


Amid the disruption of the Hive ransomware group by law enforcement agencies, Hunters International emerged onto the cyber scene in Q3 of 2023, displaying notable technical similarities with Hive, hinting at an evolutionary progression or branch-off from the dismantled group.
This transition underscores the adaptive nature of cybercriminal networks, persisting in their illicit activities despite law enforcement actions. The inception and modus operandi of Hunters International underscore an ongoing threat in the realm of cyber extortion and data breaches.
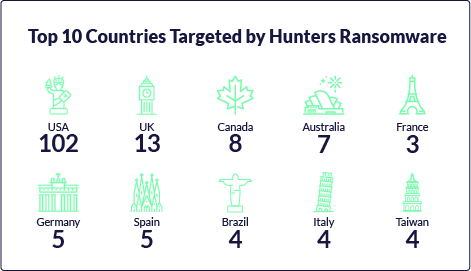
Hunters International has demonstrated a widespread targeting strategy across various industries worldwide, showing a global presence with a strategic emphasis on maximizing ransom potential and impact. Their victims range from healthcare, automotive, and manufacturing to logistics, financial, educational, and food sectors, indicating an indiscriminate approach to exploiting any susceptible entity. Their extensive targeting, spanning across regions like the United States, Europe, Canada, Brazil, New Zealand, and Japan, illustrates their indiscriminate approach, targeting entities vulnerable to cyber attacks or those likely to succumb to extortion pressure.
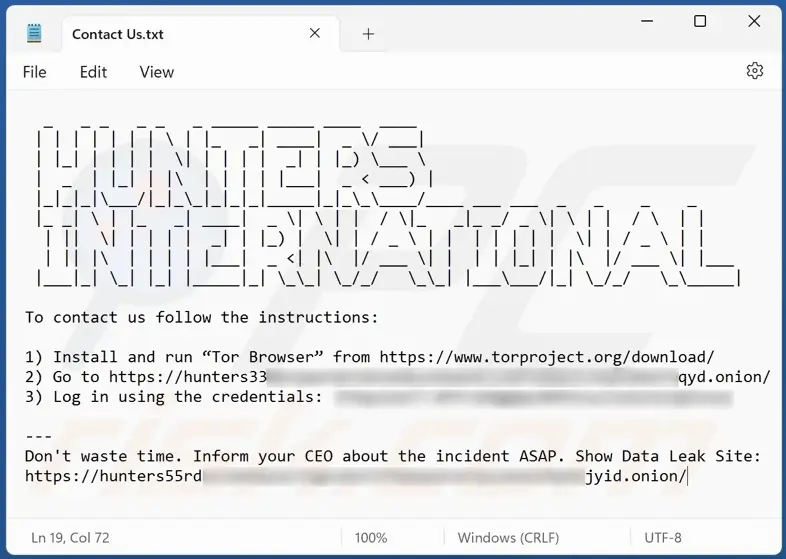
The ransom note is dropped in each encrypted folder on the system and automatically opened at the end of the encryption process.
This group doesn’t discriminate when it comes to choosing targets. Whether it’s an energy provider, a hospital, a school, or even a zoo, they’re all potential victims. The group appears driven by profit, focusing on those lacking robust cybersecurity defenses or under intense pressure to pay a ransom if their data were compromised.
This broad range of victims highlights the group’s opportunistic strategy and ability to infiltrate diverse sectors, making it a serious threat to organizations worldwide. Given their focus on financial gain, such a diverse target list is typical, especially for groups operating under the RaaS model.
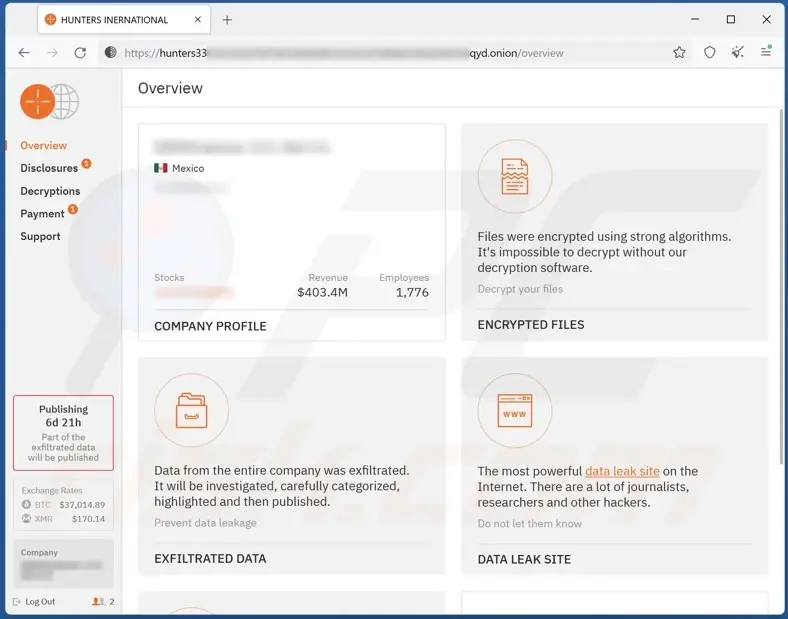

Subsequent investigations into Hunters International have revealed potential ties to Nigeria through domain registrations and associated email addresses, with the group unveiling a non-dark web version of their leak site under the same name on January 22, 2024. Researchers noted the group’s revival of a dormant website from 2021, employing deceptive tactics to obscure their true identity, potentially indicating sophisticated maneuvering. The blend of genuine and fabricated identities underscores the complexity and cunning of groups like Hunters International, highlighting the challenges in attributing cybercrimes and their global operational reach. The impact of their ransomware attacks manifests in significant data breaches, financial losses, and reputational harm to targeted organizations, emphasizing the necessity for proactive cybersecurity measures, including regular data backups, employee training on phishing detection, and robust security frameworks.
The Hunters International ransomware group is targeting IT professionals with a new C# remote access trojan (RAT) named SharpRhino, designed to infiltrate corporate networks. The malware is distributed as a digitally signed installer, which then modifies the Windows registry for persistence and executes PowerShell commands to deploy ransomware. SharpRhino uses stealthy tactics, including the creation of specific directories for command and control (C2) communication and the abuse of legitimate Microsoft binaries. The group is also creating fake websites to impersonate open-source network scanning tools, aiming to exploit accounts with elevated privileges.
Hunters International’s techniques and ransomware strains exhibit substantial parallels with those of the Hive ransomware group, suggesting a shared lineage or potential transfer of technology. This connection implies that Hunters International may have inherited or adapted encryption methods and operational tactics from Hive, indicating a continuation or evolution of their strategies.
The data leak site also features a News page, with the most recent post dated April 24, 2024, including a link to a public domain site. This public site mirrors the data leak site but is accessible from any standard web browser. The domain is registered in Russia under a false identity through the NiceNIC domain service. The individual listed, Mihail Kolesnikov, is associated with over 400 domains.
| Tactics | Techniques |
|---|---|
| Discovery | T1057 – Process Discovery |
| Defense Evasion | T1027 – Obfuscated Files or Information |
| Discovery | T1082 – System Information Discovery |
| Command and Control | T1071 – Application Layer Protocol |
| Privilege Escalation | T1547 – Boot or Logon Autostart Execution |
| Persistence | T1547 – Boot or Logon Autostart Execution |
| Defense Evasion | T1562 – Impair Defenses |
| Discovery | T1083 – File and Directory Discovery |
| Command and Control | T1071.001 – Web Protocols |
| Impact | T1486 – Data Encrypted for Impact |
| Execution | T1129 – Shared Modules |
| Defense Evasion | T1575 – Native API |
| Execution | T1575 – Native API |

Fill in your business email to start.
©1994–2025 Check Point Software Technologies Ltd. All rights reserved.
Copyright | Privacy Policy | Cookie Settings | Get the Latest News
Fill in your business email to start


