



Improving assessment policies and processes on safety and security in organizations is essential in outlining potential breaches and dangers to workers and properties. As an individual with a unique skill set, I have helped to identify security measures and appropriate solutions to mitigate various security risks.
Following research on a notorious cybercrime mastermind known as Neo_Net, Cyberint has unveiled the extent of the threat actor’s activities, who primarily targets Spanish and Chilean banks. The findings indicate that the mastermind’s crimes have now expanded into multiple countries and industries worldwide.
Further analysis reveals that Neo_Net has not only focused on targeting Financial Applications through the creation of fake Android applications, but has also expanded its schemes. The cybercriminal group now offers rental services for its SMS Phishing Platform (known as Smishing-as-a-Service) to affiliates and other malicious individuals interested in conducting their own Smishing campaigns.
Additionally, Neo_Net generates profit through various means. They deploy multiple Advertisement Modules within their fake applications to earn Ad Revenue from installations. Moreover, the group engages in selling stolen credentials to third-party and marketplace websites.
Despite utilizing relatively simple tools, Neo_Net has achieved remarkable success by customizing its attack infrastructure to specific targets. This approach has allowed them to illegally acquire over 350,000 EUR from victims’ bank accounts and compromise the Personally Identifiable Information (PII) of numerous individuals. Their multi-stage attack strategy begins with targeted SMS phishing messages distributed in Spain and other countries. These messages leverage Sender IDs (SIDs) to appear authentic, while imitating reputable financial institutions to deceive their victims.
This report provides an overview of Neo_Net’s attack framework and methodology. Additionally, it delves into information about the Threat Group and offers a deep-level understanding of its malware.
From June 2021 to April 2023, an extensive campaign specifically targeted clients of prominent banks worldwide. The main focus of this campaign was on Spanish and Chilean banks, with approximately 30 out of the 50 targeted financial institutions having their headquarters in Spain or Chile. Notable banks like Santander, BBVA, and CaixaBank were among the major targets, while other regions experienced attacks on banks such as Deutsche Bank, Crédit Agricole, and ING.
The attackers employed a sophisticated multi-stage attack strategy. It all started with the distribution of targeted SMS phishing messages across Spain, which was facilitated through Neo_Net’s proprietary service known as Ankarex. To deceive victims, these messages utilized Sender IDs (SIDs) to create an illusion of authenticity, mimicking reputable financial institutions.
Neo_Net’s SMS Phishing Services operate as follows: When an affiliate purchases their services, they gain access to a unique dashboard. Within this dashboard, the threat actor can easily define a “Sender ID or SID,” which appears as the “Sender” to the intended recipient. Next, they specify the contents of the SMS Phishing, typically inserting the Phishing Link. Finally, they provide the list of Mobile Numbers to whom the SMS Phishing Campaign will be sent.
By offering these services, the Threat Actor/Group provides a convenient way for other threat actors and groups to execute their SMS Phishing campaigns without the need to create their own tools. They can simply avail the services provided by Neo_Net, making the process much easier and accessible for potential attackers.
As seen on the screenshot above, the SMS Phishing Services of Neo_Net price per SMS sent depends on the country which is billed. The prices are shown below:
Cyberint has gathered malware samples that were also used by Neo_Net as a part of its campaign. In this research, we dig deep into the collected APK and decode its behavior.
(Sha256: eb0d66eaf000ce34f637123abe459a9776759cd439a821d89328a2960fae9fb0)
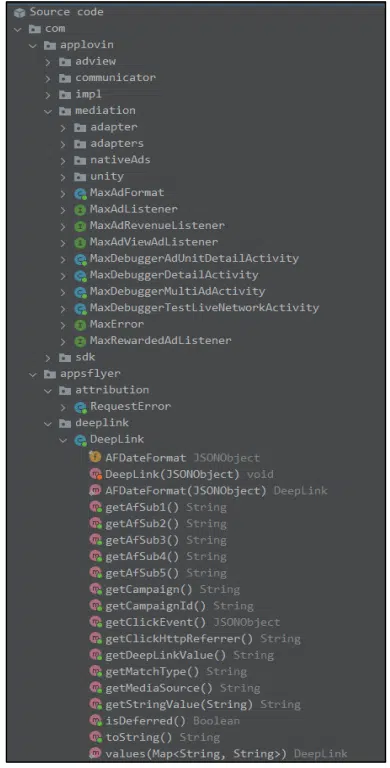
Upon examining the unpacked malicious APK file, it becomes evident that it utilizes several Advertisement Layers, including AppDiscovery and AppsFlyer, to generate revenue when installed on the compromised system. Additionally, the APK employs a DeepLink feature, which involves a URL link being generated. When users click on this link, the app opens with a specific activity or screen, potentially leading them further into the malicious application’s scheme.
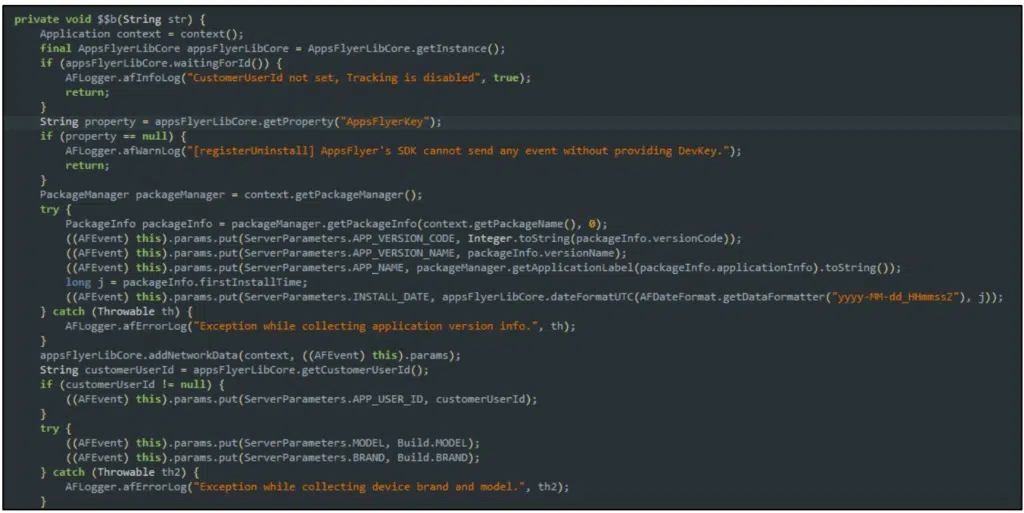

Interestingly, the observed lines of code in the malicious APK file have been intentionally programmed by the Threat Actors to offer an alternative source of income in case the victim does not fall for their Phishing Scheme. This indicates that the threat actors have devised a backup plan to generate revenue even if the primary phishing attempt is unsuccessful.
Based on the overall analysis on the Android malware’s source code, the application is capable of the following behavior:
Based on the above screenshot, it’s clear that the APK itself is inherently malicious due to the extensive and direct permissions it requests upon installation. During our testing, we installed the APK file on a test machine and observed that it immediately impersonates a well-known Spanish bank, CaixaBank. Upon executing the application, it displays the screenshot shown below, further confirming its malicious nature.
Interestingly, upon execution, the application shows a web version of CaixaBank’s Online Portal with the application named “Mi Vodafone”.
When an unsuspecting individual enters their banking credentials, the stolen information is sent to a telegram channel “hxxp://api[.]telegram[.]org/bot5{BLOCKED}19:AAFvxSA{BLOCKED}DXfd590MPhv41BwAqo/send
Message” . The credentials are then viewed and collected by the cybercriminals.
Neo_Net has a significant online presence, particularly on underground markets and its dedicated Telegram Channel. As depicted in the above screenshot, Neo_Net has been active since 2007 and claims to be the CEO of its Smishing-as-a-Service Platform called Ankarex. Interestingly, according to its Telegram bio, the threat actor also boasts a Cybersecurity Certification CEH, typically associated with “Ethical Hackers.” Cyberint also noticed Neo_Net’s existence on GitHub, where the threat actor has publicly shared code in its own repository.
As observed on Neo_Net’s GitHub repository, it has some public repositories namely a “undetected-facebook-phishing” which is highly likely to be a Phishing Kit for Facebook users and a BIN Checker to automate the checking of Credit Card BIN Numbers.
After conducting further investigation, it was discovered that Neo_Net’s GitHub repository is registered under the email address “star-@ -macosfera.com,” which is associated with an already taken-down illegal forum.
The research on Neo_Net has uncovered a worrisome expansion of criminal activities, targeting various countries and industries worldwide. Notably, Neo_Net has moved beyond solely targeting financial applications and now offers “Smishing-as-a-Service,” providing rental services of its SMS Phishing Platform to affiliates and other malicious actors for their campaigns. Additionally, they have devised a profitable scheme by deploying fake applications with advertisement modules to generate revenue and selling stolen credentials to third-party websites.
Cyberint’s impactful intelligence solution combines cyber threat intelligence, external attack surface management, brand protection, and digital supply chain intelligence into a single, powerful platform. By leveraging autonomous discovery of all of an organization’s external-facing assets, coupled with open, deep & dark web intelligence, the solution enables cybersecurity teams to accelerate the detection and disruption of their most pressing cyber risks. Global customers, including Fortune 500 leaders across all major market verticals, rely on Cyberint to prevent, detect, investigate, and remediate phishing, malware, fraud, brand abuse, data leaks, external vulnerabilities, and more, ensuring continuous external protection from cyber threats.

90d0f35bafaa0c99fc8ca6a07a90dd0ef69ce9dcfa4c521c1bc1e8dbbe825830 Sha256
dba9f77877c932ad093267ceca66128cd88ee3979fc2441b0903ab84808a79d4 Sha256
70281d30feb97afb4b1e4c4c72a3542a382561a0c7bda3e6e5fe0a0e5c24a8f1 Sha256
30c804492ca939db5041444399db46d341927d5d2dea936d1543aa6aa36788ce Sha256
24fb177ff570f2805100d256722cf698d082f9872b0fa17b7a39683c68fb9928 Sha256
003e23dc340679696a5e5b774880ea87b74bb5b8b1297a01eaaae484bd9a159f Sha256
003e11066cae3fb15d5648fcebfe1d5c540f4362e776e3963c2a1139115ced30 Sha256
003dfaa9c5d6db3320987e718ec4d0ed44a6e17788fd70c144c945d3d3dc48e0 Sha256
003cfae6c796187fe633ea6bb0fe8be811b2ba864103da6f6280d0b48ba447b2 Sha256
003c99ecc1b43ec3da686a53c683c8fd6a518a6485a2020bce95afa54f024ef2 Sha256
003be0cf4e361883375fb39333db57794ca2f3375eca16cdc6d53092b3dcef23 Sha256
003abb8242f5c3899c36f525f41fb5cbce75a58303219cb28e8ad813adfaab3f Sha256
003a85110bc0e7847a9d8fb7e853d0769e6af5690eb6546ab1329d032d362230 Sha256
00399c8840a10f4677af6ba2db3d4779a89616ac3a5d61b2d1e7c7a7ffe93021 Sha256
00395c51b8cf3c9204da04caf34b2f7fd42260e246e74a918950bd49766c7d7b Sha256
003924c28a8de5cb84c284298acff5402f524dd6b31d5071832b90d966b1e2cf Sha256
00381b45f22f7fd70e9dfb4d76d437b15ecdac234cacbb8fd5df9196fb463f88 Sha256
00373fdb1f2e0e7b1a8fc8010b8665a3c819276bbe420b25a334af9d44f3e064 Sha256
003680d473f0ed18b8ec5f75898892f0f8b28e95f243d3c40b2dffbd9c3103e3 Sha256
00359182b14d245d5b7bcf9181c041456fb70ca70dc1edcee5d8757144a6483c Sha256
0035035b1b26765e193fa737c418058781b1b60be2510ae4e13acaa81684d212 Sha256
003422637b31b1dda2d7c1b986088392af0175483c3b3ba8f080444858e10bd5 Sha256
0034011eeb33c14af275d4d68b67dc965c8adb477de401aa6a4a29cc990f5ed8 Sha256
00339eebe2938cd0193937e6e1c46147b906274334d63430507a962cfbddeeae Sha256
0032dd8f45d08cd74860fe35bcac1208a18ad913dbe1511ae89ce8a2a5735d03 Sha256
0031a578bfebd801c5e40c154101cd507462f0fc12ee4b2a9485d831ecd899ec Sha256
0031563da23d86bda6ad0cad009c773b1a46b65b42cc234c8f08462f2a8b18c3 Sha256
003001b069e028effe6624b4efaa3d1332421a07e51789ef086b38040c2ba8fb Sha256
002f77e3a4cec4a0a7fca3db5be643909f2ff7734962d4be13ebae837eeea218 Sha256
002e94dc42aa7f4e5857b8524851a66479e97c781dbb06b1676e8046f95734c7 Sha256
002e6310023d2ccca646482790500b97f4f3dfbb710ff765e46f2742a632ba98 Sha256
002dc083ae4cf25381d9ebdd36f7283160af258b1fcde346e0076953e3de9b50 Sha256
002b065e4d12be26e36e248544b38466bb28e946ce5445a76f0898039769f7d6 Sha256
002a8cec53930d3518a0e5bf1efbe02b451aeb23e4f7b68c78f163f2cc49cf0f Sha256
002a2ca2751616afcffa082af72611903ef3413c613f8aeda8fcde389924ee49 Sha256
9fc1c2137bb7c342ceb8bfa39a4745f89aaaf08b50f3a26b51276cb65e55b024 Sha256
d52e0cbfcb5ef372f799f77124d604e9e81f598519477113e098f226dab096f0 Sha256
5c893b0933f8c336bdc4e17a5798be1b1febc11f6255e15937b773204c72b73f Sha256
©1994–2026 Check Point Software Technologies Ltd. All rights reserved.
Copyright | Privacy Policy | Cookie Settings | Get the Latest News
Fill in your business email to start


