


Hacktivism – the practice of carrying out cyberattacks to advance political or social goals – is not new. Hacktivist attacks go as far back as the 1980s.
Yet today’s hacktivists often look and operate in ways that are markedly different from their predecessors. They’ve embraced new techniques, they often have more resources at their disposal and they can prove more challenging to stop.
As Complex Discovery notes based on recent ENISA survey data, businesses now face an “evolving cyber threat landscape, driven by growing geopolitical tensions and the increasing sophistication of cyber actors.”
Contending with the modern hacktivist threat requires an understanding of how hacktivism has changed and which defense techniques are necessary for mitigating hacktivism today.
To explain how hacktivism has changed over the years, let’s discuss some key developments and changes in the way hacktivists operate, as well as why they do what they do.
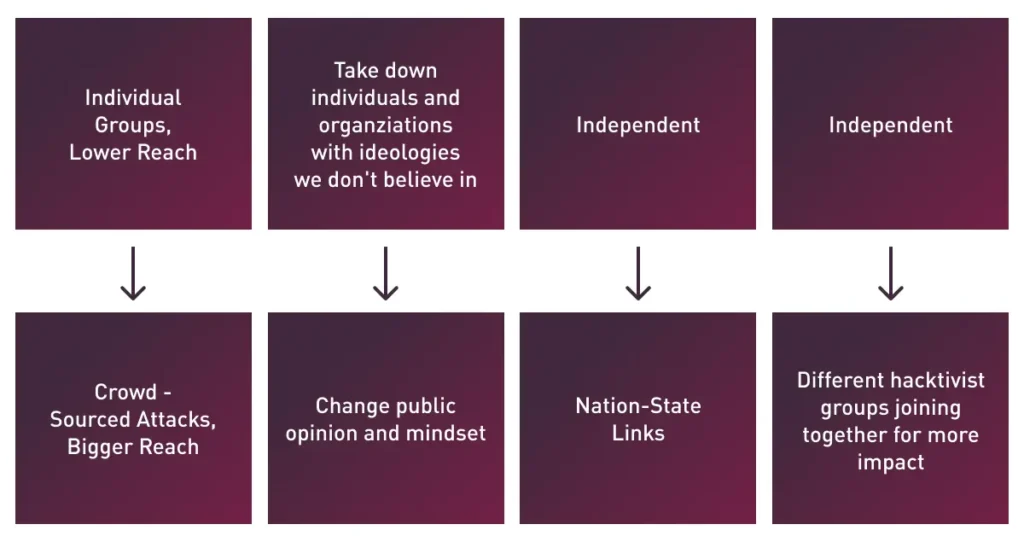
Historically, most hacktivist groups worked independently. They planned and executed attacks entirely on their own.
But that has changed as hacktivists increasingly rely on crowdsourcing to help expand their attacks. Crowdsourcing allows them to make their campaigns public and invite anyone to contribute, which offers three key advantages from attackers’ perspective:
Crowdsourcing has already become prominent within hacktivist campaigns associated with the Israel-Hamas conflict
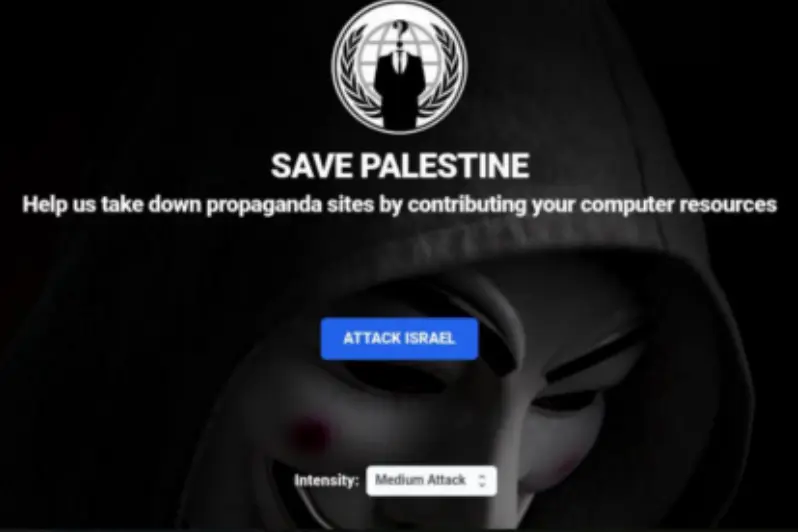
and the Russia-Ukraine war. For example, in the context of the latter conflict, Telegram channels appeared inviting individuals to enlist in cyberwar efforts in support of Ukraine.
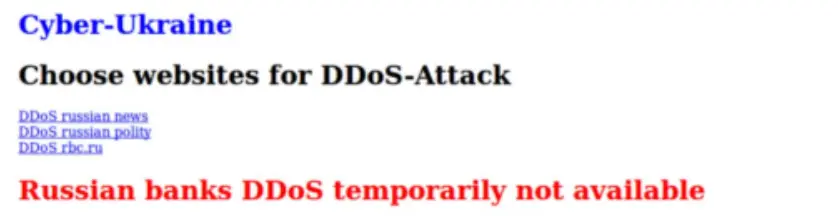
As a growth strategy, crowdsourcing can deliver dramatic results for hacktivist groups. For instance, as Dark Reading noted in 2022 about a hacktivist project sponsored by attackers sympathetic to Russia, “the crowdsourced DDoS project known as ‘DDoSia’ has grown exponentially, by 2,400%” in just one year..
The goals and mindsets of hacktivists have also evolved. Today, hacktivism campaigns are often not aimed at destroying targets as much as changing people’s minds.
For example, when the Israel Aerospace Industries (IAI) website planned scheduled maintenance, a hacktivist group that knew in advance about the planned downtime published a statement announcing they had shut down the site. Even though they hadn’t, merely convincing people that they had was an effective way of creating a sense of vulnerability within their target group.
Historically, most hacktivists belonged to independent groups. But today, many are aligned at least to some extent with nation-states – a trend that is evident based on who hacktivists attack and the hours during which they are active.
Anonymous Sudan, whose members have been indicted by the U.S. government for cyberattacks on hospitals and other critical infrastructure around the world, is one example of a hacktivist group with nation-state ties.
Association with nation-states is significant because it translates to more resources for attacks because governments can provide them with financing and skilled technical personnel. It also means that they are more likely to focus on targets in specific countries or regions that are adversaries of the nation-states supporting the hacktivists.
The tendency of today’s hacktivists to embrace outside support has also led many to form coalitions – such as the “Five Families” collaboration that Cyberint discovered on Telegram. Other prominent examples of hacktivist groups banding together include SiegedSec, GhostSec and Blackforums, to name just a few.
The main motive behind these collaborations is simple: Hacktivists have realized that by pooling their resources and acting in coordination, they can increase their impact. This is another example of why the hacktivist threat has become more challenging to contain.
In short, hacktivism has evolved in ways that increase its effectiveness and the level of risk that hacktivist groups pose to businesses.
The good news is that the core cyberdefense strategies that are effective at mitigating hacktivist threats have not changed. Effective Attack Surface Management, active vulnerability scanning and testing and threat intelligence remain key pillars of hacktivism defense. With these capabilities in place, organizations substantially reduce their risks of falling victim to hacktivist hacks.
©1994–2026 Check Point Software Technologies Ltd. All rights reserved.
Copyright | Privacy Policy | Cookie Settings | Get the Latest News
Fill in your business email to start


