2023 is considered the most successful year for ransomware groups in history.
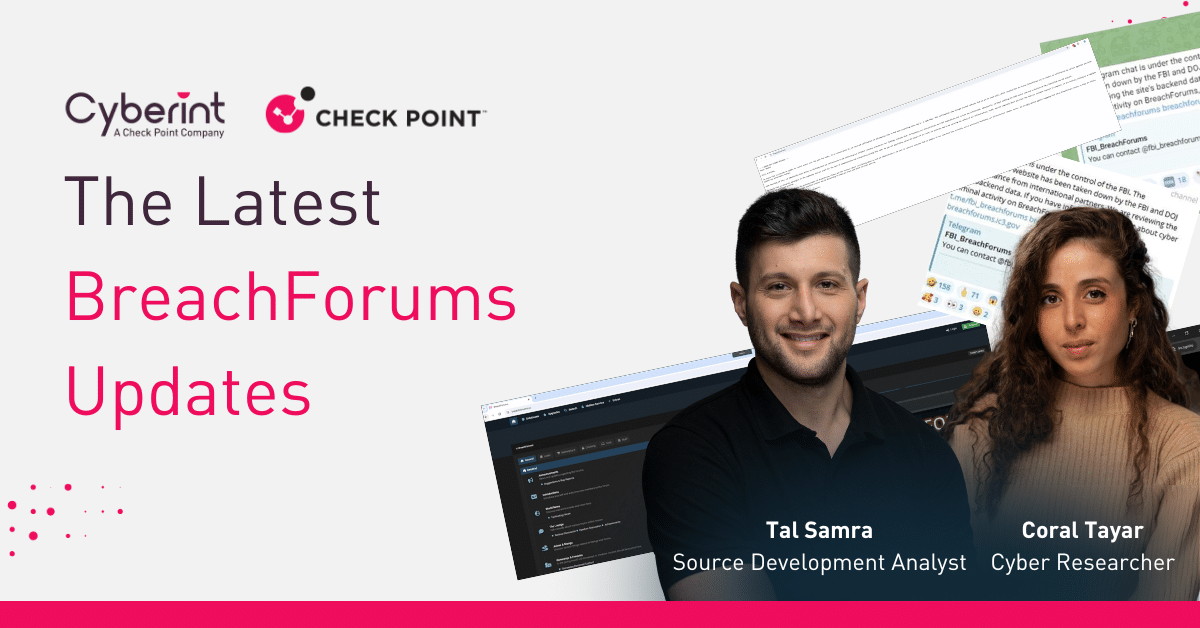
In 2023, ransomware groups saw unprecedented success, with a 55.5% surge in victims, totaling 5,070 a stark rise from the previous year. Q2 and Q3 alone claimed more victims than the entire 2022, with 2903 victims. Ransomware leaders remain the veterans, LockBit3.0, ALPHV and Cl0p.
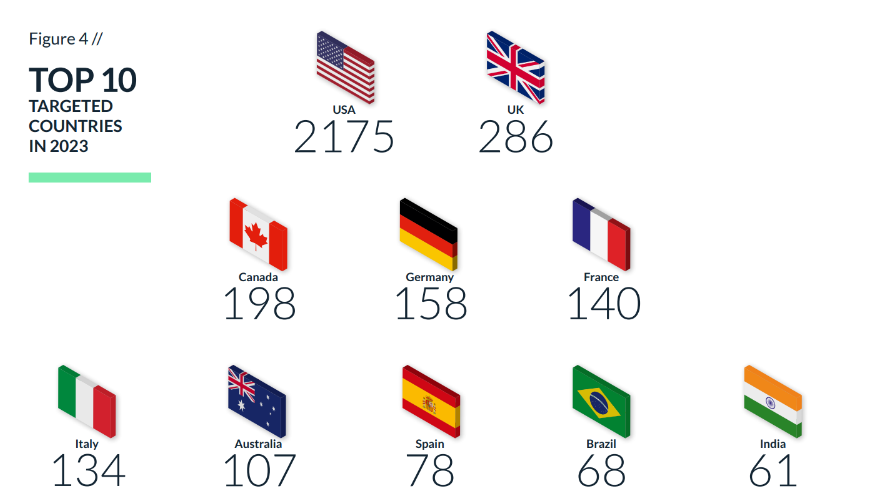
Without a doubt, the MOVEit campaign will be remembered as the most successful campaign this year, teaching us the importance of supply chain attacks, version control and the importance of understanding our attack surface. The USA was the most targeted country (49.8%, up from 38% in 2022) followed by the U.K. and Canada. The most targeted sector was business services, with 1265 cases, followed by retail and manufacturing.
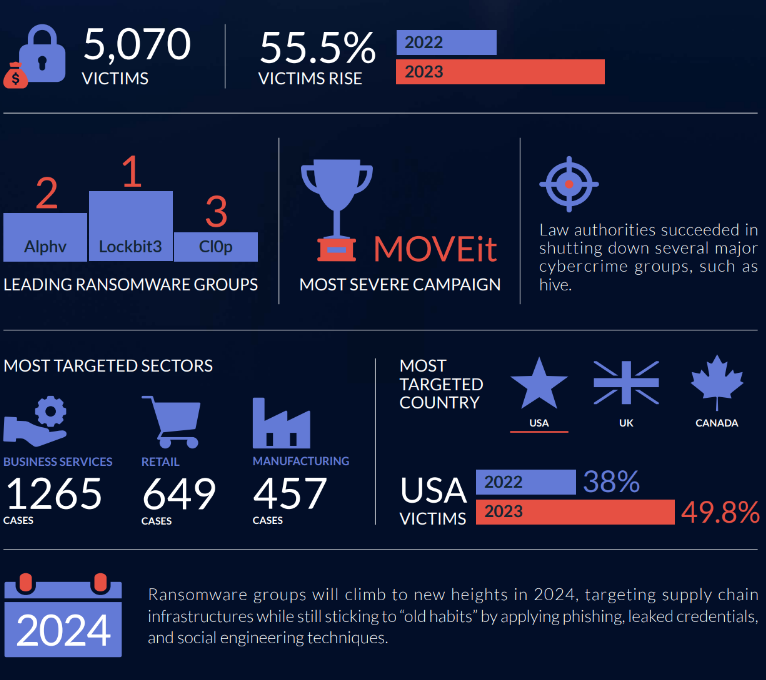
In the fourth quarter of 2023, we documented 1,309 ransomware incidents globally. As illustrated in the graph below, the LockBit group continues to dominate ransomware group attacks, recording a total of 243 successful incidents. Following closely in second place is the PLAY group, which executed ransomware attacks on 110 different organizations. Notably, nearly 40% of their attacks were carried out in the fourth quarter alone.
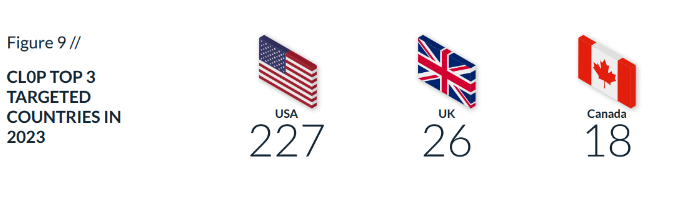
It is worth mentioning that the CLOP gang did not make it to the top 10 list for the quarter despite being among the top 3 in the year’s overall totals. Since the notable MOVEIt breach orchestrated by the CLOP gang, there has been no observed activity from the group. However, despite missing an entire quarter, Cl0p is the third most active group in 2023, which shows us the scale of the MOVEit campaign.
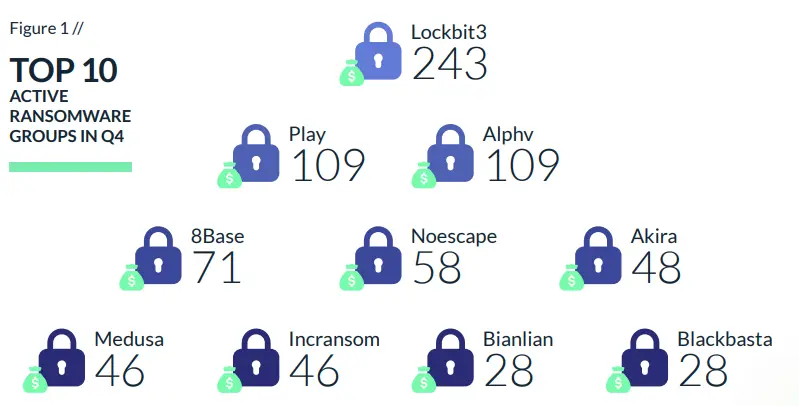

In the year 2022, a total of 2,809 ransomware attacks were recorded globally. However, in 2023, there has been a significant surge, with the total number of ransomware attacks reaching 5070, marking a substantial increase of >55%.
This significant shift is spearheaded by established cybercrime groups like LockBit and Clop, with additional momentum coming from emerging ransomware gangs such as 8Base, BianLian, Play, Akira, and others. The substantial increase can be largely attributed to the CLOP group, which executed attacks at a higher frequency compared to the previous year, rapidly securing a position among the top three ransomware groups by attack count.
When examining the Top 10 Countries most impacted by ransomware attacks, notable shifts are not apparent. The United States maintains its leading position, accounting for approximately 49.8% of all ransomware attacks. Following a pattern similar to the previous year, the United Kingdom, Canada, France, and Germany secured the next positions in the Top 5, with a considerable gap from the United States.
In a noteworthy change, India has unfortunately entered the top 10, displacing Russia from the previous year. This change could be attributed to the ongoing conflict between Russia and Ukraine, which garnered significant attention last year and involved ransomware groups from both sides, resulting in an escalation of attacks on the Russian front. With a relative de-escalation in cyber warfare activities between the two nations this year, India has taken Russia’s side, experiencing increased ransomware attacks on its behalf.
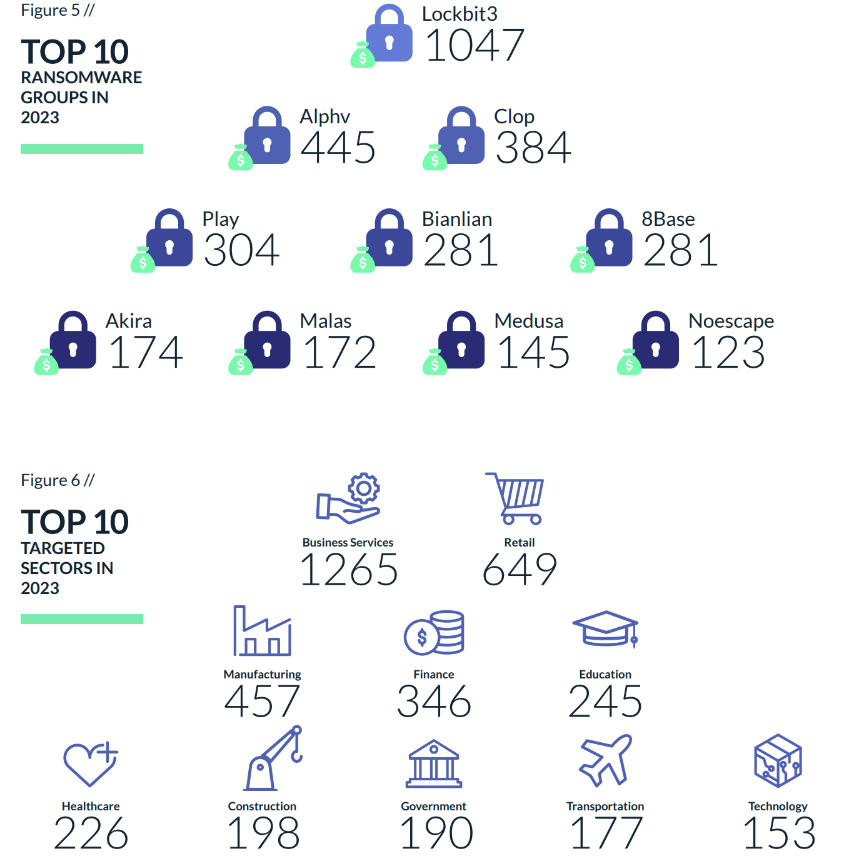
Emerging in September 2019, the LockBit Ransomware Group claimed the title of the most active ransomware group in 2022 following the shutdown of Conti. Throughout 2023, LockBit maintained its prominence as the most active ransomware group. This year, LockBit achieved successful attacks on approximately 1047 victims, contributing to over 24% of the total ransomware attacks monitored by Cyberint in 2023.

On December 19, 2023, the FBI successfully dismantled one of the ALPHV/BlackCat ransomware sites. The main page now bears the customary FBI banner, while other sites linked to the cybercrime gang remain operational. Although the FBI’s action disrupted ALPHV, it is unlikely to completely halt the ransomware gang. Financially robust players like ALPHV can endure idle periods, and ransomware groups facing shutdown often resurface as entirely new entities or collaborate with existing groups. The comeback occurred swiftly when the group targeted two organizations at the end of December.
This year, ALPHV achieved successful attacks on approximately 445 victims, accounting for over 10% of the total ransomware attacks monitored by Cyberint in 2023.

Since February 2019, Clop attacks have been on the rise, persistently harming organizations worldwide in 2023. This year, Clop achieved successful attacks on approximately 384 victims, representing over 8% of the total ransomware attacks monitored by Cyberint in 2023.
At the end of 2022, new ransomware families emerged and older ones intensified their attacks in 2023. Notable among them were the 8base and Play ransomware families.
Initiating operations in April 2022, 8Base is a ransomware collective that swiftly gained a reputation for its forceful strategies and a substantial volume of victims despite its relatively short time in the cyber landscape. In 2023, the group achieved significant milestones, conducting attacks on 281 organizations, with 40% of their focus on the United States.
First observed around June 2022, the Play ransomware gang, responsible for devastating attacks on major American cities, allegedly launched more than 300 successful incidents since June 2022. In this year alone, the group executed 304 attacks, with more than 50% targeting organizations in the United States.
The Rhysida ransomware group came into the spotlight around May-June 2023 when they introduced a victim support chat portal accessible through the TOR (.onion) site. The group portrays itself as a “cybersecurity team,” claiming to be acting in its victims’ best interests by targeting their systems and drawing attention to the purported security vulnerabilities and their potential consequences.
The Rhysida ransomware group has gained notoriety due to a series of attacks on healthcare institutions, prompting government agencies and cybersecurity firms to intensify scrutiny of the group’s activities. In June, Rhysida first garnered attention when it publicly disclosed documents stolen from the Chilean Army (Ejército de Chile) on its data leak site.
In 2023, the Rhysida ransomware group made headlines with multiple significant attacks. They targeted high-profile entities, including the British Library, where they conducted a cyber-attack, causing a major technology outage and selling stolen personal information online. In the US, Rhysida attacked Prospect Medical Holdings, impacting the healthcare sector, and compromised Insomniac Games, a Sony-owned video game developer, showcasing their broad reach across diverse industries.
MalasLocker emerged in March 2023 and adopted an unconventional approach by promising a charitable donation in exchange for providing decryption tools and preventing data leaks. This departure from typical ransom demands casts them as digital activists against corporate entities and economic inequality. Despite their claims, it’s unclear if they follow through on decryption after receiving proof of donations.
Focusing primarily on the Business Services, Software, and Manufacturing sectors, with a significant emphasis on Professional, Scientific, and Technical Services, MalasLocker targets companies mainly located in Italy, Russia, and the United States. Their attacks involve breaching Zimbra servers, encrypting data, and uploading suspicious JSP files to specific directories.
Akira is offered as a ransomware-as-a-service and was discovered in March 2023. Preliminary research suggests a connection between the Akira group and threat actors associated with the notorious ransomware operation Conti.
This ransomware, identified as having an impact on both Windows and Linux systems, operates by exfiltrating and encrypting data, coercing victims into paying a twofold ransom to regain access and restore their files.
The collective responsible for this ransomware has already directed its attention towards numerous victims, primarily focusing on those in the U.S. Furthermore, the group operates an active leak site for the Akira ransomware, where they publish information, including their latest data breaches.

BlackSuit, a newly identified ransomware group resembling the notorious Royal ransomware, has posed a significant threat to the Healthcare and Public Health (HPH) sector since its emergence in May 2023. Exhibiting strong connections to Royal and the now-defunct Conti, known for aggressive targeting in this sector, BlackSuit’s affiliation raises concerns. While their victim count is limited, their attacks have impacted the United States, Canada, Brazil, and the United Kingdom across industries like healthcare, manufacturing, business technology, retail, and government.
Notably, a U.S.-based medical services provider to numerous hospitals faced severe disruptions, reflecting potential widespread consequences. Employing a double extortion method, BlackSuit encrypts sensitive data and demands ransoms, with detections in various sectors, highlighting it’s evolving threat. Operating independently, BlackSuit’s distribution methods include infected email attachments, torrent websites, malicious ads, and Trojans.
3AM, a recently surfaced ransomware discovered in August 2023, has seen limited usage but showcased a noteworthy incident where it was employed as an alternative to LockBit after the latter was blocked. Coded in Rust, marking it as a distinct malware family, 3AM follows a distinct sequence, targeting services before encrypting files and attempting to delete Volume Shadow copies. The group behind 3AM publicly revealed leak sites, listing victims from the United States and Malaysia, a move that raises speculation about their intentions.
2023 provided us with some notable campaigns that, unfortunately, caused major damage to organizations worldwide. While MOVEit was the most devastating one, some other campaigns are worth mentioning.
The ongoing MOVEit campaign remains a prominent fixture in headlines, continually ensnaring new victims as it unfolds. This expansive campaign is a stark illustration of the potency of a supply chain attack, impacting many global companies. MOVEit, an instrumental managed file transfer (MFT) software employed widely across healthcare, finance, technology, and government sectors, touts its security through encryption and robust file transfer protocols for safe data exchange within and between teams and organizations.
However, within this seemingly secure software lie discovered vulnerabilities, exposing a path to remote code execution and potential data breaches. These loopholes have been exploited by the Cl0p ransomware group, tracing back to their exploitation of the MOVEit vulnerability since 2021, with evident attempts to extract data in 2022.
Cl0p, renowned for their adeptness at zero-day exploits such as the Accellion File Transfer Appliance (FTA) attacks in 2020 and 2021 and the targeting of GoAnywhere MFT servers in early 2023, has disclosed various compromised victims through the MOVEit flaw. Noteworthy companies like Norton, EY, and Zellis fell prey to this assault.
This extensive cyber incursion caused a ripple effect, impacting major entities to such an extent that the US government has offered a substantial reward for any information that links Cl0p’s actions to a foreign government.
Despite Cl0p’s claims of data deletion from specific sectors such as governments, the military, and children’s hospitals, their breach affected several US federal government agencies. The scale and repercussions of this attack continue to reverberate, with the Cl0p gang’s actions drawing widespread attention and scrutiny, signifying the severity and depth of the MOVEit ransomware breach.
The City of Dallas fell victim to a ransomware attack orchestrated by the Royal gang on May 3, triggering extensive network disruptions that compelled Dallas courts to remain shuttered until May 31. The Royal operators initially infiltrated the city’s network by pilfering service account credentials, maintaining a persistent presence for a month before deploying the ransomware. Restoration efforts commenced on May 9 and concluded by June 13.
In the wake of this disruptive attack, the Dallas City Council sanctioned an $8.5 million budget for mitigation and recovery endeavors. Expenditures encompassed external cybersecurity expertise, identity theft and fraud protection, and breach notification services.
The City of Dallas publicly acknowledged the ransomware intrusion in May, highlighted by the unusual printing of ransom notes from network printers, unequivocally attributed to the Royal ransomware group. In their blog post, the Royal ransomware gang threatened to expose sensitive information, encompassing employee details, court cases, prisoner data, medical records, client information, and governmental documents.
The ramifications were far-reaching, affecting various city services and departments, including the Dallas police department, 311 customer service app, courts, water utilities, code compliance services, animal services, secretary’s office, and development services. Subsequent reports from the Attorney General’s office in August indicated that 26,212 individuals bore the brunt of the breach, exposing personal details such as names, addresses, social security numbers, and medical and health insurance information. Further investigation pushed the tally of affected individuals to 30,253, amplifying the gravity and scope of the breach.
In September 2023, two major hotel and casino giants in Las Vegas, MGM Resorts International and Caesars Entertainment, fell victim to ransomware attacks. MGM Resorts encountered a “cybersecurity issue” that led to the shutdown of U.S. systems, impacting numerous MGM hotels and disrupting vital services like the company’s website, app, reservations, ATMs, slot and credit card machines.
While sensitive financial data remained secure, personal information, including names, contact details, driver’s license and Social Security numbers, and passport details of pre-March 2019 customers were compromised, with a projected cost of around US$ 100 million. In contrast, Caesars Entertainment saw limited service disruption but suffered data theft from its loyalty program database, affecting 41,397 Maine residents.
Scattered Spider ransomware group claimed responsibility, absconding with 6 terabytes of data. MGM declined ransom payment, working on recovery, while reports indicated Caesars paid 15 US$ million of the demanded 30 US$ million ransom for data protection.
In March, Western Digital encountered a ransomware attack linked to the ALPHV/BlackCat ransomware group, which they disclosed on April 3. Responding swiftly, they activated their protocols, restoring affected services and engaging law enforcement. The aftermath involved data theft and service disruptions affecting platforms like SanDisk and My Cloud, impacting customer access.
BlackCat, a notable ransomware group in 2023, claimed responsibility for leaking alleged stolen data publicly on April 28, employing aggressive tactics such as sharing purported footage from a Western Digital video conference. Western Digital acknowledged the leaked data on May 5 and confirmed an ongoing investigation into these claims.
In early 2023, Royal Mail experienced a significant ransomware attack orchestrated by the LockBit group. The attack, involving LockBit’s encryptors, severely disrupted Royal Mail’s international shipping capabilities for approximately six weeks. LockBit initially demanded a ransom of £65.7 million ($79.85 million) for the return of stolen data.
Royal Mail, however, chose not to comply with these ransom demands, which were considered “absurd” by its directors. In response, LockBit published 44 gigabytes of Royal Mail’s stolen data on the dark web in an attempt to extort money. Despite this pressure, Royal Mail maintained its stance against paying the ransom. The financial impact on Royal Mail was significant, with substantial costs incurred for recovery from the attack.
Meanwhile, LockBit continued its extortion attempts, reducing the ransom demand to £33 million, a decrease from the original £65 million. Royal Mail maintained its stance against paying the ransom. The company’s decision not to comply with the ransom demands led to LockBit publishing the stolen data on the dark web.
2023 is a new all-time high for the ransomware industry. With permanent families such as LockBit ALPHV and Cl0p, this industry caused severe damage to organizations worldwide. In addition to that, the newcomers this year were introducing quality tools and products that helped them become permanent threats as well.
Although law authorities worldwide are still doing their best to stop this menace from continuing to evolve, the industry is still growing rapidly.
Read on for a detailed breakdown Quarter by Quarter ↓

Fill in your business email to start.
Q3 will be remembered as a new record for the ransomware industry as it was the most successful quarter ever recorded.
While the number skyrocketed in Q2 with 1386 cases, in Q3, the ransomware industry was able to surpass this number with 1420 cases.
With no surprise, the U.S. continues to be the most targeted country by ransomware, while the business services sector is the most targeted sector.
There is no doubt that the new faces that were introduced to the industry, along with the MOVEit campaign, were able to claim many victims. This, combined with the consistency of industry leader LockBit3.0, meant devastating results for companies worldwide.
As mentioned, the ransomware industry claimed 1420 victims this quarter, the highest number of victims ever recorded in one quarter.
While it was a successful quarter for the entire ransomware industry, three families were far ahead of the pack. As expected, LockBit3.0 remains the most dominant ransomware group with 252 new victims, 17.7% of all ransomware cases.
Coming second is Cl0p Ransomware, which was able to claim a significant number of victims − 177. An important note here is that although Cl0p claimed 177 victims, this was only in two out of the three months of the quarter, as they haven’t announced any victims for September.
Number three is the veteran group ALPHV with 120 victims this quarter.
Regarding the most targeted countries (Figure 2), the U.S. remains the number one targeted country in the world, with good reason. The world’s leading economy, it was the victim of 51% of this quarter’s ransomware attacks − 575 cases.
The second most targeted country this quarter is the United Kingdom, with 77 cases, far behind the U.S. Finally, we have Canada in third place with 48 ransomware cases this quarter. Even when focusing on the top three countries, we can see that there is no doubt that the U.S. is the most attractive country to threat actors.
As expected, the business services sector was the most targeted sector in Q3, with 42% of the ransomware cases, followed by the manufacturing and the retail sectors, with 19% and 12%, respectively (Figure 3).
The Rhysida ransomware group came into the spotlight around May-June 2023 when they introduced a victim support chat portal accessible through the TOR (.onion) site. The group portrays themselves as a “cybersecurity team” claiming to be acting in their victims’ best interests by targeting their systems and drawing attention to the purported security vulnerabilities and their potential consequences.
The Rhysida ransomware group has gained notoriety due to a series of attacks on healthcare institutions, prompting government agencies and cybersecurity firms to intensify their scrutiny of the group’s activities. Earlier in June, Rhysida first garnered attention when it publicly disclosed documents stolen from the Chilean Army (Ejército de Chile) on its data leak site.
Rhysida ransomware mostly targets the U.S., with 31% of its victims. In addition, it also ran successful campaigns in the UK, Italy and France. As for the target sectors, it seems that Rhysida had the most success in the business services sector, which comprises 51% of their campaigns.
A newly discovered ransomware strain named 3AM has emerged, but its usage has been limited thus far. One interesting attack that was discovered was when a ransomware affiliate tried to deploy LockBit on a target’s network but switched to 3AM when LockBit was blocked.
3AM is coded in Rust and appears to be an entirely new malware family. It follows a specific sequence: It attempts to halt multiple services on the compromised computer before initiating the file encryption process. After completing encryption, it tries to erase Volume Shadow (VSS) copies. Any potential links between its authors and known cybercrime organizations remain unclear.
The threat actor’s suspicious activities began with the utilization of the gpresult command to extract policy settings enforced on the computer for a specific user. They then executed various components of Cobalt Strike and made efforts to elevate privileges on the computer using PsExec.
Then the attackers conducted reconnaissance through commands such as whoami, netstat, quser, and net share. They also attempted to identify other servers for lateral movement using the quser and net view commands. In addition, they established a new user account to maintain persistence and employed the Wput tool to transfer the victims’ files to their FTP server.
On September 14, the 3AM (ThreeAM) Ransomware group made their leak sites public and included six organizations on their list of victims. These organizations consisted of five from the United States and one from Malaysia. It remains uncertain whether this development was an intentional publicity move or merely a coincidental occurrence for this group, which had only recently come to the researchers’ attention.
On September 7, the United States Department of Treasury and the United Kingdom Foreign Office jointly declared sanctions against 11 individuals, accusing them of being linked to the Trickbot cybercriminal group. Additionally, the US Department of Justice revealed indictments against nine individuals said to have ties to Trickbot and its affiliated entity, Conti. Notably, seven of the individuals named in the sanctions were also included in the list of those facing indictments.
The Department of Justice has unveiled three indictments, and among those charged is Galochkin. One of these indictments, filed on June 15 in the Northern District of Ohio, accuses him and ten other purported Trickbot members of conspiring to employ the Trickbot malware for personal gain, as well as personal and confidential data, from unsuspecting victims. These victims include businesses and financial institutions both within the United States and across the globe, with the illicit activity commencing in November 2015.
In an indictment filed in the Middle District of Tennessee, on June 12, Galochkin and three additional individuals were charged with using Conti ransomware. These charges stem from attacks aimed at “businesses, nonprofits, and governments in the United States” spanning from 2020 to June 2022.
Furthermore, an indictment filed in the Southern District of California on June 14 implicates Galochkin in connection with the Conti ransomware attack on Scripps Health that occurred on May 1, 2021.
Ashley Liles, a 28-year-old former IT employee, has received a prison sentence of more than three years for his involvement in an extortion attempt against his employer during a ransomware attack.
Liles, who previously worked as an IT security analyst at a company based in Oxford, abused his position to intervene in a ransomware payment following an attack on his employer.
In an attempt to deceive the company, he posed as the ransomware group that was extorting them. His scheme involved trying to divert the ransom payments by changing the cybercriminals’ cryptocurrency wallet to one that he controlled.
He accessed the private emails of a board member on more than 300 occasions and also tampered with the original blackmail email, changing the payment destination specified by the initial attacker. Furthermore, he established an email address that closely resembled the one used by the attackers and used it to exert additional pressure on his employer, with the aim of ensuring that the ransomware gang’s demands would be met, and the ransom paid.
However, the company did not comply with the demands of the attackers. During this time, internal investigations revealed that Liles had been accessing confidential emails without authorization while using his home internet connection.
Although Liles took measures to erase all data from his personal devices once he became aware of the ongoing investigations, the cybercrime team from SEROCU seized his computer and successfully recovered damning evidence.
Initially, Liles vehemently denied any involvement, but during a recent court hearing at Reading Crown Court, he pleaded guilty, five years after the events in question.
As a result, Liles was sentenced to three years and seven months in prison for charges related to blackmail and unauthorized computer access with the intent to commit other offenses.
Abyss Locker is a ransomware group that emerged relatively recently. Its activities are believed to have commenced in March 2023. Their modus operandi resembles that of other ransomware operations, involving the infiltration of corporate networks, data exfiltration for double extortion purposes, and the encryption of devices within the network.
The Abyss Locker campaign is the most recent example of the trend where ransomware operators have developed a Linux encryptor designed specifically to target VMware’s ESXi virtual machine platform in their attacks on businesses.
As organizations increasingly adopt virtual machines to enhance resource management, performance, and disaster recovery, ransomware groups have adapted by creating encryptors tailored to these platforms.
Given that VMware ESXi is among the most widely used virtual machine platforms, nearly every ransomware gang has started releasing Linux encryptors with the capability to encrypt all virtual servers hosted on these devices.
Ransomware threat actors are now spending less time operating within compromised networks before security solutions detect their presence. During the first half of this year, the median dwell time for hackers decreased from nine days in 2022 to just five days.
Upon cross-referencing our ransomware family statistics, encompassing all attacks monitored by Cyberint, with data provided by cybersecurity company Sophos, a noteworthy trend emerged. The median dwell time for cyberattacks, encompassing the entire spectrum of incidents, exhibited a decline from ten days in 2022 to a reduced eight-day timeframe during the first half of this year. Furthermore, it became evident that ransomware attacks accounted for approximately 70% of the total cyberattacks reported during this period.
From our findings and Sophos’ as well, we can indicate that while ransomware attackers act swiftly with a median dwell time reduction from 11 to 13 days this year, other cybercriminals conducting network intrusions tend to prolong their presence, waiting for the right moment.
Across all cases, the average dwell time hovers at 15-16 days, with the longest observed dwell time this year exceeding three months. Interestingly, data theft is becoming less common, as there were fewer such attacks, dropping to 31.58% in H1 2023 from 42.76% in 2022. This trend is supported by an uptick in incidents where it was confirmed that no data was exfiltrated, rising from 1.32% to 9.21%.
Our data reveals intriguing trends when examining the timing of cyberattacks. According to the stats, we suggest that threat actors, including ransomware groups, tend to target organizations more frequently on Tuesdays, Wednesdays, and Thursdays.
PurFoods, operating under the name Mom’s Meals, reported a data breach in the Maine Attorney General’s Office. The breach involved the unauthorized access of sensitive information, including personal identifiers such as names, financial account numbers, payment card (credit or debit) details, security codes, and account passwords or PINs.
The company first detected “suspicious account behavior” on February 22, 2023. Subsequent investigation revealed that PurFoods had experienced a cyberattack between January 16, 2023, and February 22, 2023. During that attack, certain files on their network were encrypted. Although it couldn’t be definitively determined if data was extracted from their servers, the possibility couldn’t be ruled out.
PurFoods engaged third-party experts to conduct a review of the potentially compromised data, which concluded on July 10, 2023. This review revealed that the files in question contained personal and protected health information of specific individuals. The potentially exposed information included names, Social Security numbers, driver’s license or state identification numbers, financial account and payment card information, medical and health data, as well as birthdates.
The company initiated the notification process for affected individuals on August 25. According to official records, approximately 1,237,681 people may have been impacted by this security incident.
In a recent cybersecurity incident, the Sri Lankan government suffered a significant data loss as a result of a ransomware attack. The attack targeted Sri Lanka’s government email network, impacting thousands of email accounts, including those belonging to high-ranking government officials. The attack, which commenced at the end of August, affected nearly 5,000 email addresses utilizing the gov[.]lk email domain, with the council of ministers, a central government body, among the victims.
The targeted system, known as the Lanka Government Cloud (LGC), was subjected to encryption, along with its backups. While officials managed to restore the LGC system within 12 hours of the attack, they were unable to recover backups from the period between May 17 and August 26. Consequently, all affected accounts lost data for that duration, as stated by Mahesh Perera, the head of Sri Lanka’s Information and Communication Technology Agency (ICTA).
In response to the incident, Sri Lanka’s computer emergency response team (CERT|CC) launched an investigation and is actively working on data recovery efforts. Perera has emphasized that the government has no intention of negotiating with the attackers or paying a ransom to retrieve the lost data.
The identity of the hacking group responsible for the attack remains unknown. It is suspected that the attackers may have gained access to the targeted system by distributing malicious links to government employees. It is likely that they exploited a vulnerability in an outdated version of Microsoft Exchange that had not been updated.
Notably, the Sri Lankan government has previously faced criticism for its lack of cybersecurity focus. The country lacked a dedicated cybersecurity authority until June 2023 when cybersecurity legislation was introduced.
Starting on May 27, the Clop ransomware group initiated extensive data theft attacks by exploiting a previously unknown vulnerability on the MOVEit Transfer secure file transfer platform.
These attacks are anticipated to have repercussions for numerous companies across the globe, with many of them having already informed their affected clientele over the course of the last two months. In addition, Clop has altered its approach to extortion by requesting considerably larger ransom payments than those typically observed in data exfiltration attacks. Their aim is to offset the overall decrease in payments by securing a few substantial sums.
Based on insights from various researchers, it’s anticipated that only a limited number of MOVEit data theft victims will opt to make payments. Despite this, Clop is still projected to accumulate a substantial sum, estimated to be in the range of $75-100 million, primarily due to the substantial ransom requests they’ve made.
The ransomware industry remains the number one threat to organizations worldwide. As this quarter had the most recorded victims, supply chain attacks became a solid technique for the mature and experienced ransomware groups.
In addition, this quarter revealed new ambitious groups that are looking to make their mark on the ransomware industry. LockBit3.0 remains the ruler of the industry, although Cl0p was not far behind this quarter.
Although we have seen increased activity by law authorities worldwide this quarter, this industry keeps on thriving despite these efforts.
With Cyberint’s Attack Surface Management, you gain visibility of your true attack surface – the digital assets you are aware of, the assets you are unaware of, and malicious or rogue assets. Learn more about how we prevent ransomware attacks with a 1:1 meeting.

The ransomware industry has been a prominent player this quarter, causing significant impact and affecting numerous organizations globally. With its widespread threat, the industry has successfully claimed 1386 victims.
The industry is feeling increasingly impacted by ransomware as many critical vulnerabilities were discovered this quarter. Additionally, the emergence of new groups, both from the end of 2022 and during this quarter, has contributed to the industry’s growth. These ambitious groups show promise and are introducing a new generation of ransomware families.
While LockBit3.0 continues to dominate as the top ransomware group, their numbers have experienced a slight decline compared to the Q1 2023. Furthermore, one of their affiliates was apprehended.
As with every quarter,the Cyberint Research Team also monitored the emerging new ransomware groups. Notably, MalasLocker, 8base, and Nokoyawa have gained attention as new players in the field. In their first quarter of operations, these groups collectively claimed a total of 305 victims.
This report aims to summarize the global ransomware activity observed in Q2 2023. It will delve into statistics, trends, noteworthy events, and arrests related to ransomware incidents.
Overall, this quarter we saw a massive increase of no less than 67% in ransomware cases compared to last quarter, as ransomware groups were able to compromise 1386 victims worldwide (Figure 1).
Compared to Q2 of 2022, we see that the numbers are even higher with an increase of 97% in ransomware cases (Figure 2).
Undoubtedly, this quarter was by far one of the most successful quarters the ransomware industry has seen.
Not surprisingly, the country most targeted is the US, with 574 victims, followed by the United Kingdom and Canada, with 60 and 56 victims respectively (Figure 3).
As for the top sectors targeted, business services is on top this quarter, with 255 victims, followed by the retail and manufacturing sectors, with 168 and 156 victims respectively.

Among all the ransomware groups, three have risen to the top – LockBit3.0, MalasLocker and the veteran ALPHV (Figure 5).
Unlike previous quarters, when the remaining groups didn’t get close to the top three, in this quarter, many of these groups were still able to boast significant victim counts, such as BianLian, 8Base and Cl0p, of course.
LockBit3.0 is currently one of the most seasoned groups in the ransomware industry. They remained consistent throughout the quarter, averaging 20.66 victims per week and 248 victims overall.
LockBit3.0 mostly uses social engineering techniques in their campaigns, such as phishing and malspam, along with bribing employees to willingly give them access.
In addition, in some cases we witnessed that LockBit3.0 was able to utilize and exploit vulnerabilities to gain initial access.
The group mainly focuses on the business services, retail, and manufacturing (Figure 6) sectors.
In addition, the group targeted the US in 93 campaigns, followed by France and the UK, each with ten victims (Figure 7).
While over time, LockBit3.0 has been the most consistent and professional ransomware group in the industry, this quarter, they faced quite a significant competitor – MalasLocker.
This new rising star of the ransomware industry first emerged on April 9 (Figure 8) and, throughout the quarter, was able to compromise 171 victims, which might be the best debut we have seen in the history of new ransomware groups.
Like many ransomware groups, MalasLocker presents itself as the “good guy” who is doing the victims a favor by testing their defenses. In return, they request payment for their hard labor.
It seems that MalasLocker usually targets Zimbra servers using the CVE-2022-27925, CVE-2022-37042, CVE-2022-30333 and CVE-2022-24682 vulnerabilities.
When it comes to targeted sectors, we can see that the top sectors targeted by MalasLocker are business services, manufacturing and retail (Figure 9).
Unlike most ransomware groups, the top country targeted by MalasLocker is Italy, followed by the US and Russia (Figure 10).
The fact that MalasLocker also targets Russian companies is very surprising, especially since Russia is one of their top three targeted countries. This leads to the assumption that MalasLocker is based outside the Russian region.
ALPHV/BlackCat is a veteran group, a descendant of the Darkside group that was responsible for the Colonial Pipeline incident, later rebranded into BlackBatter, and now ALPHV.
The group’s affiliates use various techniques in their campaigns as they utilize vulnerabilities, phishing campaigns, and the services of other malware-as-a-service groups, such as IcedID to deploy their payload.
Like most ransomware groups, business services is ALPHV’s most targeted sector, along with retail and finance (Figure 11).
There is no doubt that the US is the group’s main focus, as 55% of its cases are in the US (Figure 12).

This quarter, an astonishing number of new ransomware groups – at least 143 – have emerged. Although the vast majority of these groups will soon perish, some will survive and could become a permanent fixture in the ransomware world.
This quarter we decided to focus on two newcomers that have already resulted in a substantial number of victims (given that we already addressed MalasLocker in the previous sector).
8Base is a group we consider a newcomer. Although evidence suggests that the group existed a few months ago, their first victims were only documented in this quarter. Additionally, their “debut” in the ransomware industry was explosive, with 107 new victims.
Although MalasLocker was able to compromise 171 victims, which is way more than any other newcomer, it seems that 8Base is being taken more seriously in the ransomware industry as many compare it to LockBit3.0 and Conti.
8Base mostly targets the business services, retail and manufacturing sectors, focusing most of its efforts on the US, Brazil and the UK.
Nokoyawa ransomware is a relatively new group that emerged recently. Although it was first seen in February 2022, it disappeared shortly after its arrival and resurfaced this quarter. In their first week, they published 26 new victims, although not much activity has been documented since.
Nokoyawa is known for reusing the leaked Babuk ransomware source code as they utilized it in their campaigns. In addition, their infection methods involve vulnerability exploitation and email phishing. 17 out of the 26 of Nokoyawa’s victims and surprisingly, the most targeted sector of the group, are from the educational sector, followed by the government and the transportation sectors.
Although this quarter was packed with notable events and cases to learn from, the main events we found worth mentioning are definitely the still-ongoing MOVEit campaign, the arrest of Ruslan Astamirov, one of LockBit3.0’s affiliates, and the high bounties on other affiliates and Cl0p’s heads.
To date, the MOVEit campaign is still hitting headlines and claims new victims daily.
Their massive campaign is another great example of how a supply chain attack can affect a significant number of companies worldwide.
MOVEit is managed file transfer (MFT) software that encrypts files and uses secure File Transfer Protocols to transfer data within teams, departments and companies. By encrypting files and utilizing secure File Transfer Protocols, MOVEit provides an allegedly reliable solution for transferring data. MOVEit is used in the healthcare, finance, technology, and government industries.
The MOVEit campaign consists of several critical discovered vulnerabilities, which, once successfully exploited, can lead to remote code execution and data leaks.
The new information about the MOVEit vulnerability did not appear to be new to the Cl0p ransomware group, which had it in its sights long before it was made public. Cl0p has reportedly been exploiting this vulnerability since 2021. Indicators also showed that the group attempted to extract data from compromised MOVEit servers in April 2022.
Cl0p has demonstrated a pattern of conducting zero-day exploit campaigns against various targets, such as Accellion File Transfer Appliance (FTA) devices in 2020 and 2021 and GoAnywhere MFT servers in early 2023. This indicates that such campaigns may be an appealing modus operandi for Cl0p and provides insights into the technical profile of some Cl0p gang members. Currently, Cl0p has published 80 victims that were announced as compromised by the MOVEit vulnerability. In addition, they were able to ransom big name companies such as Norton, EY, and Zellis. The Cyberint Research Team covered this campaign in a different research report.
Ruslan Magomedovich Astamirov was arrested in Arizona and charged by the U.S. Justice Department for deploying LockBit ransomware on networks in multiple countries. If convicted, he could face up to 20 years in prison for wire fraud and up to five years for damaging protected computers.
The U.S. government is determined to expose ransomware perpetrators and bring them to justice, emphasizing that online anonymity will not protect them. Astamirov is the third person to be prosecuted in connection with LockBit, following the arrests of Mikhail Vasiliev and the indictment of Mikhail Pavlovich Matveev.
Evidence suggests that Astamirov used specific email addresses and controlled an IP address involved in the attacks.
When asking LockBit3.0 for a response about how this arrest might affect their operation, they said, “He should have practiced better OpSec”. Once again, the group shows no sentiment, focuses purely on the business itself and on other affiliates, and is recruiting more skilled affiliates to take Ruslan’s place.
There is no doubt that the FBI, along with other intelligence and law enforcement organizations worldwide, decided to significantly increase its efforts in hunting down those behind one of the most widespread threats to organizations worldwide.
As part of their war against ransomware, the FBI is offering a bounty of no less than $10 million for anyone who has information about another LockBit3.0 affiliate, Mikhail Pavlovich Matveev (Figure 13), who, in the past, also worked with Darkside and Babuk ransomware families.
Mikhail, aka Wazawaka, was being targeted by bounty hunters even before the $10 million reward, and several head hunters were able to find him several times, but no arrests were ever made.
In addition, the FBI has also offered a reward for the Cl0p ransomware family, although usually, the reward is given for information that will lead to the shutdown of the operation or the arrest of its people. In Cl0p’s case, the additional reward will be granted for any information linking a government or a state to Cl0p and its operations, especially if it’s related to the MOVEit campaign.
We all know that the ransomware threat is not going anywhere. However, Q2 of 2023 showed massive growth in ransomware cases with several new campaigns and the emergence of new, very ambitious groups.
Although LockBit3.0 remains the industry leader, more and more groups have risen to the challenge and tried to take over the throne.
In addition, Cl0p’s MOVEit campaign has taught us once again how lethal a ransomware campaign can be when obtaining strategic pivot points in a supply chain infrastructure. We expect other ransomware groups to invest time and effort in exploiting and finding these strategic links as well.
Unfortunately, Q2 of 2023 was very successful for the ransomware industry, with the highest victim counts per quarter we have seen, ambitious newcomers, and a strong supply chain use case that could be utilized by other ransomware groups.
Cyberint gathers high-tier sources that remain elusive to most companies. We penetrate hidden corners to enables us to collect and analyze data. We enrich our automated collection with a human approach, through research and analysis of our military-grade expert team. Get a demo and see what assets you have exposed on the deep & dark web that could put you at risk of a ransomware attack.
The first quarter of 2023 was the best quarter we’ve seen for the ransomware industry in a long time, even exceeding Q1 2022. With 831 victims, Q1 2023’s victim count was much higher than the first quarter of 2022, with just 763 victims.
Unsurprisingly, LockBit3.0 remained the number one group claiming an average of around 23 victims per week and almost 33% of all ransomware cases this quarter.
The groups that came in second and third places were Clop Ransomware and ALPHV/BlackCat ransomware, with 104 and 81 victims, respectively.
In addition, we saw some notable events, such as LockBit’s Royal Mail incident, the shutdown of Hive Ransomware and the ESXiArgs campaign with thousands of infected machines.
As mentioned, LockBit3.0, ALPHV and Royal are currently leading the industry; LockBit has the most victims (Figure 1).
When it comes to the top 10 ransomware targeted countries, the US remains the number one targeted country with the UK and Canada falling behind (Figure 2).

Analyzing the victims by sectors, we can see that the manufacturing sector is the top targeted sector this quarter, along with the services and construction sectors (Figure 3).
During this quarter, we encountered several interesting ransomware cases.
At the beginning of February, the U.S. Department of Justice celebrated a major victory in the fight against ransomware by dismantling and confiscating the infrastructure of Hive ransomware (Figure 4), which was one of the most persistent groups in the ransomware industry and was ranked in the top 10 ransomware groups in 2022.

Hive ransomware emerged in mid-2021 and has reportedly targeted and held ransom about 1,500 victims.
At a press conference led by FBI Director Christopher Wray, it was revealed that the FBI had taken control of servers in Los Angeles, which contained important Hive ransomware gang data. The operation was the culmination of several months of investigation, beginning with the FBI’s infiltration of Hive ransomware’s network in July 2022. By gaining access to the network, the FBI obtained the decryption keys for the ransomware and provided them to 1,300 current and former Hive targets.
While many celebrated the takedown, some doubt it will have any real effect on the ransomware industry in general. Currently, there has been no actual change and none of the other veteran groups went off-grid because of this incident.
In early January, the UK’s Royal Mail was compromised by a ransomware attack. At first, it seemed that it was a new module of LockBit named Lockbit Black.
However, when contacting the LockBitSupp, they claimed that this was in fact their module, but they are not aware of any campaign targeting the UK’s Royal Mail.
This claim raised many speculations regarding copycats or new groups that emerged due to a leak LockBit had in September 2022.
Several days later, LockBit3.0 made another announcement saying that they had found the affiliate that was responsible for the attack and they reclaimed responsibility for the case, saying, “We have too much activity going on these days and it’s hard to keep track of everything”.
During negotiations for this case, LockBit demanded a £65 million ransom, which was rejected by the Royal Mail.
While observing LockBit’s negotiation chats, the group said that these are hard times for the ransomware industry as they are impacted by less profitable campaigns.
Over the weekend, a relatively new ransomware group named Nevada Ransomware initiated its first massive campaign, targeting any ESXi machine that is exposed to the internet. The group seemed to compromise hundreds of servers over the weekend and caused major damage. Although the scale of this campaign is one of the biggest we have seen, it might already have a solution.
As mentioned, the group includes only Russian and Chinese speakers. As a result, the group’s encryption module does not target Russia, Albania, Hungary, Vietnam, Malaysia, Thailand, Turkey and Iran.
Over the weekend, the group targeted any front facing ESXi machine that could find and exploited multiple related vulnerabilities. A significant proportion of the victim count is focused on France.
The group encrypts the configuration files of the ESXi systems instead of encrypting the vmdk disks themselves.
Then, a ransomware note is left for the victim with contact information for negotiations.
Clop Ransomware is a veteran ransomware group that emerged in February 2019 and targeted most industries worldwide, including retail, manufacturing, energy and finance.
Over the last three weeks of Q1, Clop’s victim count was much higher than the average numbers we are used to seeing from this group. It seems that Clop was able to claim an massive number of victims worldwide and was even able to surpass the current ruler of the ransomware industry, LockBit3.0.
The Cyberint research team has covered this anomaly in this blog post “Is Clop the New Ransomware to Watch?”, which is recommended reading.
During Q1, Cyberint’s research team found 167 new ransomware families. While this number seems very high, not all of them will become major actors in the ransomware industry, and some of them target individuals and not organizations.
Those that the Cyberint research team found more interesting this quarter than the others are Medusa ransomware and Nevada ransomware.
Medusa ransomware has become a solid member in the ransomware industry in 2023, targeting corporate victims worldwide with high ransom demands.
The Medusa operation started in June 2021 but with relatively low activity, and few victims. However, in 2023 this ransomware gang increased its activity and launched its own unique ‘Medusa Blog’ and like the classic double-extortion model, threatened to leak the files if the ransom isn’t paid.
One of the cases that made Medusa ransomware fairly popular in the mainstream was the video they published of themselves showing the stolen data of one of their campaigns, targeting the Minneapolis Publish Schools (MPS).
Throughout this quarter, Medusa was able to compromise 20 victims as their activity started in mid-February.
The Nevada group was first introduced to the cybercrime industry on December 10, 2021, when they published an announcement to recruit new members to their Ransomware-as-a-Service plan.
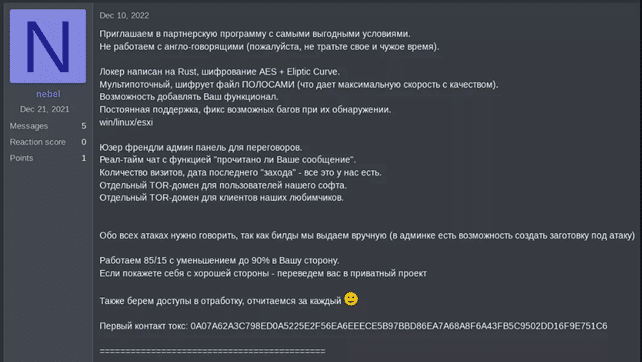
The group works with only Russian and Chinese-speaking individuals.
Their encryption module is built in Rust and is currently still under development, as the group claims it will target Windows and Linux machines in addition to ESXi.
As the group is still very new, there is a chance that this incident was merely an initial experiment for their products and an opportunity to get some free PR, given that any threat actor in the cybercrime industry knows their name.

This campaign claimed around 3,200 victims in the first week. It taught us a lot about the awareness companies have of version control. One of the vulnerabilities that was exploited was a two-year-old vulnerability, where the patch has been available for around the same amount of time.
The ransomware industry is on the rise once again. Clop delivered explosive numbers towards the end of the quarter, Royal became more firmly established and LockBit3.0’s stayed consistent. This led to the ransomware industry claiming a greater number of victims than any quarter in the past year.
When considering the fact that Hive ransomware operators might make a comeback in the next 2-3 months with a rebrand, we do see a shift in favor of the ransomware industry as the once new groups, are now a persistent threat in our landscape.

Fill in your business email to start