming the above, it would take approximately 47.5 years to iterate through the entire list.
However, there are also additional, more probable, uses for such data – one could also use such a list for the purposes of password hash-cracking.
This is where a list like this could very well be useful. Assuming availability of hardware in the performance range of something like an RTX 3090 to be used for the computation, one could compute approximately 10 billion NTLM hashes (which are used to store windows passwords) in under 30 seconds. This time would, of course, increase with the complexity of the hashing algorithm, but even for relatively tough implementation of bcrypt it would only result in several days of computation.
After the “shock” of the initial announcement wears off, and we examine the file, we can see the extremely low quality of the data. “rockyou2024.txt”, while enormous (~150GB decompressed), is absolutely full of what can only be described as unusable junk data. This ranges from entries which are either too short or too long to be an actual password, entries that contain non-standard characters and symbols, various types of unsolved hashes, entries with large heading or trailing whitespaces, etc’.
So much “junk data”, in fact, that if we trim off most of the entries mentioned above, we will be left with between 1 and 1.5 billion “useable” entries. A size reduction equating to between 85 and 90 percent. Not so scary now, is it?
Leaks, compilations and “re-hashes” of previous dumps are nothing new and are not going to disappear. The Cyberint Research Team tracks this on a regular basis. However, it is important to distinguish between such incidents that contain high quality data, and others that are basically junk.
While it’s true that “10 billion leaked passwords” sounds initially scary, after examining the data itself, this incident is more along the lines of:

We encourage you to use strong passwords, replace them periodically and implement password management policies and a password manager in your day to day work.

Fill in your business email to start.
©1994–2026 Check Point Software Technologies Ltd. All rights reserved.
Copyright | Privacy Policy | Cookie Settings | Get the Latest News
Fill in your business email to start


