


Highly motivated, problem solver, dot connector, energetic multi-dimensional & professional management with commercially oriented, customer service skills & PMO abilities in high-growth, fast-paced organizations.
Over the past months, Cyberint Research Team observed a new group that emerged on several underground forums. What seemed to be “yet another info stealer seller” has turned out to be something far more interesting. As the group is named Jester Stealer, that were, at first, selling a fairly sophisticated info stealer (Figure 1). Other evidence suggests that there is much more to it.

Cyberint Research Team discovered a developing threat group that gets their claws into whatever they can find. With a botnet named Lilith, a miner named Trinity, a clipper named Merlynn, and an exploit builder, it seems that the new group is putting its best efforts into establishing a major foothold in the cybercrime industry.
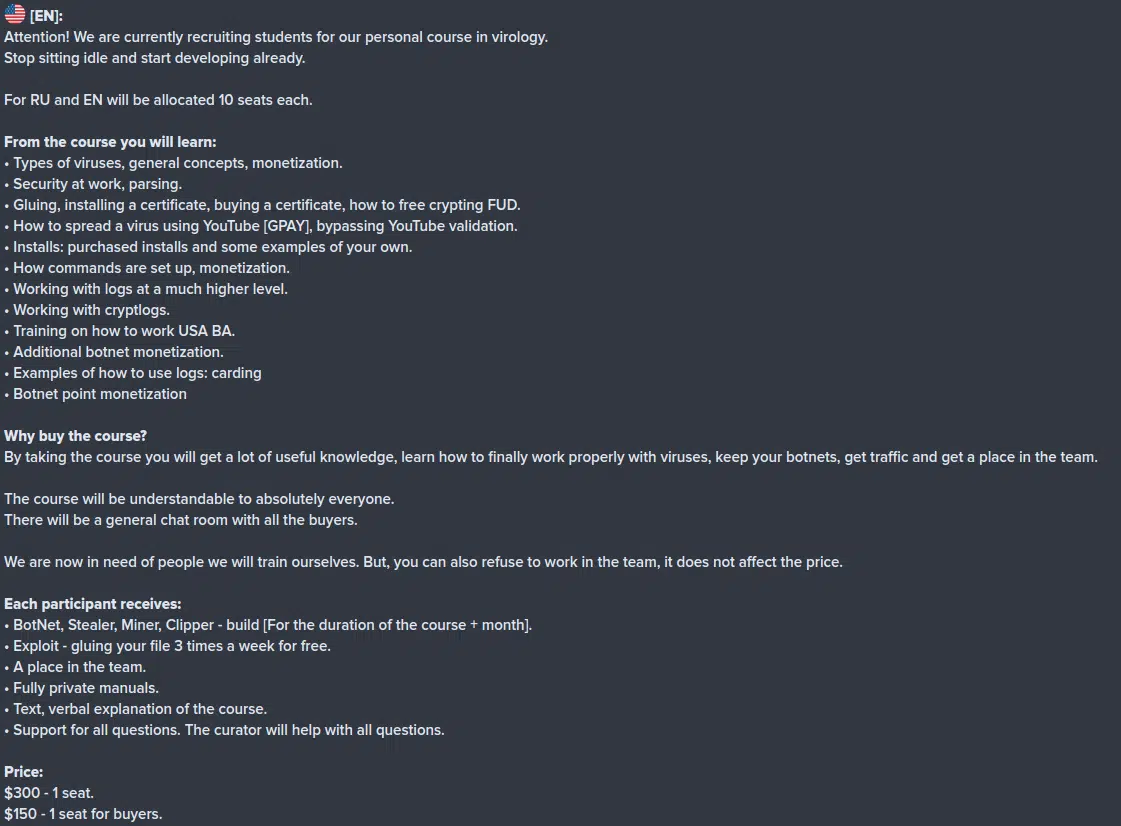
The Russian-speaking group tries to recruit and train new members into their ranks (Figure 2), offering a course for $150-300 depending on whether the student is already a client or not.
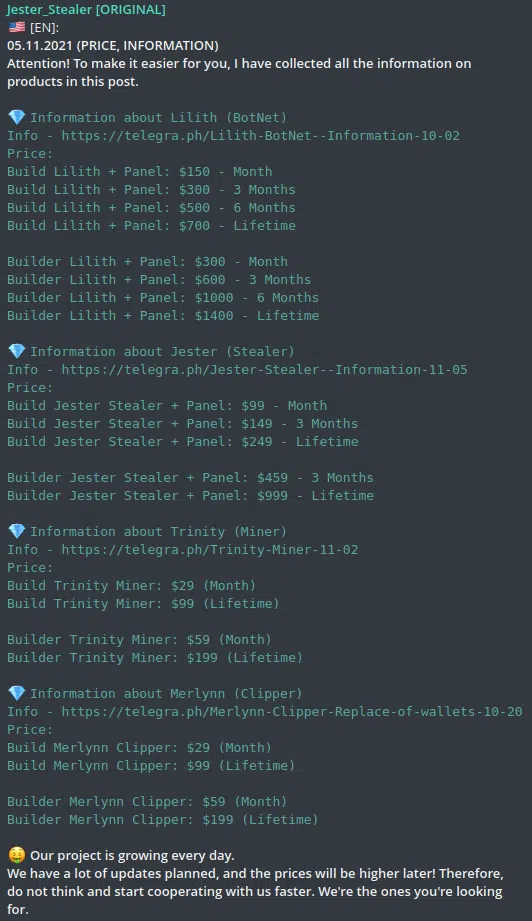
The prices for Jester’s products vary between $35 and $2000 depending on the product and the duration of the subscription.
First observed in July 2021, Jester Stealer, the flagship of the group, is gaining popularity via massive advertising efforts, lifetime support given by the group, and fairly good buyer reviews.
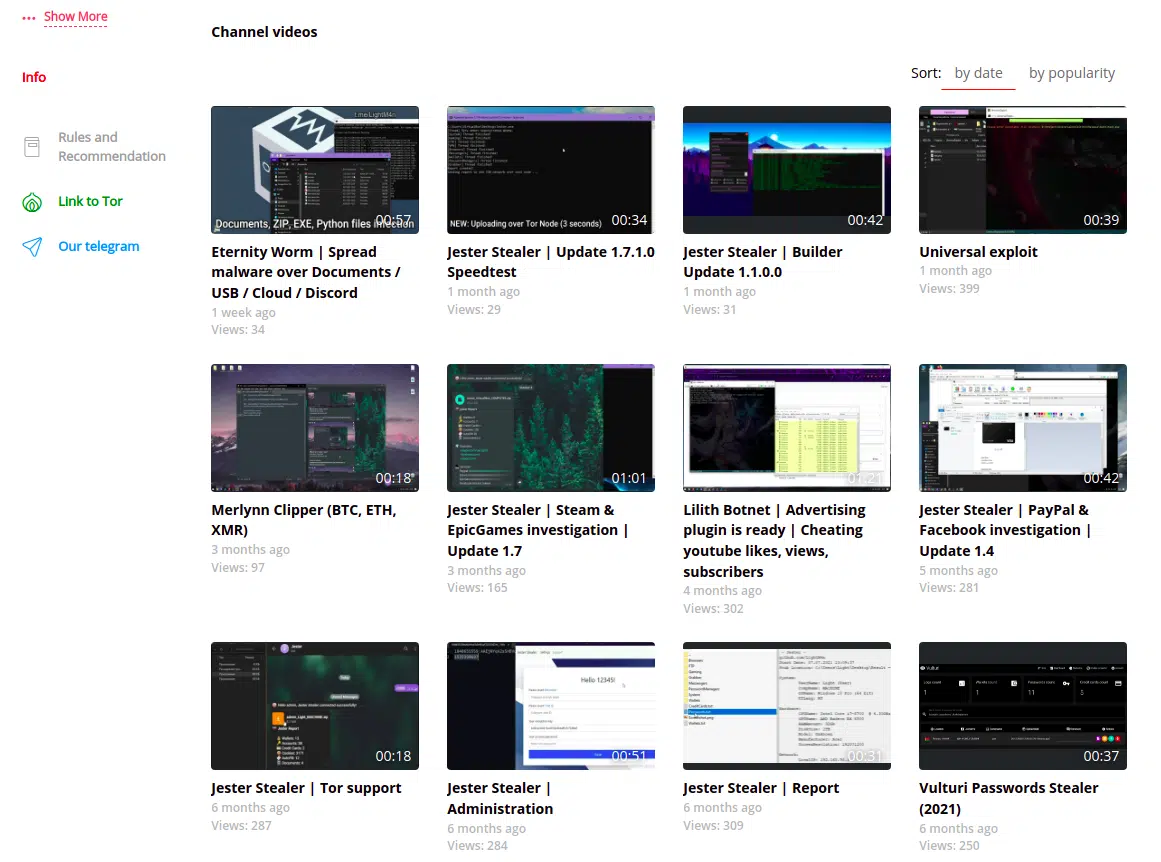
As new info stealer developers are constantly trying to gain entry into the industry, Jester Stealer makes a major effort to demonstrate how “unique and premium” their product is compared to others, and creates highly detailed and appealing landing pages. They offer direct channels to the developers for “custom made” abilities, and have launched a “demo presentation” channel (Figure 3) on an underground video sharing platform, where they demonstrate each of their products.
As mentioned, they have also created a training program, both in Russian and English, as an “opportunity” to join their team.
We also found large advertisements using Argos Edge in underground and darknet forums (Figure 4).
All these ad campaigns lead to the main telegram channel they currently operate, which is used to communicate with buyers regarding new updates and patch notes, while also, of course, advertising all of their products, not only Jester Stealer (Figure 5).
This Telegram channel often offers a platform for new buyers to both communicate with the developers in order to buy or ask questions about the product, and directs to a reviews channel they operate as well.
While other info-stealers threat groups look to put their focus on one product, this new, fairly ambitious, group comes with the sole purpose of creating a real game-changer and setting a new standard and introducing a whole ecosystem for threat actors looking to get into the game.
The Jester Stealer group’s second-biggest project is the Lilith Botnet (Figure 6). This botnet has a variety of plugins offered as part of its operation and may fulfill many purposes. The goal of this tool is to serve a variety of threat actors who seek to use this infrastructure to generate traffic, DDoS attacks, malware deployment, and more.
The base price is $150, up to $1400, paid in BTC, XMR or USDT.
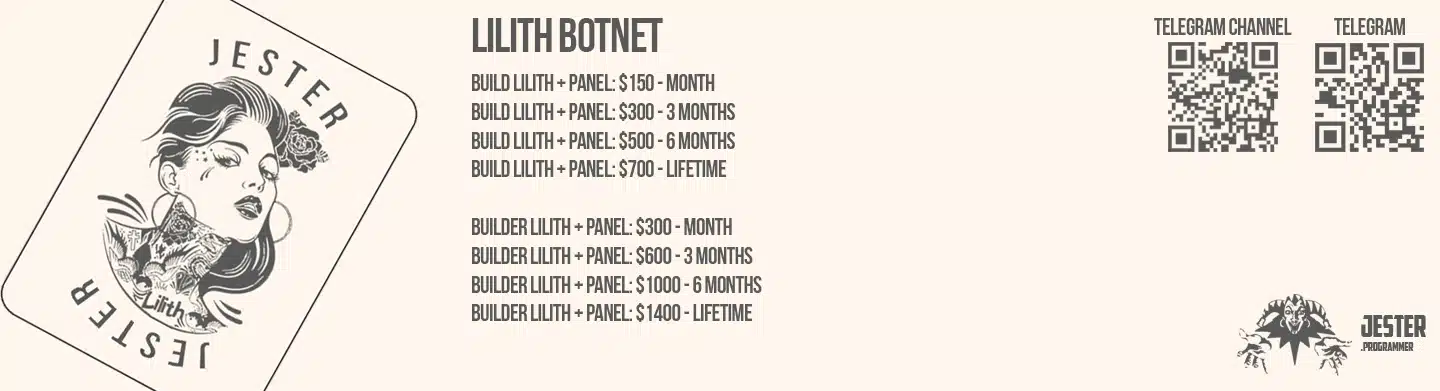
Currently, the following plugins are available when using this botnet:
Advertising Plugin
Generating likes, subscriptions, views for videos and streams on social media networks and YouTube.
BotKiller Plugin
Lilith will purify any pre-infected machine it is taking over, and clears any other malware on the machine.
Clipper Plugin
Lilith already stores Merlynn Clipper’s abilities in its arsenal but can also operate other clippers if the buyer desires to do so.
DDoS Plugin
As with all botnets, here Lilith is no different and can initiate a DDoS attack on a given site or server using methods such as:
Dropper Plugin
Destined to be a commonly used platform for any type of malware, including ransomware, Lilith offers the ability to deploy, download and execute and malware on bots in its possession.
Mining Plugin
Just like the Clipper, Lilith already has the Trinity Miner that the group has developed in its arsenal, but can also operate other miners if the buyer wishes.
Stealer Plugin
Lilith has perfect synergy with Jester Stealer, and even has some of its functions if credentials stealing abilities are already stored.
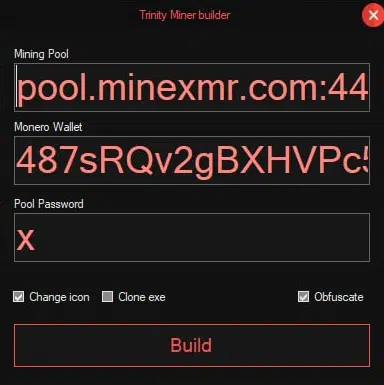
The Trinity Miner is, as mentioned, also one of the group’s products. Although it seems to be using fairly sophisticated techniques in order to work without any setbacks such as injecting itself into the process explorer.exe, gaining persistence and restart protection at the price of 29$ up to 199$, not much evidence was found suggesting it is better than other low key miners. Furthermore, it only supports mining Monero (Figure 7), which might not be desired by all threat actors.
Clipper software is designed to monitor the clipboard and replace other people’s crypto wallets with the threat actor’s address.
Merlynn is no different than most clippers at its core, but it is more agile, consistent and anonymous than others. Like Trinity Miner, its price also ranges between $29 and $199. It supports communication with the threat actor’s Telegram bot, integration with all major wallets, adding itself to the Windows startup and instant substitution of clipboard addresses.
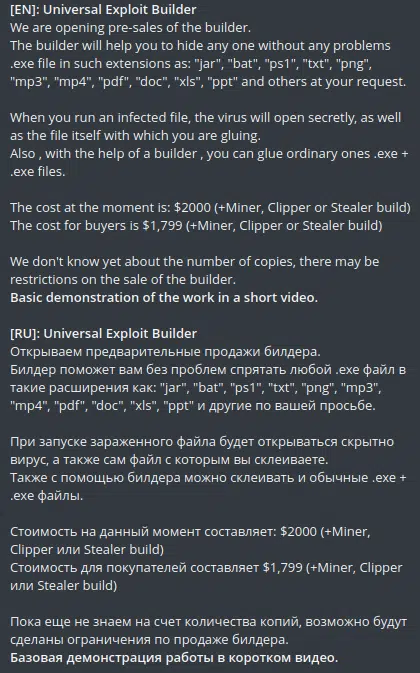
In their quest to become a valuable and popular franchise within the cybercrime industry, the Jester Stealer group is always looking for new ways to expand and add more products to their shelves. The group has published in their official Telegram channel (Figure 8) that their next product is an exploit builder. They have already initiated presale for early adopters and claim that this exploit builder should be able to masquerade any file type and run it silently.
It seems that the price of this exploit builder should be $1799, or $2000 for those who don’t own Jester Stealer.
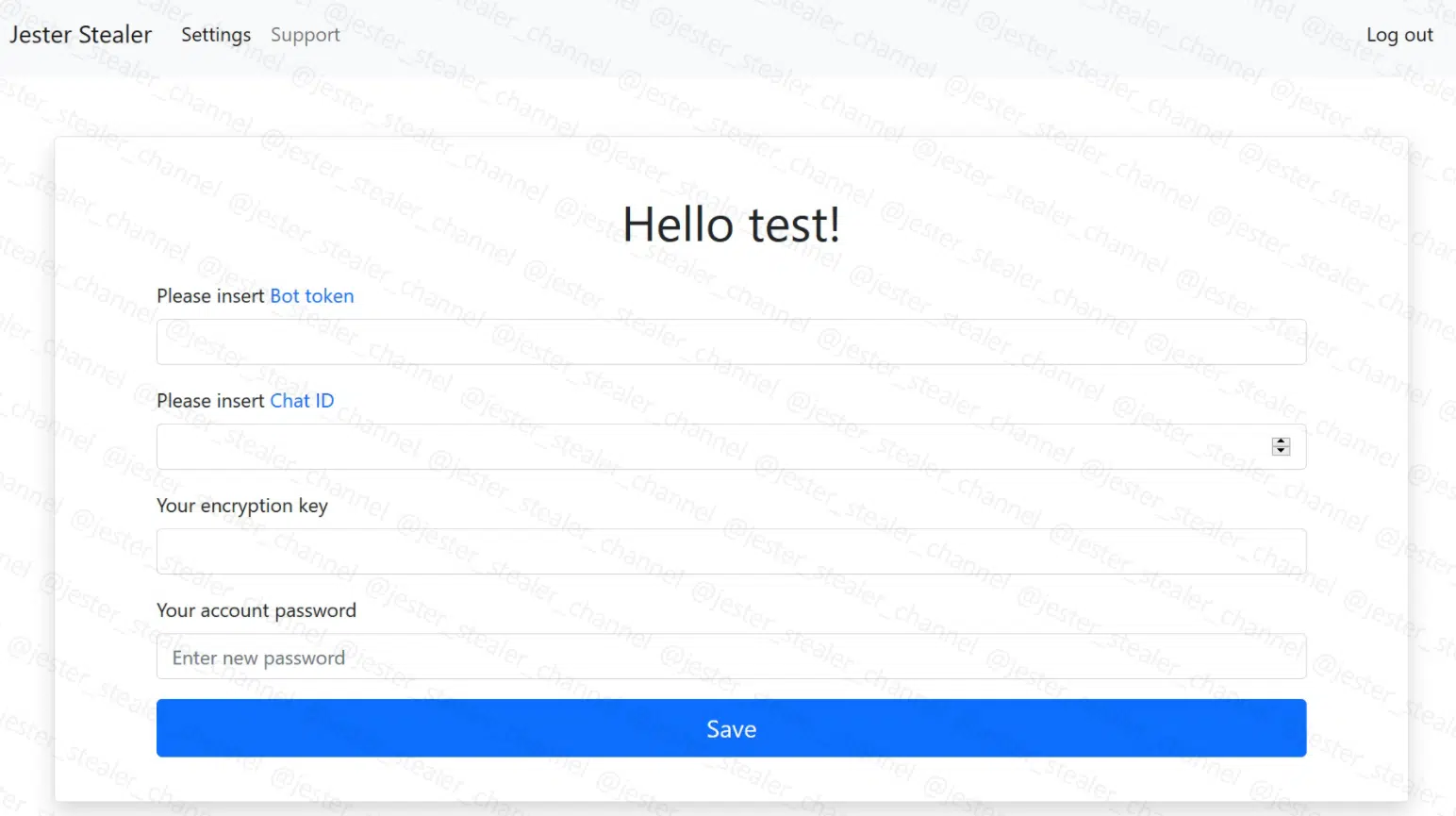
Jester Stealer’s dashboard takes many forms. The group has built several ways to store, parse and show buyers the obtained logs.
The default dashboard is a “.onion” site, which is the first “go-to” address to upload the stealer’s findings, although this is merely part of the chain. Each buyer gets an interface on the onion page in which Telegram channel details should be filled in (Figure 9).
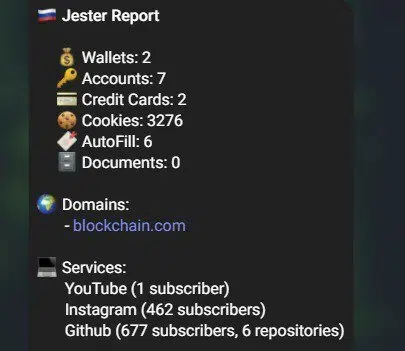
The Jester Stealer is the crown jewel. While it is more focused on operating in the areas of credit cards and cryptocurrency wallet theft, the developers did not neglect other “treasures” such as browser information, password managers, VPN clients, FTP clients, system credentials and more (Figure 10).

What differs Jester Stealer from other traditional stealers is its communication and data exfiltration through the Tor onion website and easy integration with the threat actor’s Telegram bot.
Jester Stealer’s business model is Malware-as-a-Service (MaaS) based, which means that threat actors pay for a subscription that changes from 1 month to a lifetime, depending on the price, which varies between $99 and $999 (Figure 11).
It seems that most of the early adopters of this stealer are looking for personal gain and are targeting more crypto-related assets such as wallets, tokens and NFTs rather than Redline or Raccoon threat actors who mostly look to resell the findings.
While Jester Stealer developers placed an emphasis on marketing, reliability and variety of other products, they do not support any delivery methods and leave it to the buyers to handle this.
As is common with threats of this nature, evidence suggests that threat actors often use email lures masquerading as legitimate business communications that encourage the recipient to open an attachment. When targeting organizations members, recipients targeted will likely include those working within Business Administration, Finance and Sales teams. Furthermore, the compromise of one organization could lead to legitimate email accounts being abused to send convincing lures to other organizations, such as their customers, partners and suppliers.
Although malspam is a fairly popular technique, we have seen several cases where threat actors spread Jester Stealer in forums, and mostly Discord channels with gaming or cryptocurrency content. Currently, spreading the stealer in Discord channels is the most common technique we have observed.
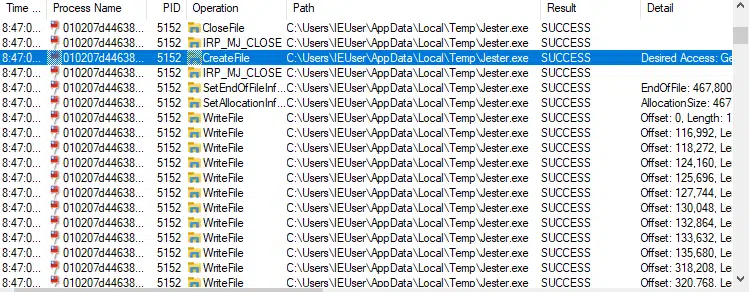
Having lured the victim into opening the malicious email or Discord channel attachment, which most of the time is an executable file, mostly a loader the threat actors purchased separately, it dynamically loads the Jester Stealer payload into the %TEMP% directory (Figure 12) and executes it. Once the Jester Stealer executable runs, the loader deletes itself.
As mentioned, Jester Stealer uses Tor proxies to exfiltrate the stolen data. One of its first steps is to download a zipped Tor client custom module from GitHub repository (Figure 13), which belongs to the group. The Tor client is also downloaded into the %TEMP% directory.
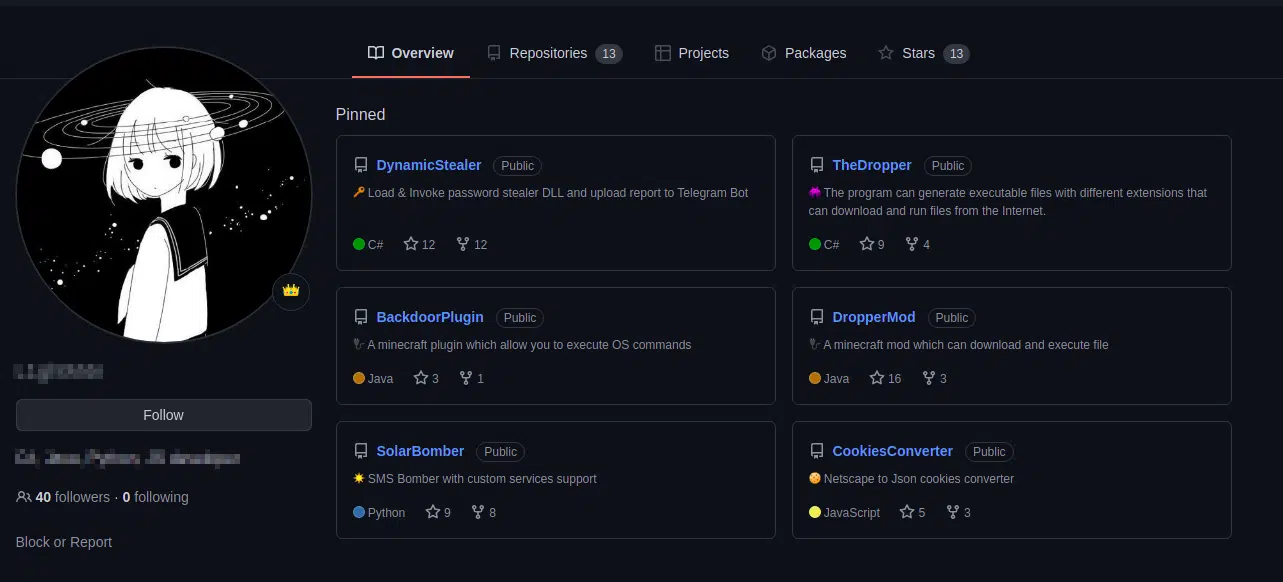
While this GitHub repository is a crucial stage in the first steps of the stealer, it seems that other repositories are stored there that might be used in the group’s other tools and products.
Utilizing the same working directory as the dependency download phase, in the %TEMP%, Jester Stealer stores all acquired data in preparation for data exfiltration, including credentials from a variety of chat, email, FTP and web-browsing applications, as well as cryptocurrency wallets, a desktop screenshot and details of the system configuration.
Upon the completion of the data theft stage, Jester Stealer creates a compressed Zip archive containing all of this stolen data (Figure 14), and names it the threat actor’s username, the victim’s machine user and the victim’s machine name, all separated by underscores as follows:
<THREAT ACTOR USERNAME>_<VICTIM USERNAME>_<VICTIM MACHINE NAME>.zip
As the vast majority of the modern info stealers often look to exfiltrate the stolen data to fairly classic C2 infrastructures, Jester offers better anonymity and several extraction channels that the threat actor can use.
The default C2 connectivity provided to Jester Stealer’s buyers is via the Tor site hxxp[:]//jesterdcuxzbey4xvlwwheoecpltru5be2mzuk4w7a7nrhckdjjhrbyd[.]onion.
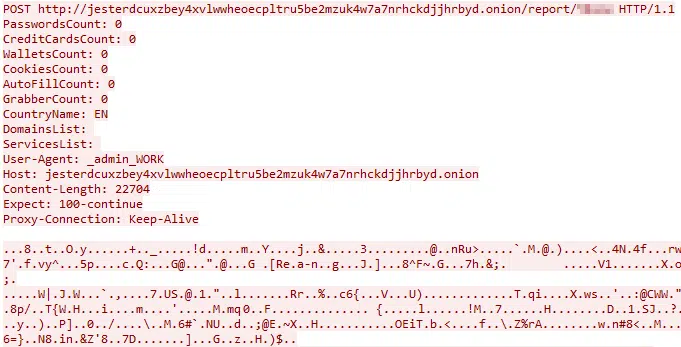
Jester Stealer sends its findings via an HTTP POST request containing the findings zip file, along with a summary contained in the headers (Figure 15).
The onion page is a node in the chain that receives the stolen data from the stealer and sends it to a Telegram bot (Figure 16) the threat actor has provided. This additional hop assures the threat actor even more anonymity.
In addition to this infrastructure, Jester Stealer is also capable of having a fallback data exfiltration technique. Each threat actor can config an anonfile, an anonymous file-sharing platform, account that the stealer will send the stolen data to in case the first option did not work properly.
The following hashes are provided for reference., Given the ongoing nature of these campaigns, it is likely that the threat actor will utilize methods to avoid detection such as packing and crypting, resulting in differing cryptographic hashes. Furthermore, as the group keeps making efforts to expand, we might see more onion pages and more fallbacks for data exfiltration.
010207d4463874eabd3808b12355e24acab67ff55c93c075625c2a05e481fd3163c6a046117b72d93b4e7080112efeef75a56c70fc739337a0e58a24bc9b483c6c696dfabef6726c984759bbd8ea68c048bf2a8efd056597bcbe0b179c3a9d89e038cd85c9da66e9517bba1e3af819a7cb1cf068fe955b8e125273d1e0533c2bcfa4a0acd6953e845c6dc4e7d66f1acd487c24814689a575190642c2be76852de9c0a925edadcabd11f20a9c44912b1f4be987998208d16a728fef8c3d0792d232c5f9a900171b2a12fa07e8bcccb91cb45433b59e34ba691bf6d3ba239c426869e395e78e1ad069f22269e0d3618706d95f174d6af411bec70e1e315308aff4ecd4609a880cb82fce449a7d8e5919c7f2786f5918f6aa5d8a29438f4393547d3168f18432106cfaf21f48598c1b26b1026de7a0bac69ae548c79dec67be7853cdbed3a79d37d581fc5be268df61e13aaafa5c88a001f4e8b298d77c4b37ae136dd7f4652faa45c4e124cdeb6582262b8572f5ed8bd7fbdb2967ee5dce01d8e0a4a81d6a903411ebca75c1f2d85f6db8ef65cd6e4e5fdbaa9b8fafc093d4297083315459c10621aa4965545a36ec5fb0b803ec0dcd5a1fa3b3a2266db9165714ee5e8737168f71747990cce9802470c6d9d484ebd51225fd972408f4909c92fc28b7bab024147403bc3988850009c6e5120686292c8927056b521bb9b0cc0337ecb44ba0a108abc5f5c4d6e22fcd46e6d9608f7b72ea0fe603f2f0918b542937ceb1a94e9366a84f75948fbe56576945abeb7b2ecb578b00aeaa22b7896bf6fba679ee3c33f24010f2b794bb76e0f4b11bbca6c4f87240820e308ea1d5b442cfb61663582da089a5ba37ad833149864a99ce60d8f2d9106d02aa26baa7b14106When posting the stolen credentials to the onion site, Jester Stealer often summarizes its findings in the HTTP POST request’s headers as each header represented the content it looked for, following the count of what it found. The following HTTP headers indicate Jester Stealer’s connectivity:
PasswordCountCreditCardsCountWalletsCountCookiesCountAutofillCountGrabberCountCountryNameDomainsListServicesListhxxp[:]//host-file-host-3[.]com/files/2737_1638475151_5837.exehxxp[:]//host-file-host-3[.]com/files/5976_1638523846_7576.exehxxp[:]//data-host-coin-8[.]com/files/5304_1642027539_6274.exehxxps[:]//transfer[.]sh/get/HhNAjU/jes.exehxxp[:]//92.38.240.149/33442.exehxxps[:]//github[.]com/L1ghtM4n/TorProxy/raw/main/LIB/Tor.zipjesterdcuxzbey4xvlwwheoecpltru5be2mzuk4w7a7nrhckdjjhrbyd[.]onion92.38.240.149©1994–2025 Check Point Software Technologies Ltd. All rights reserved.
Copyright | Privacy Policy | Cookie Settings | Get the Latest News
Fill in your business email to start


