


Although 2024 began with a Q1 decline in the frequency of ransomware attacks, the second quarter was underscored by a return to a much more intimidating world of ransomware attacks globally, and the third quarter continues the trend of the second.
In Q2 2024, the number of attacks stood at 1,277 cases, but Q3 saw a small decrease of 5.5% with 1209 cases. Although the numbers remain pretty much the same, the dominance of ransomware groups changed, where the RansomHub group is taking the first place crown from LockBit after 2 years.
Interestingly, this quarter, the top 10 ransomware groups were responsible for 58.3% of all attacks. Compared to the previous year, this highlights the significant influence of new ransomware groups and the highest number of active groups on record, indicating a decline in dominance by historically significant groups in the ransomware landscape.
Nevertheless, it is no surprise that the U.S. continues to be the country most targeted by ransomware, while business services is the most targeted sector, similar to last quarter statistics. There is no doubt that the new faces introduced to the industry, along with ongoing attacks on businesses around the world, claimed many victims.
This, combined with the consistency of the industry’s leaders – RansomHub, Play, LockBit3.0, Meow, and Hunters – led to devastating results for companies worldwide, such as Young Consulting, Halliburton, and others.

While it was a successful quarter for the entire ransomware industry, three families stood out. The new leader, RansomHub was the most dominant ransomware group, with 195 new victims, 16.1% of all ransomware cases. For the first time since 2022 LockBit are not in first place!
Coming second was the Play ransomware group, which claimed a significant 89 victims, 7.3% of all ransomware cases. As expected, Play continues to be a dominant power in the ransomware landscape. The third place was saved for the LockBit group, which claimed 85 successful attacks this quarter, marking a new low for the group, with the lowest number of attacks per quarter in a year and a half.

RansomHub has quickly risen to prominence in the ransomware landscape, capitalizing on the disruption of major players like ALPHV and LockBit. With its roots likely in Russia and connections to former ALPHV affiliates, the group has established itself as a formidable force by leveraging its Ransomware-as-a-Service (RaaS) model, which offers attractive profit-sharing terms to affiliates. This approach has led to a surge in attacks, particularly in August and September 2024, when over half their attacks took place. Another interesting fact is that the attack count of those two months represents more than 10% of all ransomware attacks we tracked this quarter!

The ransomware syndicate responsible for numerous destructive assaults on significant American municipalities has purportedly executed over 560 successful attacks since June 2022. Researchers uncovered a Linux variant of the Play ransomware that only encrypts files when running in a VMWare ESXi environment, which assists them in wider operations. If not hindered, Play is going to break its own record of yearly victims in 2024 (301).

Since Operation Cronos, which disrupted LockBit’s affiliate program and exposed one of its leaders, Dmitry Khoroshev (known as ‘LockBitSupp’), the group’s operations have significantly declined. For the first time in two years, LockBit has fallen to third place among ransomware groups this quarter. This marks a notable shift in their activity level following these law enforcement actions.
In Q3, LockBit attacked almost 60% less companies than Q2, showing the massive impact of law enforcement operations. Despite these major operations against the group, LockBit continued its global onslaught against organizations, maintaining its position in the top 3 ransomware groups as long as possible.

Regarding the most targeted countries (Figure 2), the U.S. remains the number one targeted country globally, with good reason. 50% of the total ransomware attacks targeted the world’s number one economy i.e. 599 cases.
The second most targeted country this quarter was the Canada, with 73 cases, lagging far behind the U.S.
Finally, United Kingdom was in third place with 59 ransomware cases this quarter. Even when focusing on the top three countries, there is no doubt that the U.S. is the most profitable country for threat actors.

As expected, the business services sector was the most targeted in Q3, with 27% of the ransomware cases, followed by the retail and manufacturing sectors, with 18% and 11%, respectively (Figure 3).

Lynx, a double-extortion ransomware group, has been highly active recently, listing numerous companies as victims on their site. However, the group claims to avoid targeting government entities, hospitals, non-profits, and other socially crucial sectors.
Once inside a system, Lynx encrypts files, adds the .LYNX extension, and leaves a ransom note titled “README.txt” in multiple directories. At the time of this report, Lynx had claimed over 28 victims, highlighting their ongoing activity in the ransomware landscape.

Orca Ransomware hit 2 victims in September 2024, Chernan Technology from Taiwan, and ExcelPlast Tunisie from Tunisia. According to them (taken from their DLS ‘introduction’): “Orca Ransomware’s primary motivation is driven by financial incentives, with a strong commitment to avoiding unnecessary harm to organizations.
We understand the importance of ethical considerations in the quest for financial success and adhere to a strict policy against targeting government institutions, hospitals, or non-profit organizations, as these sectors are crucial to society.”

The ransomware leak page pertaining to Chernan Technology contains limited information, primarily focused on the company’s name. There are no specified compromise dates, nor any significant content extracted from the site such as paragraphs or descriptions.
The presence of images is also absent, indicating a streamlined leak with minimal visual components. No download links are provided on the page, which suggests that the data disclosure may not have involved direct access to sensitive files or documents typically associated with ransomware incidents.
The nature of the leak remains unspecified, and further details about Chernan Technology’s activities or the implications of the ransomware attack are not available in the current summary.
The Mad Liberator ransomware group, active since July 2024, focuses on data exfiltration rather than data encryption. Like other extortion groups, they maintain a leak site where they publicly list their victims.
Mad Liberator relies on social engineering to infiltrate its targets, specifically those using remote access tools such as Anydesk. The group deploys malware that mimics a Windows Update screen to make it appear as though the system is updating.
This decoy screen, which performs no real updates, is likely designed to evade detection by most antivirus software. To prevent users from exiting the fake update screen using the “Esc” key, the attacker disables keyboard and mouse input through Anydesk, keeping the deception in place. Once inside, the attacker uses Anydesk to access the victim’s OneDrive account and files on a central server through a mapped network share, transferring data using Anydesk’s FileTransfer feature.
Afterwards they run an Advanced IP Scanner to identify other vulnerable devices but do not attempt lateral movement. Instead, they create ransom notes across multiple locations on a shared network, without leaving them on the victim’s device.

Researchers highlighted this attack chain as a reminder of the importance of continuous staff training and clearly defined IT policies for remote access sessions. They also recommend that administrators use Anydesk Access Control Lists to restrict connections to trusted devices only.
A new ransomware group has begun leaking data it claims to have stolen from five organizations across the globe. Recently, Valencia Ransomware has added links to its DLS, offering gigabytes of allegedly exfiltrated data for download. The victims appear to include a California municipality, a pharmaceutical company, and a paper manufacturer.

The reported victims are the City of Pleasanton in California, where attackers claim to have taken 283GB of sensitive data; Malaysia’s Duopharma Biotech with 25.7GB; Indian paper manufacturer Satia with 7.1GB; and Bangladeshi drug company Globe Pharmaceuticals with 200MB. Additionally, Spanish fashion giant Tendam is also rumored to be a target, which is especially concerning as they were also reportedly struck by Medusa ransomware earlier this month.
There is growing speculation that some Valencia group attacks may be connected to critical vulnerabilities found in the WhatsUp Gold network monitoring software from Progress. These vulnerabilities, that allow attackers to take over admin accounts, were discovered and responsibly disclosed in May, with a proof-of-concept exploit released in late August.
Helldown is an emerging ransomware group that listed 17 victims on its leak site last month. Despite being relatively new, Helldown has rapidly gained a reputation in the cybersecurity community for its aggressive tactics. The group uses advanced encryption methods, including AES, Salsa20, and RSA, while maintaining a high level of anonymity through the dark web and cryptocurrency transactions.
Known for exploiting vulnerabilities to breach networks and disable security measures, Helldown primarily targets the IT services, telecommunications, and manufacturing sectors. Their approach of exfiltrating sensitive data and threatening to release it publicly unless a ransom is paid has proven both highly effective and destructive.

A new ransomware group, “Pryx,” has recently appeared on the cybercrime scene, claiming responsibility for its first major attack. Pryx announced that it compromised the systems of Rowan College in Burlington County (RCBC.edu) and stole 30,000 university applications. According to the group, they successfully breached the college’s IT systems and obtained sensitive data from the institution. This disclosure was made via their data leak site, accessible through both the regular internet and the dark web.

Pryx operates a data leak site where they publicly expose information about victims who refuse to pay the ransom. This platform is accessible to the public on the internet, as well as, like many ransomware groups, through the dark web. Pryx’s data leak site presents an ominous interface, with a spider web motif and the slogan “Get Pryxed” prominently displayed.
The platform is organized into sections like Contact Information, Public PGP Key, All Updates, and Breaches and Operations by Pryx. The homepage boldly invites visitors to “Get Pryxed,” reflecting the group’s aggressive and provacative style.

Recently, On July 2024, the landscape of cyber threats has been enriched by the emergence of a new ransomware group named “Ransomcortex”. This group is distinguished by its specialization in attacking healthcare facilities, having already collected four victims within a few days of its first appearance. Among these, three are Brazilian healthcare facilities and one is Canadian.

Unlike many other ransomware groups, Ransomcortex has concentrated its efforts solely on attacking healthcare facilities. This targeted approach raises concerns about what criminals gain if ransoms are not paid.
The answer lies in the intrinsic value of healthcare data, which can be exploited in various ways. Criminals can commit financial fraud by using patients’ personal information to open bank accounts, apply for credit cards, or secure loans.
They may also resort to extortion, threatening to release sensitive medical information unless their demands are met. Additionally, stolen medical data can be sold on the black market or used for phishing and online scams. Furthermore, the data can facilitate identity theft, where criminals create false identities using the personal information of patients.
The group emerged on July 2024, hitting 3 victims in a short time and publishing them on their official data leak site. The 3 victims are from United states, China and Netherlands. All 3 of them were posted on the same day – 10/07/2024.
The Vanir Group’s website features an interactive terminal where users can input commands such as “help” for a list of available commands, “news” for updates about the group and their activities, and “victims” to view a list of all their targets.

However, the group’s data leak site was seized by law enforcement, and it’s been two months without any sign of their return:

A new ransomware group that published 6 victims on September 30. Currently their blog “Nitroblog” is down. 5 of the victims are from the USA, and one is from Canada.

UK authorities have arrested a 17-year-old suspected of involvement in the 2023 ransomware attack on MGM Resorts. The individual is thought to be part of the “Scattered Spider” hacking group, notorious for its social engineering tactics and high-profile cyberattacks.
The MGM breach led to widespread disruption of its IT systems and compromised customer data. This arrest marks a key step in efforts to dismantle Scattered Spider’s operations.
On August 12, 2024, in a significant international collaboration, the FBI successfully disrupted the Radar/Dispossessor ransomware operation. The agency seized servers and websites associated with the group, marking a major victory against the cybercrime network.
The takedown follows a thorough investigation involving law enforcement agencies worldwide, as they continue to target organized cybercriminal groups. This operation highlights ongoing efforts to dismantle ransomware organizations that have been responsible for numerous attacks globally.
Germany Seizes 47 Crypto Exchanges Linked to Ransomware Gangs German authorities have successfully seized 47 cryptocurrency exchanges used by ransomware gangs for laundering illicit gains. This move is part of a larger effort to crack down on cybercriminal networks exploiting digital currencies to obscure their financial activities.
These exchanges were found to have facilitated the laundering of funds linked to ransomware attacks, further highlighting the increasing use of cryptocurrencies by threat actors for illicit transactions. The action comes as part of a coordinated global initiative to target platforms that provide ransomware operators with the financial infrastructure needed to hide their ransoms and profits.
This effort demonstrates law enforcement’s growing focus on digital currencies as a critical part of disrupting cybercriminal operations.
German authorities have successfully seized 47 cryptocurrency exchanges used by ransomware gangs for laundering illicit gains. This move is part of a larger effort to crack down on cybercriminal networks exploiting digital currencies to obscure their financial activities.
These exchanges were found to have facilitated the laundering of funds linked to ransomware attacks, further highlighting the increasing use of cryptocurrencies by threat actors for illicit transactions. The action comes as part of a coordinated global initiative to target platforms that provide ransomware operators with the financial infrastructure needed to hide their ransoms and profits.
This effort demonstrates law enforcement’s growing focus on digital currencies as a critical part of disrupting cybercriminal operations.
In recent years, ransomware groups have increasingly shifted their focus towards Linux-based systems and VMware ESXi servers, recognizing them as valuable targets within corporate infrastructures. These systems often host critical virtual machines (VMs) that, if compromised, can cause widespread disruption.
Furthermore, ransomware capabilities have evolved considerably over the past year, with attackers developing more sophisticated techniques to evade detection and maximize damage. Black Basta, for instance, has adopted custom malware designed to bypass security tools, making it more evasive and effective against modern defenses.
In addition, ransomware groups like RansomHub are leveraging legitimate tools like Kaspersky’s TDSSKiller to disable endpoint detection and response (EDR) software, allowing them to operate undetected in compromised environments.
Another significant development is the abuse of cloud-based tools for data theft. For example, ransomware operators, including BianLian and Rhysida, are now using Microsoft’s Azure Storage Explorer and AzCopy tools to steal data from victim networks and store it in cloud-based infrastructure, adding a new layer of complexity to their operations.
These developments demonstrate the growing sophistication of ransomware, with groups increasingly targeting more robust systems and leveraging new capabilities to outsmart security measures across various environments.
In August 2024, the Port of Seattle was hit by a ransomware attack attributed to the Rhysida ransomware group. The attack disrupted the U.S. government agency responsible for Seattle’s airport and seaport operations. While the exact details of the breach and its full impact are not entirely clear, it is known that the attack caused significant system outages over a span of three weeks.
The RansomHub ransomware group claims to have carried out a cyberattack on Kawasaki, a global manufacturer, threatening to leak stolen data unless a ransom is paid. The threat actors reportedly gained unauthorized access to sensitive company data and have issued an ultimatum, leveraging the potential exposure of this information to press for payment. As with other RansomHub operations, the group engages in double extortion tactics, encrypting files while threatening to expose sensitive information publicly.
Halliburton, a major oil and gas services company, confirmed that sensitive data was stolen during a cyberattack in August 2024, linked to the RansomHub ransomware gang. The attack, which caused significant operational disruptions, led to systems being taken offline as the company worked with cybersecurity firm Mandiant and law enforcement to address the breach.
While Halliburton has not disclosed detailed information about the stolen data, it was revealed that the ransomware group used a new version of their encryptor to carry out the attack, as part of a double extortion scheme aimed at both encrypting data and threatening to leak it unless a ransom is paid.
Young Consulting, a prominent US software provider specializing in employer stop-loss insurance, confirmed that the BlackSuit ransomware group compromised the personal data of nearly a million customers. Occurring in April, the breach involved unauthorized access and subsequent data encryption by the attackers.
The compromised data included full names, Social Security numbers (SSNs), birth dates, and insurance claim details of clients, notably affecting Blue Shield of California subscribers. Moreover, BlackSuit claims to have leaked extensive corporate data on its extortion site, including contracts, financial records, and personal employee information, heightening the risk of further illicit use of the exposed information.
In Q3 2024, the ransomware landscape saw minor changes, with a 5.5% drop in total attacks compared to the previous quarter. RansomHub led with 195 victims, accounting for 16.1% of all ransomware cases, while Play remained stable with 89 victims. LockBit, for the first time in two years, fell to third place with 85 attacks due to law enforcement pressure.
The U.S. remained the top target, representing 50% of cases, while Israel entered the top 10, replacing India. New players like Orca, Lynx, and Mad Liberator introduced different techniques, such as data exfiltration. Although fewer new groups emerged this quarter compared to the last, these developments reflect a constantly evolving ransomware landscape, with both established and newer groups competing for dominance.
Law enforcement actions worldwide continue to put pressure on ransomware groups, leading to the decline of major players like LockBit. As these large operations struggle, it’s only a matter of time before other big and small ransomware groups follow the same path. The ongoing crackdown has created a more hostile environment for these groups, signaling that their dominance may not last much longer.
Overall, this quarter followed a similar pattern to the previous one. Aside from LockBit’s decline and RansomHub’s rise, there were no significant shifts in the ransomware landscape, maintaining consistency with Q2 trends.
Read on for the full Q2 report:
Although 2024 began with a Q1 decline in the frequency of ransomware attacks, the second quarter was underscored by a return to a much more intimidating world of ransomware attacks globally.
While the number of ransomware attacks decreased in Q1 2024 to 1,048 cases, in Q2 2024, it increased to 1,277 cases. This is almost a 21.5% increase compared to Q1 2024. One reason could be the intervention of law enforcement, as demonstrated by LockBit arrests and the identity reveal of group admins and other cybercriminals’ infrastructure seizure. As a result, big ransomware operations were split into smaller ones, creating more competition between ransomware gangs.
The emergence of new ransomware groups in 2024, as evidenced by the emergence of 27 new groups by the second quarter, suggests a sustained and evolving threat landscape. These groups, such as ArcusMedia, APT73, dAn0n, and DragonForce, pose fresh challenges to cybersecurity professionals and organizations worldwide.
Interestingly, this quarter, the top 10 ransomware groups were responsible for 60% of all attacks. Compared to previous quarters, this highlights the significant influence of new ransomware groups and the highest number of active groups on record, indicating a decline in dominance by specific groups in the ransomware landscape.
Nevertheless, it is no surprise that the U.S. continues to be the country most targeted by ransomware, while business services is the most targeted sector, similar to last year’s stats. There is no doubt that the new faces introduced to the industry, along with ongoing attacks on businesses around the world, claimed many victims. This, combined with the consistency of the industry’s leaders – LockBit3.0, Play, RansomHub, IncRansom, and Medusa – led to devastating results for companies worldwide, such as Keytronic, London hospitals, and others.

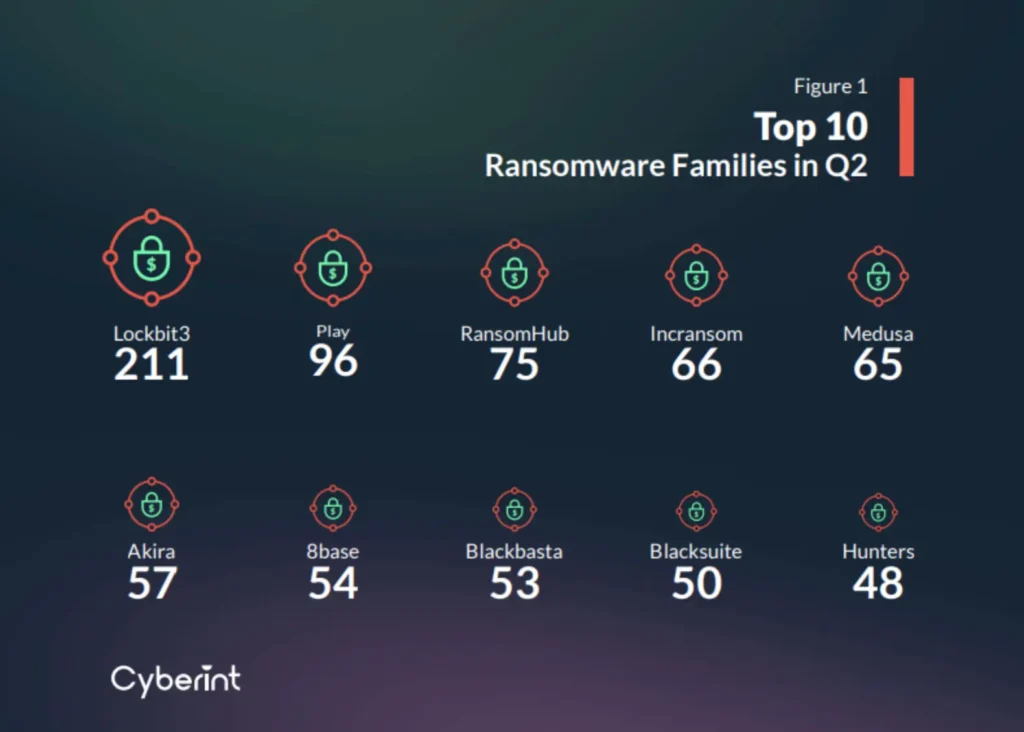
While it was a successful quarter for the entire ransomware industry, three families stood out. As expected, LockBit3.0 remains the most dominant ransomware group, with 211 new victims as they claim 16.5% of all ransomware cases.
Coming second is the Play ransomware group, which claimed a significant 96 victims, 7.5% of all ransomware cases. Play continues to be a dominant power in the ransomware landscape. Ransomware as a Service (RaaS) is a business model where affiliates pay to use ransomware attacks developed by operators. It mirrors the Software-as-a-Service (SaaS) model. This approach is significant in the global proliferation and persistence of ransomware attacks. The rise of RaaS models has notably impacted the ransomware landscape, exemplified by the RansomHub group, which recently claimed the third spot with 75 victims this quarter.
In the current landscape, where ransomware groups are closing their operations much faster than previously observed, a group that consistently executes dozens of successful ransomware attacks every month and sustains its activities for over a year can be considered a veteran. Therefore, the fourth and fifth places are also reserved for other veteran groups: the IncRansom group, which had 66 victims this quarter, and the Medusa group, which had 65 victims.
On Feb. 19, 2024, Operation Cronos, a targeted law enforcement action, caused outages on LockBit-affiliated platforms, significantly disrupting the notorious ransomware group’s operations. The UK, US, and Australia have revealed the identity of Dmitry Khoroshev, a Russian national and the leader of the once-notorious LockBit ransomware group, following an international disruption campaign led by the National Crime Agency (NCA).
Dmitry Khoroshev, also known as LockBitSupp, who previously operated in secrecy and offered a $10 million reward to uncover his identity, is now facing sanctions announced by the FCDO in coordination with the US Department of the Treasury’s Office of Foreign Assets Control (OFAC) and the Australian Department of Foreign Affairs.
Over the past three months, the group has made efforts to regroup; however, according to the NCA’s assessment, their operations are currently running at limited capacity due to this investigation, resulting in a substantial decrease in the global threat posed by LockBit.
LockBit has launched a new leak site where they have exaggerated their activity by listing victims targeted before the NCA gained control of their services in February, and have also claimed responsibility for attacks carried out using other ransomware strains. Despite these major operations against the group, LockBit continued its global onslaught against organizations, maintaining its position as a dominant force in ransomware operations.
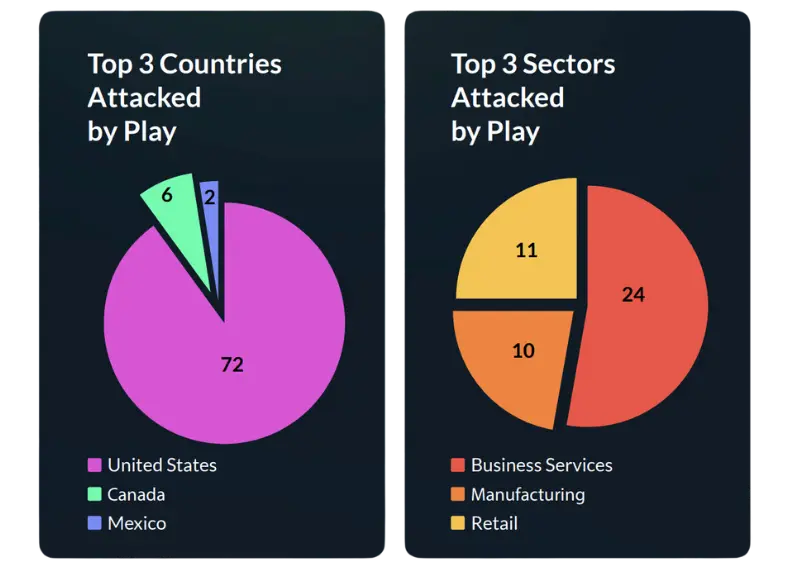
The ransomware syndicate responsible for numerous destructive assaults on significant American municipalities purportedly executed over 300 successful incidents since June 2022. Among the notable attacks, this quarter was the breach targeting the Swiss government, where approximately 65,000 files were pilfered by the Play ransomware gang during an assault on an IT vendor. Like BlackBasta, there are no indications that this systematic group intends to halt its operations. An interesting point is that in January
2024, this group only managed to attack 3 victims, which is the lowest number in the past 2 years.
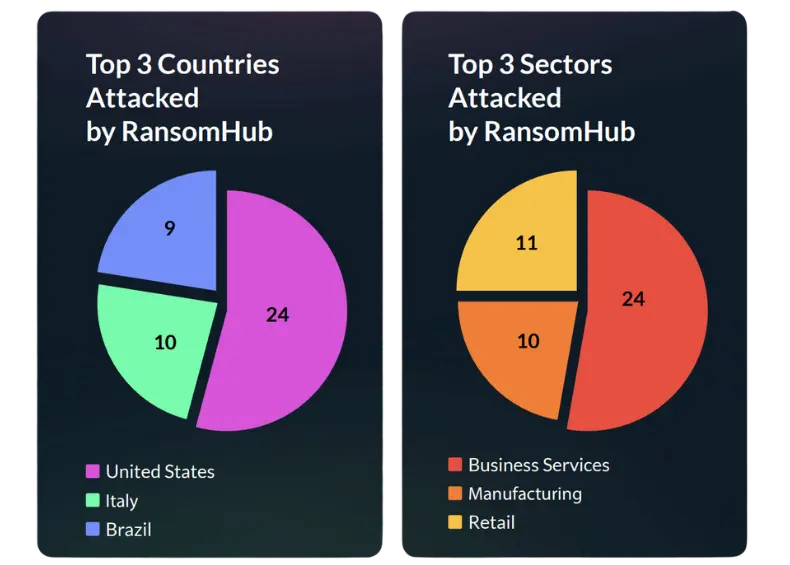
The RansomHub ransomware group has emerged as a significant player in the ransomware landscape, making bold claims and substantiating them with data leaks. In February 2024, RansomHub posted its first victim, the Brazilian companyYKP. The group has since successfully attacked over 100 organizations worldwide. RansomHub offers affiliates a 90% commission rate, which is higher than the typical 80-90% range seen in the RaaS market.
This lucrative rate is likely to attract seasoned affiliates from other platforms, leading to a surge in RansomHub-related infections and victims, as we’ve seen in this quarter, where they successfully attacked 75 victims worldwide.
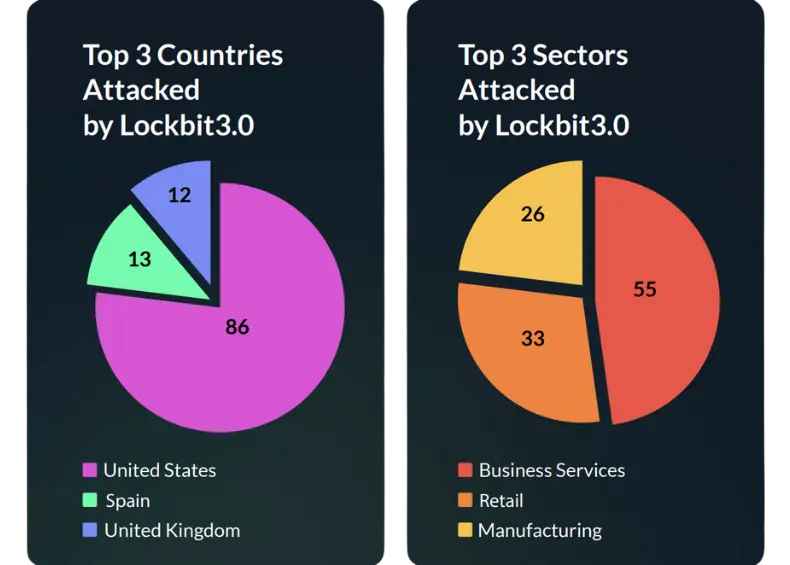
Regarding the most targeted countries (Figure 2), the U.S. remains the number one targeted country globally, with good reason. The world’s number one economy was the victim of ransomware attacks this quarter in 47.8% of total cases, i.e., 611 cases. The second most targeted country this quarter is the United Kingdom, with 85 cases, lagging far behind the U.S.
Finally, Canada is in third place with 66 ransomware cases this quarter. Even when focusing on the top three countries, there is no doubt that the U.S. is the most profitable country for threat actors.

As expected, the business services sector was the most targeted in Q2, with 28.5% of the ransomware cases, followed by the retail and manufacturing sectors, with 17% and 11.5%, respectively (Figure 3)

The Underground ransomware group surfaced in May 2024, quickly posting 13 victims on its official Data Leak Site (DLS). In contrast, June saw fewer victims, with only 2 reported. 6 of the victims are from the United States, two from South Korea, and the rest from Germany, Slovakia, UAE, Taiwan, Singapore, Spain, and Canada.
Within the cybersecurity community, it is believed that SpaceBears, a ransomware group reportedly based in Moscow, Russia, has recently claimed responsibility for several high-profile cyberattacks, showcasing their advanced tactics in the cyber threat landscape.
The group provides detailed instructions for visitors to their Data Leak Site (DLS) on what to do if they believe their data has been compromised. They claim that upon receiving payment, they will remove the published data, delete it from their servers, and provide a decryption tool for the encrypted files.
Additionally, they offer guidance on how to prevent similar attacks in the future. SpaceBears lists 20 organizations on their DLS, most of which are medium to small-sized enterprises. The organizations are spread across several countries: 7 in the US and the others in Portugal, Canada, Germany, Norway, Morocco, Singapore, Ecuador, and Fiji. Sector-wise, the victims include manufacturing companies, small technology solutions providers, and healthcare-related companies.
The Flocker (aka Fsociety) ransomware group emerged at the end of April, listing four victims on its official DLS in just two days. The group continued to operate and listed more victims on its DLS in June.
Embargo ransomware, created using the Rust programming language, is a new group that emerged in April 2024. The threat actors (TAs) behind this ransomware employ double extortion tactics, exfiltrating sensitive information from the victim’s systems before encrypting the data. One notable victim, “Aussie lender Firstmac,” has garnered significant media attention.
According to Embargo, the group stole over 500 gigabytes of data, including “full databases, source codes, and sensitive customer data.”
DarkVault recently published data from 19 victims on its leak site in April 2024. This rapid publication rate indicates either previously undisclosed activities or a well-coordinated team capable of quickly executing multiple attacks. Their targets are diverse, spanning industries such as surveillance systems, fitness, fashion, and healthcare insurance, and are located in countries including the US, India, Sri Lanka, and the UK.
Among their notable victims are the UK-based charity Tommy Club, which raises funds for various divisions of the Royal British Legion, and Sandip University in Nashik, India. Despite their brief history, DarkVault’s ability to compromise significant targets has raised concerns within the cybersecurity community.
There has been speculation about DarkVault’s connection to LockBit due to similarities in their activities and site design. However, no concrete evidence supports this theory, and it is equally plausible that DarkVault is a new entity or a rebranding effort by experienced cybercriminals seeking to capitalize on LockBit’s notoriety.
This group surfaced at the end of April and has since posted information about 14 victims on their data leak site. Of these victims, 10 are based in the United States, with business services as the primary sector targeted.
A notable observation from their data leak site is the apparent lack of emphasis on design or a visible logo, which may suggest that the group prioritizes attack methodologies over branding and has a smaller team.
In contrast to other naming conventions that researchers use to identify threat actors, this group has chosen to refer to themselves as “APT” (Advanced Persistent Threat) followed by a number, specifically APT73, a ransomware group modeled on LockBit. This was observed through similarities in their “Contact Us,” “How to Buy Bitcoin,” and “Web Security & Bug Bounty” pages, which closely resemble the layout of the LockBit Data Leak Site (DLS). The content on these pages mirrors that of LockBit, indicating that this is essentially a LockBit-style Ransomware Data Leak Site (DLS). One notable difference is the “Mirrors” section, which lacks any active mirrors, unlike LockBit, highlighting a level of amateurism within this group.
To date, the group has targeted a total of 12 victims in various locations worldwide, including Germany, Canada, the Czech Republic, and the United States (twice). Their attacks have been exclusively focused on the business services sector.
The Qiulong ransomware gang, a new cyber threat actor, has emerged, targeting Brazilian victims. The group announced its presence by compromising two entities in Brazil: Dr. Lincoln Graca Neto and Rosalvo Automoveis.
The attackers created a website for posting data breaches, including summaries of the compromised targets and mocking content directed at Dr. Lincoln Graca Neto. Dr. Neto either rejected the ransom demand or negotiated in bad faith, as he has not paid the ransom.
Although this is the first known exploit of the Qiulong gang, their technical capabilities are evident in their ability to target multiple victims and potentially compromise sensitive data. These attacks suggest that the Qiulong gang aims to become a significant player in the ransomware threat landscape. So far, the group has posted 8 victims on their DLS; 7 of them are from Brazil, and one from Canada.
The rebranding of ransomware operation HelloKitty to HelloGookie coincided with the publication of internal Cisco network data exfiltrated from a 2022 attack, exfiltrated source code for several CD Projekt Red games from a 2021 attack, and four private decryption keys for other intrusions that involved an older iteration of its ransomware encryptor.
HelloGookie, which has not yet touted any new victims, noted on its data leak site that it had a list of Cisco NTLM hashes that were exfiltrated during a breach, which was believed to be conducted by the Yanluowang ransomware attack.
Meanwhile, more than 400GB of uncompressed information was included in the exposed CD Projekt Red data, which included source code for the company’s “The Witcher 3,” “Cyberpunk,” and “Gwent” titles, as well as numerous console SDKs and build logs, said Sventek, one of the developers who compiled Witcher 3 from the leaked data.
The Apos ransomware gang emerged on April 2024. They listed 4 victims on their DLS, other than which, it looks like the group hasn’t been active over the last 2 months. This could indicate a one-time operation or a relation to another group. Two of the victims are from Brazil, one from India and one from France.
The Arcus Media ransomware group, active since May 2024, is a relatively new threat actor known for its direct and double extortion methods. They gain initial access through phishing emails, deploy custom ransomware binaries, and use obfuscation techniques to evade detection.
Their tactics include phishing emails with malicious attachments, obfuscated scripts for executing payloads, and privilege escalation using tools like Mimikatz. The group attacks various sectors and countries; Brazil is the most targeted country to date, with 6 notable attacks. The most targeted sector is business services. The group admin is a threat actor who manages his account in the Exploit Russian hacking forum. This information, along with the actor’s name, could indicate the group’s location or political position in Russia.
According to our resources, this individual attacked the Republic Bank of Argentina only
once, in May 2024.
Brain Cipher is a recently launched ransomware operation that launched attacks on organizations globally earlier this month, June 2024. On June 20, 2024, Brain Cipher attacked Indonesia’s National Data Center (Pusat Data Nasional or PDN), disrupting various government services. This ransomware significantly impacted public services, including immigration processing at Jakarta’s Soekarno-Hatta International Airport, causing long queues and delays.
The attackers demanded a ransom of $8 million to decrypt the compromised data. Over 210 institutions, including national and local government offices, were affected. The encryptor is based on the leaked LockBit3.0 encryptor, which has been thoroughly analyzed. Unless Brain Cipher has modified the encryption algorithm, there are no known methods to recover files for free.
Massive police operation across Europe dismantles ransomware networks and results in 4 arrests. THE HAGUE, Netherlands (AP) – In the largest international operation ever against ransomware, police coordinated by the European Union’s justice and police agencies have dismantled computer networks responsible for spreading ransomware through infected emails.
The EU’s judicial cooperation agency, Eurojust, announced on Thursday that police arrested four “high value” suspects, dismantled over 100 servers, and seized control of more than 2,000 internet domains. This major operation, codenamed Endgame, involved coordinated efforts in Germany, the Netherlands, France, Denmark, Ukraine, the United States, and the United Kingdom.
According to Europol, three suspects were arrested in Ukraine and one in Armenia, and searches were conducted in Ukraine, Portugal, the Netherlands, and Armenia.
The UK, US, and Australia have revealed the identity of Dmitry Khoroshev, a Russian national and the
leader of the once-notorious LockBit ransomware group, following an international disruption campaign led by the National Crime Agency (NCA).
Dmitry Khoroshev, also known as LockBitSupp, who previously operated in secrecy and once offered a $10
million reward to anyone who could reveal his identity, is now facing sanctions announced by the FCDO in
coordination with the US Department of the Treasury’s Office of Foreign Assets Control (OFAC) and the
Australian Department of Foreign Affairs.
These sanctions include asset freezes and travel bans. Additionally, the US has unsealed an indictment against Khoroshev and is offering a reward of up to $10 million for information leading to his arrest or conviction.
These actions are part of an extensive investigation into the LockBit group conducted by the NCA, FBI, and other international partners forming the Operation Cronos taskforce.

A 22-year-old British national allegedly linked to the Scattered Spider hacking group and responsible for attacks on 45 U.S. companies has been arrested in Palma de Mallorca, Spain. The suspect is believed to be a leader of a cybercrime gang focused on stealing data and cryptocurrencies from organizations and extorting them to prevent the publication of sensitive data. Investigators report that the group stole $27,000,000 worth of cryptocurrencies using this scheme.
The arrest followed an investigation initiated by a tip from the FBI, which led to the issuance of an International Arrest Warrant (OID). The Spanish police arrested the suspect on May 31, 2024, at Palma airport as he was about to depart for Naples, Italy. During the arrest, his laptop and mobile phone were confiscated for forensic examination. Authorities have not yet disclosed details about the specific threat group, but VX-Underground alleges without confirmation that the suspect is “Tyler,” a SIM swapping
specialist from the notorious Scattered Spider group.
Scattered Spider is a loose-knit collective of English-speaking cybercriminals known for accessing their targets’ networks through social engineering, phishing, multi-factor authentication (MFA) fatigue, and SIM swapping. Some members of this group have also acted as affiliates with the Russian-speaking BlackCat ransomware gang. In September 2023, Scattered Spider breached entertainment giant MGM Resorts,
deploying a BlackCat/ALPHV encryptor, stealing data, and causing significant operational disruption.
The Ukraine cyber police arrested a 28-year-old Russian man in Kyiv for collaborating with the Conti and LockBit ransomware operations. He specialized in making their malware undetectable to antivirus software and conducted at least one attack himself. Supported by information from the Dutch police, the investigation linked the man to a ransomware attack on a Dutch multinational. He was arrested on April 18, 2024, as part of Operation Endgame, which targeted various botnets and their operators.
The suspect developed custom crypters to make ransomware payloads appear as safe files, selling these services to Conti and LockBit. The Dutch police confirmed his involvement in a 2021 ransomware attack using a Conti payload. During the arrest, authorities seized computer equipment, mobile phones, and handwritten notes. The investigation is ongoing, and the suspect, charged under Part 5 of Article 361 of the
Criminal Code of Ukraine, faces up to 15 years in prison.
Fall of Major Ransomware Groups Sparks Rapid Rise of New Threats. In 2023, international law enforcement agencies intensified their efforts against ransomware, resulting in the decline of groups such as Hive, Ragnar Locker, and thecollapse of ALPHV (BlackCat). These actions underscore the growing challenges faced by ransomware groups.
The significant February 2024 operation targeting LockBit, which included arrests and the seizure of data leak sites and servers, represents one of the largest law enforcement actions taken against a major ransomware operation.
Data from leak sites revealed the emergence of at least 25 new ransomware groups in 2023, highlighting the ongoing appeal of ransomware as a lucrative criminal activity. However, despite the appearance of new groups like Toufan, Darkrace, and CryptNet, many of these threat actors disappeared during the second half of the year.
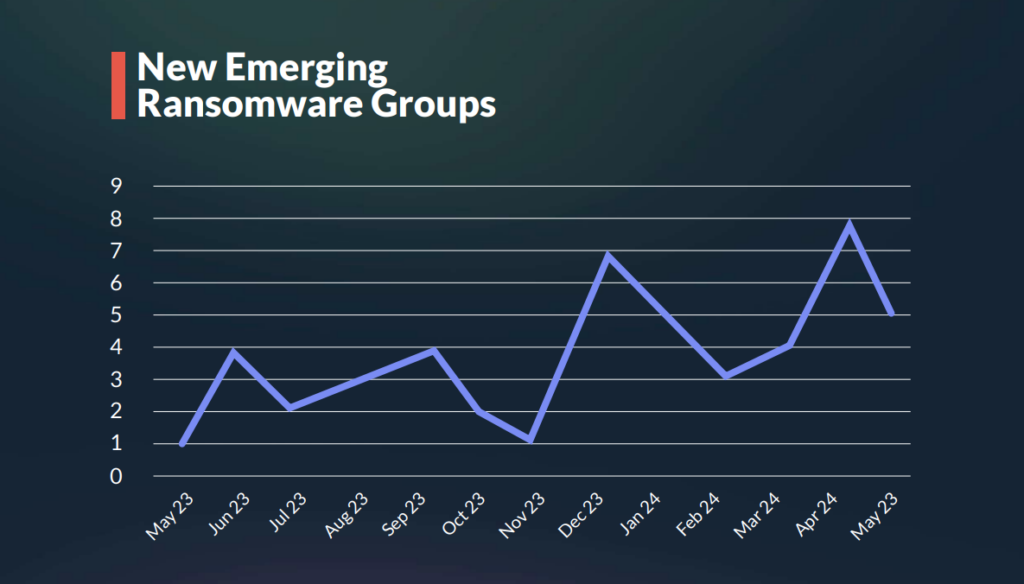
We are only at the end of the second quarter of 2024, and we’ve already seen 25 new ransomware groups posting at least one victim on their data leak site.
Keytronic, a major manufacturer of printed circuit board assemblies (PCBA), has confirmed a data breach after the Black Basta ransomware gang leaked 530GB of stolen data. Initially known for making keyboards and mice, Keytronic revealed in an SEC filing that a cyberattack on May 6 disrupted their operations, halting domestic and Mexican operations for two weeks. The attack resulted in the theft of personal information, which the company is now notifying affected parties and regulatory agencies about.
The SEC filing highlighted that the cyberattack and subsequent production loss will significantly impact Keytronic’s financial situation in the fourth quarter ending June 29, 2024. The company incurred approximately $600,000 in expenses to hire external cybersecurity experts, and this figure could continue to rise. While Keytronic did not name the perpetrators, Black Basta has claimed responsibility for leaking sensitive data, including employees’ passports, social security cards, customer presentations, and corporate documents.
At the beginning of June NHS England announced that the Synnovis ransomware attack forced multiple London hospitals to cancel hundreds of planned operations and appointments. Synnovis, a partnership between SYNLAB UK & Ireland, Guy’s and St Thomas’ NHS Foundation Trust, and King’s College Hospital NHS Foundation Trust, was locked out of its systems on June 3 by an attack linked to the Qilin ransomware group. This disruption significantly impacted procedures and operations, particularly blood transfusions and tests. Nevertheless, emergency services like A&E, urgent care centers, and maternity departments remained open.
The scale of the impact was revealed on Friday, with more than 800 planned operations and 700 outpatient appointments needing to be rescheduled across the two most affected trusts. Synnovis is working on restoring its IT systems, but full recovery will take time, causing ongoing disruptions in the coming months. Additionally, NHS Blood and Transplant (NHSBT) warned of blood shortages in London hospitals, urging O-positive and O-negative blood donors to help replenish reserves essential for urgent operations and
procedures. Despite the distress caused by these delays, patients are advised to keep their appointments unless notified otherwise.
The city of Wichita, Kansas revealed that it had to close parts of its network following a ransomware attack over the weekend. With a population of 400,000, Wichita ranks among the top 50 largest cities in the United States.
In a rare act of transparency, city officials confirmed that the attack occurred on Sunday, May 5th, when ransomware encrypted IT systems. To prevent further spread, the city promptly shut down its computer network. It remains unclear if any data was stolen, though ransomware groups typically exfiltrate
data from compromised networks before encrypting it.
Officials on the city of Wichita’s website stated, “We are conducting a thorough review and assessment, including evaluating any potential data impact. Such assessments take time.” BleepingComputer has confirmed that city services’ online payment systems, including water bills and court citations, are offline. Despite this disruption, first responders continue to operate, and the police and fire departments are implementing business continuity measures as needed.
While the specific ransomware gang responsible for the attack has not been disclosed, the city has notified local and federal law enforcement agencies, who are assisting in the response.
On June 20, the National Data Center (PDN) in Jakarta Indonesia suffered a ransomware attack, resulting in delays for airport immigration services and new student registration. The attackers are demanding a ransom of $8 million, approximately Rp 131 billion, to return the stolen data.
The ransomware used in this incident, known as Brain Cipher, is a new development of the LockBit 3.0 ransomware. In 2023, the LockBit hacker group also disrupted the systems of Bank Syariah Indonesia (BSI).
The cyber attack caused significant disruptions to the immigration office’s online services nationwide over the past week, as well as the online announcement of new student registration results (PPDB). According to data from IT security company Vaksincom, by mid-2024, 10 major institutions had been victims of ransomware attacks, including both private and government entities. These victims come from various sectors such as logistics, shopping centers, consumer finance, banks, financial services, IT services, transportation, and stock brokerage firms.
The first half of 2024 has shown a dynamic and volatile ransomware landscape. After a brief decline in Q1, Q2 saw a significant resurgence, with a 21.5% increase in attacks, reaching 1,277 cases. This rise is partly due to law enforcement interventions that fractured large ransomware operations, leading to more competition among smaller groups.
The emergence of 27 new ransomware groups underscores the evolving threat environment, posing fresh challenges to cybersecurity professionals. Notably, the top 10 ransomware groups accounted for 60% of all attacks, indicating a significant yet diversified influence within the ransomware ecosystem. Despite ongoing efforts to combat these threats, the United States remains the most targeted country, and the business services sector continues to be the most affected.
Veteran groups like LockBit3.0, Play, and RansomHub continue to dominate, while new groups such as ArcusMedia and APT73 point to persistent and growing dangers. The significant disruptions caused by these groups to major organizations like Keytronic and London hospitals demonstrate the devastating impact on global businesses and infrastructure.
Arrests and law enforcement actions have led to temporary disruptions to major players, as seen with LockBit3.0. However, the continued rise of new groups suggests that ransomware remains a lucrative and persistent threat. The arrests of high-profile figures and significant police operations signal progress and highlight the ongoing challenge of dismantling these networks.
Overall, the first half of 2024 has reaffirmed the resilience and adaptability of ransomware groups. Continued vigilance, international cooperation, and innovative cybersecurity measures are crucial in addressing the ever-evolving threat landscape.
2024 began with a decline in the frequency of ransomware attacks worldwide. However, these attacks still continues to pose the leading threat to both businesses and individuals.
While the numbers skyrocketed in Q4 2023 with 1309 cases, in Q1 2024, the ransomware industry was down to 1,048 cases. This is more than a 22% decrease in ransomware attacks compared to Q4 2023.
Two reasons for this drop could be the intervention of law enforcement, as observed with LockBit and ALPHV gangs, and the decrease in ransom payments, prompting ransomware groups to retire and seek alternative sources of income.
However, it is no surprise that the U.S. continues to be the country most targeted by ransomware, while the business services sector is the most targeted sector, similar to last year’s statistics.
There is no doubt that the new faces that were introduced to the industry, along with the ongoing attacks on businesses around the world, were able to claim many victims even though the number decreased. Combined with the consistency of the industry leader – LockBit3.0 – we saw devastating results for companies worldwide, such as Hyundai Motor, Duvel Beers, and others.
Furthermore, during this quarter, there numerous new ransomware groups emerged, a cautionary warning to businesses worldwide, as they could rise to prominence in the ransomware industry in the future.
As noted, the ransomware sector recorded 1,048 victims this quarter, marking a decrease of approximately 22% compared to the fourth quarter of 2023.
While it was a successful quarter for the entire ransomware industry, three families stood out. As expected, LockBit3.0 remains the most dominant ransomware group, with, they claim, 213 new victims, 20.6% of all ransomware cases.
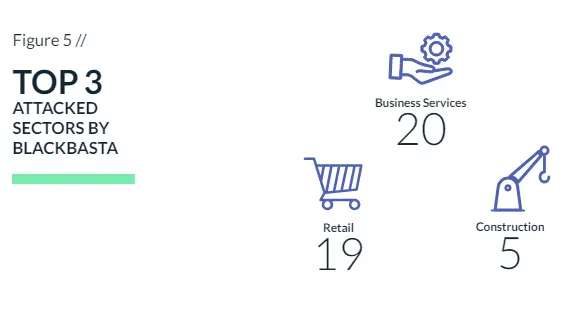
Coming in second is the Blackbasta group, which was able to claim a significant 75 victims.
In the current landscape, where ransomware groups are closing down their operations at a much quicker rate than previously observed, a group that consistently executes dozens of successful ransomwares attacks every month and has sustained its activities for over a year can rightfully be deemed a veteran. And the third place spot goes to another veteran − The Play group − with 74 victims this quarter.
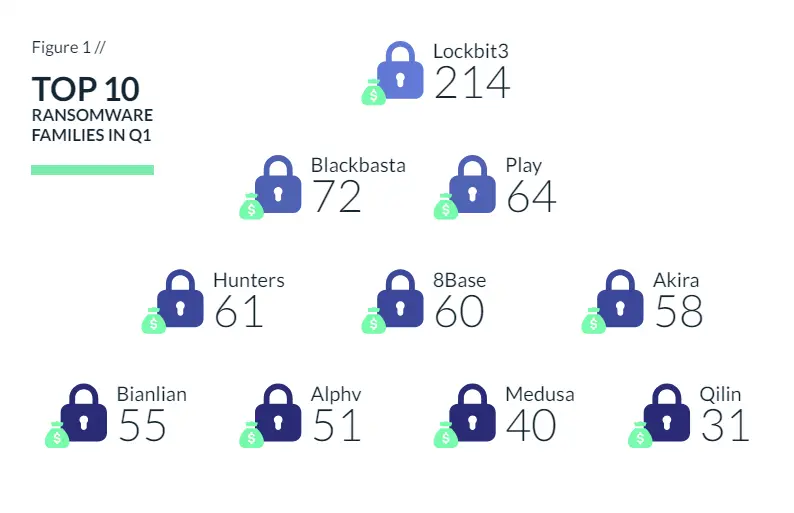
In February, an international operation culminated in the arrest of at least three associates of the infamous LockBit ransomware syndicate in Poland and Ukraine. Despite these arrests, the group continued its global onslaught against organizations, maintaining its position as a dominant force in the realm of ransomware operations. This resilience underscores the group’s formidable power and capabilities, as well as the robust security measures surrounding its operations that ensurs its continued viability and potentially promising future, as evidenced by quarterly trends over recent years

BlackBasta is a ransomware operator and criminal enterprise offering Ransomware-as-a-Service (RaaS), which surfaced in early 2022 and swiftly became one of the most prolific threat actors in the global RaaS landscape. Last month, the group successfully targeted automotive giant Hyundai, encrypting a significant volume of internal files. With ransom payments amounting to at least $107 million since its inception, the BlackBasta cybercrime syndicate shows no signs of slowing down, indicating its enduring presence and formidable status in the cybercriminal realm.

The ransomware syndicate responsible for numerous destructive assaults on significant American municipalities purportedly executed over 300 successful incidents since June 2022. Among the notable attacks this quarter was the breach targeting the Swiss government, where approximately 65,000 files were pilfered by the Play ransomware gang during an assault on an IT vendor. Like BlackBasta, there are no indications that this methodical group intends to halt its operations. An interesting point to note is that in January 2024, the group only managed to attack 3 victims, which is the lowest number in the past 2 years.
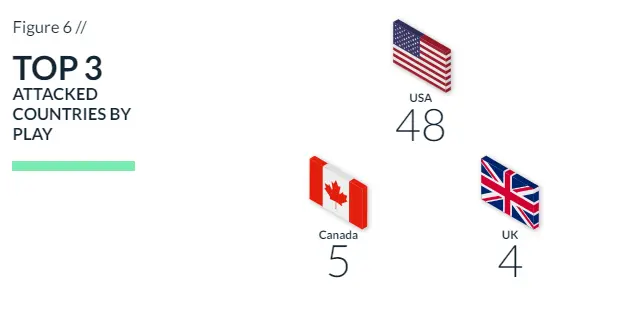
Regarding the most targeted countries (Figure 8), the U.S. remains the number one targeted country globally, with good reason. The number one economy in the world was the victim of ransomware attacks this quarter in 50.8% of the cases, amounting to 523 cases.

The second most targeted country this quarter is the United Kingdom, with 61 cases, far behind the U.S. Finally, Canada is in third place with 60 ransomware cases this quarter.
Even when focusing on the top three countries, we can see that there is no doubt that the U.S. is the most lucrative country for threat actors.
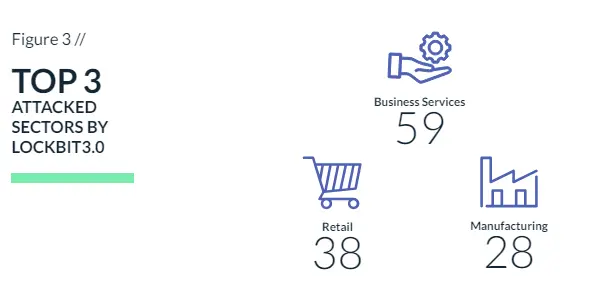
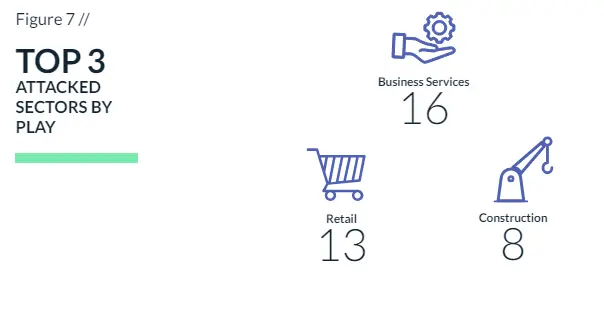
As expected, the business services sector is the most targeted sector in Q1, with 23.5% of the ransomware cases, followed by the retail and manufacturing sectors, with 16% and 14%, respectively (Figure 9).
The emergence of the Mogilevich group seemed sudden, as they promptly asserted control over major organizations including Epic Games, DJI, Shein, Kick, and others within a mere two weeks of their appearance. Despite their claims, both we and fellow researchers are doubtful about their successes due to the absence of evidence supporting these alleged breaches. None of the organizations mentioned reported any cybersecurity incidents, and there was a glaring lack of ransom notes, samples, analyses, or any public acknowledgment of such breaches or ransomware. In essence, there was a total absence of substantiation.
On March 2, 2024, doubts surrounding the group were confirmed when they revisited Epic Games, this time purportedly providing a data sample as evidence of a breach. However, this “data sample” turned out to be a confession admitting that the group were impostors rather than a legitimate Ransomware-as-a-Service (RaaS) entity (see their confession in the Ransom Notes section below). The individual(s) orchestrating this scheme, under the alias Pongo, confessed to fabricating false breaches to quickly garner attention and redirect victims to a scam.
On their “About” page, RansomHub identifies itself as a global team of hackers primarily motivated by financial gain. While this motive isn’t particularly surprising, the group claims to refrain from targeting certain entities.
On February 25, 2024, RansomHub made its debut with an attack on YKP, a Brazilian accounting and management firm, marking its first observed victim. Since then, four more victims fell prey to their ransomware in February, followed by an additional 13 victims in March.
Unlike the now-discredited Mogilevich scam, RansomHub provides data samples extracted by its affiliates, and in one instance, began releasing substantial volumes of data.
Trisec, a ransomware faction, announced its presence on the dark net leak site on February 17, declaring its initial victim: Cogans Toyota Cork, an Irish dealership. To date, the group has targeted a total of three victims.
Trisec diverges from conventional ransomware groups by openly aligning itself with a nation-state, notably, Tunisia, rather than Russia or China. The Tunisian flag prominently features in the group’s Telegram channels, and their leak site specifies a preference for hiring Tunisians.
A ransomware collective known as Slug has claimed responsibility for infiltrating and targeting AerCap as its inaugural public victim. According to cybersecurity analysts at Hackmanac, the perpetrators claim to have absconded with 1TB of AerCap’s data.
A new player in the ransomware arena, MyData / Alpha Locker, has emerged. An examination of their data leak site uncovers several companies victimized by the group, including Mike Ferry, A24Group, Accolade Group and its subsidiary Levelwear, Gadot Biochemical Industries, CARRI Systems, and Integrity. The exfiltrated data, dated 2023, points to the group’s ongoing activity.
Another ransomware entity, Blackout, has recently emerged. Its initial target was the ‘Centre Hospitalier d’Armentières’, where the group claims to have encrypted over 100 servers and workstations in the French medical institution’s local network, as well as exfiltrated a database containing records of over 900,000 patients. Additionally, Groupe M7 in Quebec fell victim to Blackout’s second attack, resulting in the extraction of 10 GB of internal documents and financial reports, alongside the encryption of several servers. The ransom demand for this incident expired on March 3rd.
Enterprises in the United States and Europe are on high alert due to the emergence of a new ransomware strain known as “DoNex,” actively compromising companies and claiming victims.
This new threat has cybersecurity experts scrambling to comprehend its full extent and devise countermeasures. The DoNex ransomware group has unveiled several companies as its victims on their dark web portal, accessible via the Onion network.
Employing a double-extortion method, the group not only encrypts files, appending them with a unique VictimID extension, but also exfiltrates sensitive data, using it as leverage to coerce victims into paying the ransom.
Affected companies discover ransom notes named Readme.VictimID.txt on their systems, directing them to initiate contact with the DoNex group via Tox messenger, a peer-to-peer instant messaging service known for its security and anonymity features.
In January 2024, Insane, or Going Insane, surfaced suddenly, targeting a victim in Thailand before vanishing just as quickly. The only information available about this “group” was posted on their data leak site. They claim to utilize AES encryption for their ransomware and purport to possess malware capable of stealing information. Researchers from Clipeus Intelligence suggest the creator may be of Russian origin.

LOCKBIT CYBERCRIME NETWORK FACES GLOBAL CRACKDOWN THROUGH INDICTMENTS AND ARRESTS
A multinational operation targeting the notorious LockBit ransomware gang has resulted in the apprehension of at least three affiliates in Poland and Ukraine.
The announcements of these arrests followed the shutdown of LockBit’s darknet platform, utilized by the group for issuing threats to victims and releasing compromised data unless ransom demands were met.
Ukrainian cyber police disclosed on Wednesday that they had detained a “father and son” duo allegedly affiliated with LockBit, whose activities purportedly impacted individuals, businesses, governmental entities, and healthcare establishments in France.
During searches of the suspects’ residences in Ternopil, Ukraine, law enforcement seized mobile phones and computer equipment suspected to have been utilized in cyberattacks.
In Poland, authorities arrested a 38-year-old individual in Warsaw, suspected of being associated with LockBit. He was brought before the prosecutor’s office and charged with criminal offenses. As evident, these occurrences did not impede the largest existing ransomware operation, as the attacks continue at the same pace. The significance of the LockBit gang likely extends beyond just three arrests, indicating that stopping their operations will demand considerable effort.
NEW TRENDS
RECORD LOW RANSOMWARE PAYMENTS REPORTED AS VICTIMS REJECT RANSOM DEMANDS
In the last quarter of 2023, the proportion of ransomware victims complying with ransom demands plummeted to a historic low of 29%, as per data from ransomware negotiation firm Coveware.
Coveware attributes this continuous decline to several factors, including enhanced preparedness among organizations, skepticism towards cybercriminals’ assurances to not disclose pilfered data, and legal constraints in regions where ransom payments are prohibited.
Not only has there been a decrease in the number of ransomware victims making payments, but there has also been a notable decline in the monetary value of such payments.
Coveware notes that in Q4 2023, the average ransom payment amounted to $568,705, marking a 33% decrease from the preceding quarter, with the median ransom payment standing at $200,000.
The Duvel Moortgat Brewery, renowned for its iconic Belgian beer brand, including the celebrated strong and fruity golden pale ale of the same name, fell victim to a BlackBasta ransomware assault. On March 7, a spokesperson for the company informed local media that their automated threat detection systems had flagged the ransomware attack.
Ellen Aarts, communications manager at Duvel Moortgat, stated, “At 1:30 AM last night, alarms went off in Duvel’s IT department because ransomware was detected. Consequently, production was promptly halted. The timeline for its resumption remains uncertain. We are aiming for a restart either today or tomorrow.”
Aarts also mentioned that despite not having an accurate estimate for the return to normal production operations, their warehouses are adequately stocked, ensuring minimal impact on distribution. The company did not specify whether the cyberattack affected production at Duvel’s primary brewery in Breendonk only or extended to other facilities in Antwerp, Oudenaarde, and Achouffe as well.
Hyundai Motor Europe, the European division of car manufacturer Hyundai Motor Company based in Germany, fell victim to a BlackBasta ransomware attack, with threat actors asserting possession of three terabytes of corporate data.
According to reports, in an image obtained by BleepingComputer, the attackers disclosed lists of folders purportedly pilfered from multiple Windows domains, including those associated with KIA Europe. While the exact nature of the stolen data remains undisclosed, the folder names suggest its affiliation with various departments within the company, encompassing legal, sales, human resources, accounting, IT, and management.
The LockBit ransomware syndicate has taken responsibility for the recent cyber assault on Fulton County, Georgia, issuing threats to disclose “privileged” documents unless a ransom is paid. With a population exceeding one million, Fulton County is Georgia’s largest county and houses the state capital, Atlanta.
Over the last weekend in January, hackers infiltrated the county’s systems, causing extensive IT disruptions affecting telecommunications, judiciary proceedings, and taxation services. Nearly three weeks after the breach, the county’s official website continues to display an initial alert regarding the system outage, redirecting visitors to the latest update from February 5.
Telephony services have been partially restored, but the property tax system remains offline, hindering payment processing and other transactions. Residents encounter challenges in water billing due to the unavailability of electronic payments, although penalties for delays are waived.
Officials have noted delays in justice system services, while affirming that email services remain unaffected.
The ransomware industry remains the number one threat to organizations worldwide. As this quarter ended, supply chain attacks became a solid technique for the mature and experienced ransomware groups.
In addition, this quarter showed us the faces of new ambitious groups that look to put their mark on the ransomware industry. More than usual, we saw more than 10 new Ransomware groups!
LockBit3.0 remains the ruler of the industry, far ahead of the other groups, in spite of the arrests that affected the group in February. Although we have seen increased activity by law authorities worldwide this quarter, this industry keeps on thriving despite their efforts.
It would be nice if ransomware attackers announced their identities, motives and strategies publicly. But they don’t. Unlike legitimate businesses, ransomware groups issue no quarterly reports or press conferences.
They do, however, elicit plenty of information that skilled analysts can use to establish a profile of their operations, then leverage that data to mitigate threats. That’s what we do all day long at Cyberint.
To learn more about how our threat intelligence research helps protect businesses against ransomware and other risks, request a demo.

©1994–2026 Check Point Software Technologies Ltd. All rights reserved.
Copyright | Privacy Policy | Cookie Settings | Get the Latest News
Fill in your business email to start


