


MEOW ransomware is a significant cyber threat known for its disruptive activities. Unlike the infamous Conti ransomware, MEOW is a modified version that retains many of Conti’s core functionalities and encryption techniques.
In late 2022, four ransomware strains derived from Conti’s leaked code were discovered, with MEOW being one of them. This crypto-ransomware operated from late August to mid-September 2022 and continued until February 2023. In March 2023, a free decryptor for MEOW ransomware was released, leading to its cessation. Operating under names like MeowCorp, MeowLeaks, or just Meow, it used the ChaCha20 algorithm to encrypt data on compromised servers. Victims were instructed to contact the extortionists via email or Telegram to pay the ransom and recover their files.
In 2024, the group’s operations underwent a significant shift, executing over 80 successful attacks worldwide. The actual number of victims is likely higher, as only those who refuse to pay the ransom are exposed on their data leak site.
From July to September 2024, the group posted 68 victims on their data leak site, which accounts for 85% of all their attacks in 2024. This shows us that the ‘meow train’ is gaining speed.
Meow ransomware’s shift to its new model involves a transition from traditional encryption-based extortion to data theft and resale as the primary tactic. Originally, like most ransomware operations, Meow encrypted victims’ files and demanded payment for decryption. Victims received a ransom note and were instructed to contact the attackers through email or Telegram.
However, the group’s recent activities have demonstrated a move toward data extortion without encryption. Instead of simply locking files, the attackers now focus on stealing sensitive data and then threatening to sell it if the ransom is not paid. This shift in tactics allows them to still pressure victims without having to rely solely on ransom payments for decryption. By selling the stolen data to third parties, often at prices ranging from $2,999 to $60,000, they can generate profits even if victims refuse to engage.
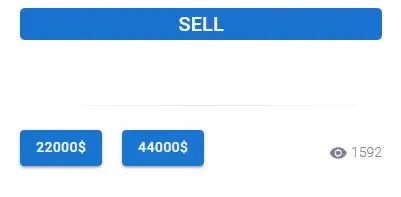
As seen in the picture above (taken from their DLS), the price from the right – $44,000, is to buy the entire data in one hand. The price on the left side – $22,000, is to buy the data in several hands.
On July 24, 2024, the group opened an account in the famous Russian hacking forum “Exploit.in”, where they mentioned that they don’t deal with ransomware, and a general description on their leak site.
The user was banned a few days later by the forum admins.
The United States is the primary target of the MEOW ransomware gang. Other affected countries include Japan, Sweden, Taiwan, Brazil, Norway, Australia, New Zealand, Morocco, Nigeria, the UK, Italy, and Canada.
The Business services sector is the most targeted one, followed by Retail, Manufacturing, and the governmental sectors.
Their data leak site presence displays a roster of victims, but only those who haven’t paid the ransom are shown. In addition, they attached samples of the stolen data with a full description on what the data includes.

MEOW ransomware encrypts a wide range of files, appending the “.MEOW” extension and making them inaccessible to users. It leaves a ransom note named “readme.txt,” a typical tactic to communicate ransom demands. Stemming from the NB65 ransomware lineage, MEOW is a formidable threat. It encrypts files using a hybrid encryption scheme that combines ChaCha20 and RSA-4096 algorithms, making decryption without the private key nearly impossible.
MEOW’s code base is linked to the leaked Conti v2 source, which surfaced after Conti publicly supported Russia during the Ukraine conflict. MEOW was distributed by actors identified as part of an anti-Russian cyber extortion group, but still no confirmation on the group’s origin.
| Tactics | Techniques |
|---|---|
| Impact | T1486 – Data Encrypted for Impact |
| Exfiltration | T1041 – Exfiltration Over C2 Channel |
| Command and Control | T1071 – Application Layer Protocol |
| Lateral Movement | T1080 – Taint Shared Content |
| Discovery | T1518 – Software Discovery |
| Discovery | T1083 – File and Directory Discovery |
| Discovery | T1082 – System Information Discovery |
| Discovery | T1057 – Process Discovery |
| Credential Access | T1056 – Input Capture |
| Collection | T1056 – Input Capture |
| Discovery | T1497 – Virtualization/Sandbox Evasion |
| Defense Evasion | T1497 – Virtualization/Sandbox Evasion |
| Defense Evasion | T1036 – Masquerading |
| Defense Evasion | T1070 – Indicator Removal |
| Defense Evasion | T1027 – Obfuscated Files or Information |
| Execution | T1129 – Shared Modules |
| Initial Access | T1190 – Exploit Public-Facing Application |
| Initial Access | T1133 – External Remote Services |
| Persistence | T1133 – External Remote Services |
| Initial Access | T1566 – Phishing |
Cyberint (acquired by Check Point), the Impactful Intelligence company, reduces risk by helping organizations detect and mitigate external cyber threats before they have an adverse impact. The Cyberint Argos platform’s patented technology provides superior visibility through continuous discovery of the evolving attack surface, combined with the automated collection and analysis of vast quantities of intelligence from across the open, deep and dark web. A team of global military-grade cybersecurity experts work alongside customers to rapidly detect, investigate, and disrupt relevant threats – before they have the chance to develop into
major incidents. Global customers, including Fortune 500 leaders across all major market verticals, rely on Cyberint to protect themselves from an array of external risks, including vulnerabilities, misconfigurations, phishing, impersonation attacks, malware infections, exposed credentials, data leaks, fraud, and 3rd party risks.

©1994–2025 Check Point Software Technologies Ltd. All rights reserved.
Copyright | Privacy Policy | Cookie Settings | Get the Latest News
Fill in your business email to start


