


Launched in September 2019 and formerly known as ‘ABCD’, LockBit is a ransomware-as-a-service (RaaS) threat that was updated in June 2021 and improved on the group’s earlier claims of having the fastest encryption process on the ransomware scene (Figure 1).
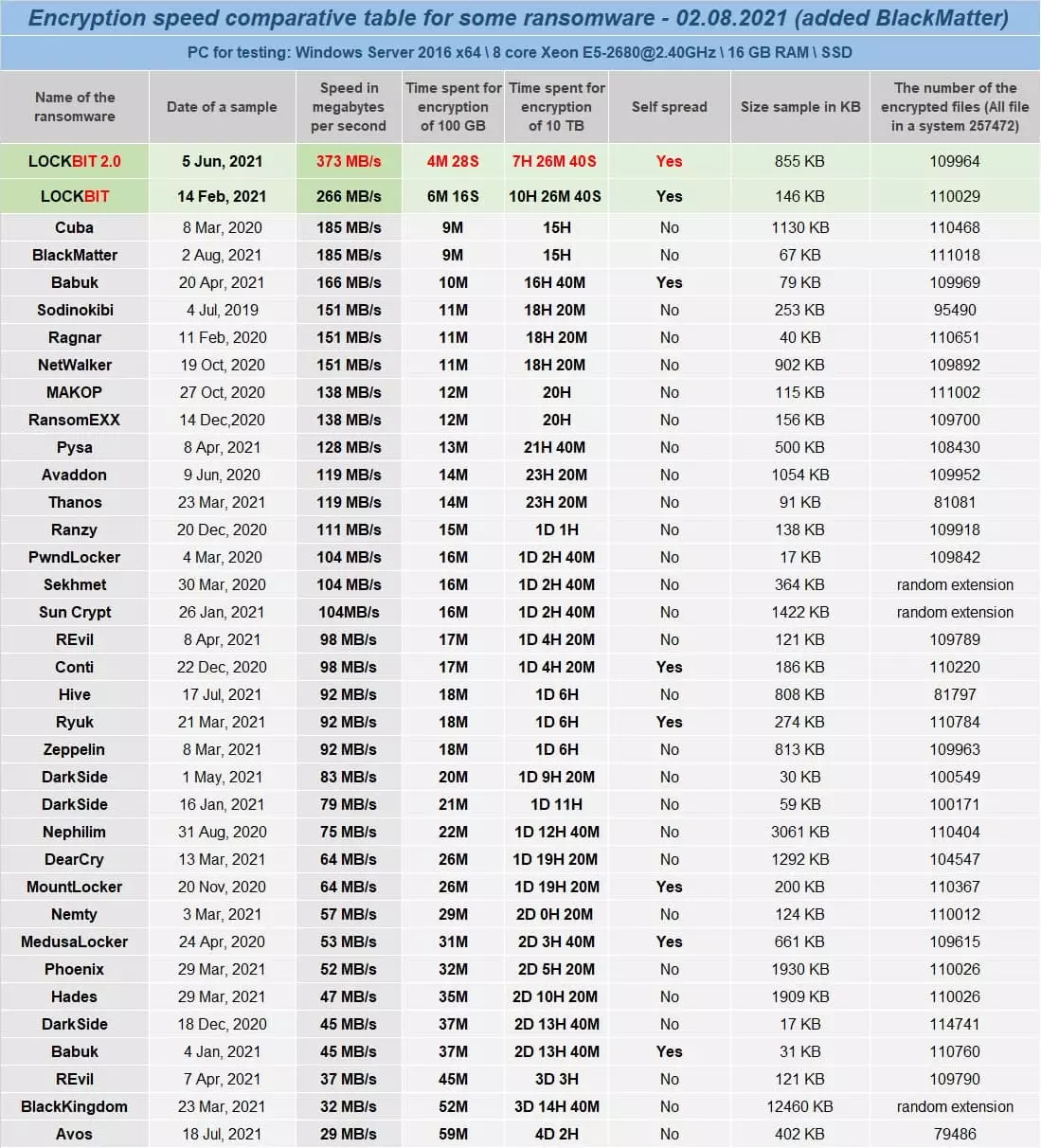 Figure 1 – LockBit encryption speed comparison
Figure 1 – LockBit encryption speed comparisonMuch like other RaaS offerings, LockBit operates an affiliate profit sharing program in which up-to eighty percent of a ransom payment can be earned whilst the operators claim the remainder.
Reportedly only requiring the affiliate to gain access to a ‘core’ server, such as a Windows Domain Controller (DC), the advertised feature set (Figure 2) suggests that the LockBit ransomware will distribute itself across the network in addition to automating steps that aid in detection evasion, complicating post-incident analysis and preventing data restoration.
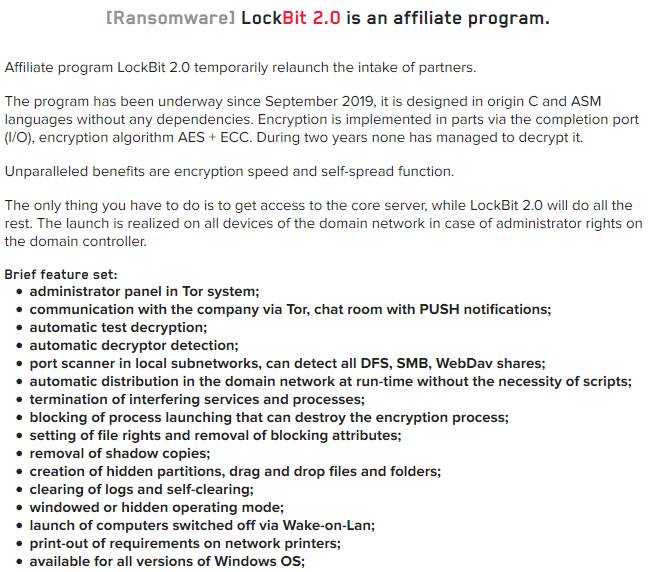 Figure 2 – LockBit 2.0 features
Figure 2 – LockBit 2.0 featuresAs is common with many ‘big game hunter’ ransomware threats, LockBit and their affiliates utilize the double extortion tactic, stealing data and threatening its release to encourage ransom payments.
As seen in the recent high-profile incident involving Accenture, a multinational consulting and professional services firm, LockBit share details of their victims on a Tor-hosted leak site (Figure 3) along with a timer the counts down to the date and time at which stolen data will be published unless the ransom payment is received.
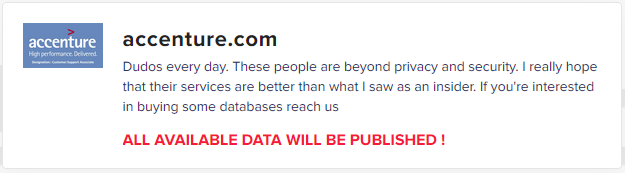 Figure 3 – LockBit ‘Accenture’ leak
Figure 3 – LockBit ‘Accenture’ leakIn Accenture’s case, LockBit have reportedly demanded a fifty million US Dollar ($50M) ransom with the countdown for payment of expiring at 20:43:00 UTC on August 13, 2021.
Potentially indicating the scale of data theft from Accenture and no doubt taking into account the firm’s profitability, this ransom demand is considerably higher than LockBit’s previously reported average ransom of $85,000.
Notably, whilst Accenture are currently in the headlines, details of some thirty-eight additional victims are currently listed on LockBit’s leak site with deadlines expiring anywhere between hours and thirteen days (as at the time of writing). Aside from demonstrating that LockBit and their affiliates are highly capable, there is no apparent pattern of victim geography or sector.
Whilst it is well known that most ransomware groups won’t target organizations located within the Commonwealth of Independent States (CIS), it comes as no surprise that current LockBit victims are located across Asia, North America, South America and Western Europe. Additionally, there appears to be no consistency in the targeted industry or sector with current victims including financials, manufacturing, petrochemicals and retail.
Whilst each affiliate will likely have their own preferred tactics, techniques and procedures (TTP) to distribute LockBit, most big game hunter ransomware groups operate in a similar manner when it comes to the initial intrusion vector.
Although targeted phishing campaigns may remain a useful method of gaining access to user credentials and/or delivering a payload to an endpoint, many ransomware threat actors continue to target exposed Windows Remote Desktop instances with brute-force attacks as well as exploiting known vulnerabilities in exposed network devices such as VPN gateways.
Specifically, the Australian Cyber Security Centre (ACSC) have recently observed LockBit as exploiting a three-year-old vulnerability in Fortinet FortiOS and FortiProxy products, CVE-2018-13379, that allows an unauthenticated threat actor to download system files via specially crafted HTTP requests and, presumably in these incidents, gain access to credentials and subsequently the target network.
Concerningly, as highlighted in commentary following the recent Accenture incident, recent reports suggest that LockBit have sought to recruit employees of target networks which, depending on the insider threat’s access, could save the ransomware group a considerable amount of time and effort.
Whilst it is hoped that most employees would ignore and/or report any nefarious recruitment attempt, cash rich ransomware groups will be more than able to offer lucrative incentives that some may find hard to resist, especially if they already hold some grievance against their employer.
Although the initial infection vector may differ from one victim to another, the objective upon gaining access to the victim network remains consistent: the exfiltration of sensitive and valuable data, prior to encryption, to exert maximum pressure on the victim and encourage prompt payment of any ransom demand.
As recently observed during the Cyberint Research investigation into the Conti Ransomware ‘manuals and tools’ leak, many groups utilize Rclone, a legitimate opensource tool used to synchronize and manage data on local, cloud and virtual file systems.
Seeking to again optimize their operation, LockBit have developed their own data stealing method dubbed ‘StealBit’ that, according to their claims (Figure 4), is significantly faster than exfiltrating data to common cloud services using Rclone.
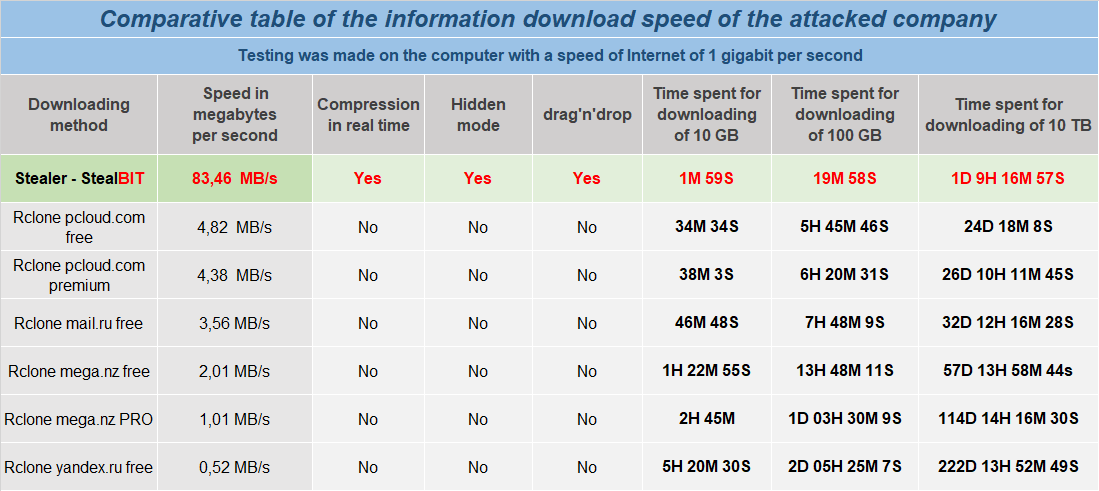 Figure 4 – StealBit performance comparison
Figure 4 – StealBit performance comparisonTo prevent interference with the encryption process, it is typical for ransomware threats to terminate processes or services, such as applications or backup utilities that may ‘lock’ files open, as well as endpoint security solutions that may detect the threat.
Whilst many threats utilise Windows command line utilities, such as net.exe stop <PROCESS> or taskkill.exe /IM <PROCESS> /F, LockBit directly calls functions within the Windows API to achieve the same outcome, likely attempting to further evade detection where endpoint monitoring is in place.
Subsequently, point-in-time backup copies of data created using the Windows Volume Shadow Copy Service (VSS) are deleted in advance of the encryption process using a single line command that also includes steps to hamper recovery efforts:
"%WINDIR%System32cmd.exe" /c vssadmin delete shadows /all /quiet & wmic shadowcopy delete & bcdedit /set {default} bootstatuspolicy ignoreallfailures & bcdedit /set {default} recoveryenabled noAside from utilizing the VSS administrative tool, vssadmin.exe, and the Windows Management Instrumentation utility, wmic.exe, to delete existing volume shadow copies, the Boot Configuration Data (BCD) editor, bcdedit.exe, is used to ensure that subsequent system boot failures are ignored and the recovery boot option disabled.
When deployed within an Active Directory (AD) environment and on a Windows Domain Controller (DC), LockBit version 2.0 makes use of Group Policy Objects (GPO) to both disable Windows Defender and distribute, then execute, the ransomware across the network.
Utilizing similar tactics to those ransomware threats that use PowerShell to interact with Windows Defender, a GPO is created to disable real-time monitoring, prevent the upload of samples to Microsoft and supress notifications.
Additionally, a User Account Control (UAC) bypass technique is utilized in the ransomware distribution and execution GPO leading to silent execution on any affected Windows host.
Once complete, a PowerShell command is used to force the update of GPOs, causing them to be pushed to all machines in the domain:
powershell.exe -Command "Get-ADComputer -filter * -Searchbase '%s' | foreach{ Invoke-GPUpdate -computer $_.name -force -RandomDelayInMinutes 0}"Having prepared for the encryption process, LockBit version 2.0 utilizes an AES encryption algorithm that is performed on files ‘in-place’ to prevent recovery from disk and, upon completion, the file extension .lockbit is appended.
In an attempt to prevent post-incident analysis, LockBit version 2.0 attempts to delete itself upon completion using the following command:
"%WINDIR%System32cmd.exe" /C ping 127.0.0.7 -n 3 > Nul & fsutil file setZeroData offset=0 length=524288 "%TEMP%<LOCKBIT_BINARY>.exe" & Del /f /q "%TEMP%<LOCKBIT_BINARY>.exe"Seemingly using the ping command as a delay mechanism, presumably allowing the ransomware process to terminate, the File System utility is used to prevent the malicious executable from being recovered by overwriting the first 524KB with zeros, fsutil file setZeroData offset=0 length=524288, and then forcibly deleting the file, Del /f.
To ensure that the victim is informed of the encryption, LokiBot version 2.0 utilizes three methods to display the ransom note. The first of which, and typical for threats of this nature, is the creation of a text file ransom note named Restore-My-Files.txt (Figure 5) within folders that contain encrypted data.
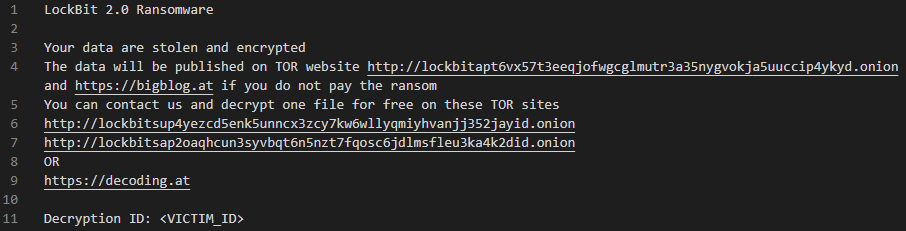 Figure 5 – Text ransom note
Figure 5 – Text ransom noteFor the benefit of victims sat in front of an encrypted machine, a HTML application (HTA) file is saved as %HOMEPATH%DesktopLockBit_Ransomware.hta and launched upon the conclusion of the process to display a full screen notification (Figure 6).
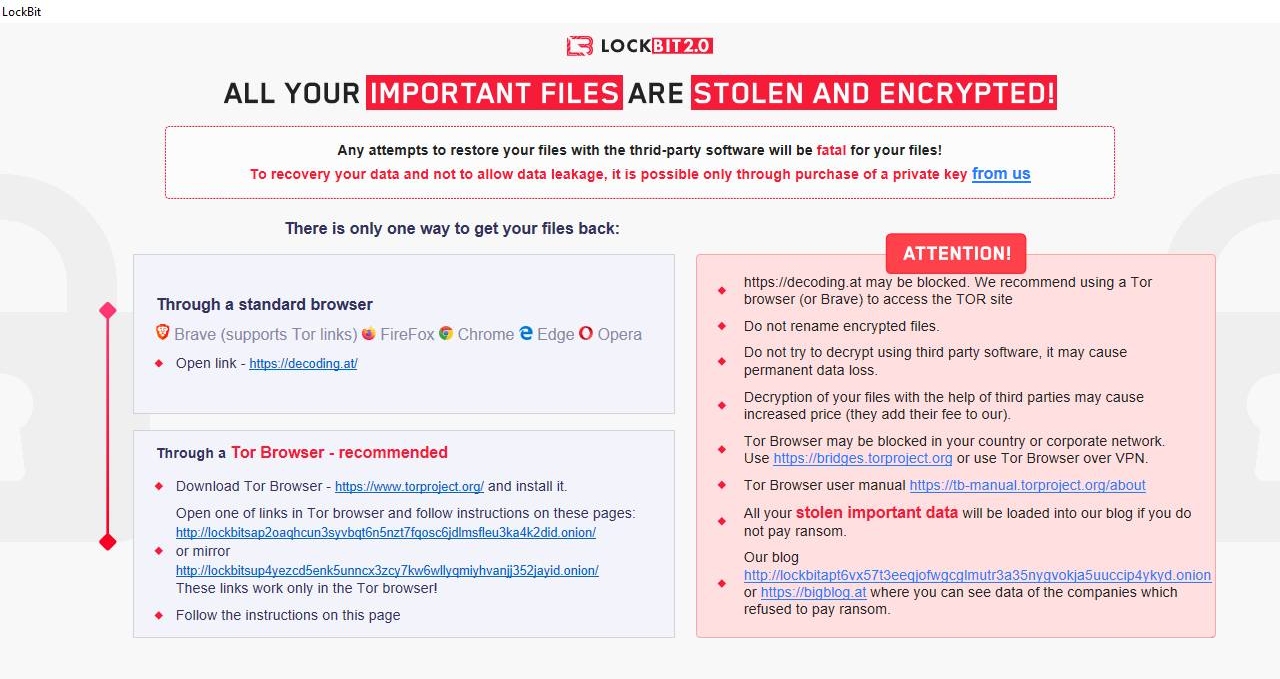
Finally, the Desktop wallpaper is changed and displays a similar message to the HTA ransom note, albeit without the ability for the victim to click on the URLs.
In 2024 a large number of LockBit operatives were arrested and LockBitSupp’s identity was revealed.
net.exe, taskkill.exe, vssadmin.exe and wmic.exe.In addition to the following indicators of compromise (IOC), consideration should be given to reading the Cyberint Research Conti IOC report given the overlap in tactics, techniques and procedures (TTP) used by big game hunter ransomware groups.
The unexpected execution of the following commands, as observed during the execution of LockBit version 2.0, may be indicative of nefarious activity.
bcdedit /set {default} bootstatuspolicy ignoreallfailuresbcdedit /set {default} recoveryenabled no%WINDIR%SysWOW64mshta.exe %HOMEPATH%DesktopLockBit_Ransomware.hta"%WINDIR%System32cmd.exe" /C ping 127.0.0.7 -n 3 > Nul & fsutil file setZeroData offset=0 length=524288 "%TEMP%<LOCKBIT_BINARY>.exe" & Del /f /q "%TEMP%<LOCKBIT_BINARY>.exe"vssadmin delete shadows /all /quietwmic shadowcopy deleteWhilst the LockBit version 2.0 ransomware binary will change from victim to victim, the following samples have been recently observed and are beneficial to those that wish to understand more about the threat.
0545f842ca2eb77bcac0fd17d6d0a8c607d7dbc8669709f3096e5c1828e1c0490d6524b9a1d709ecd9f19f75fa78d94096e039b3d4592d13e8dbddf99867182dbcbb1e388759eea5c1fbb4f35c29b6f66f3f4ca4c715bab35c8fc56dcf3fa621d089d57b8b2b32ee9816338e96680127babc5d08a03150740a8459c29ab3ba78f32e9fb8b1ea73f0a71f3edaebb7f2b242e72d2a4826d6b2744ad3d830671202Notably, the LockBit_Ransomware.hta file is consistent across recently observed LockBit version 2.0 samples:
90f3a33919fdd766e90fd96f8f20a92c2d1376b7cfdc8b738c2f8e7e6c7498b1Although the Restore-My-Files.txt ransom note will vary from victim to victim due to the inclusion of a unique identifier.
The Windows Desktop wallpaper is set to a temporary bitmap file by updating the HKCUControl PanelDesktopWallpaper Registry key and providing a filename within the %TEMP% directory.
The following URLs are provided within the ransom notes as a method to contact the threat actors and/or observe previously leaked data.
hxxp://lockbitapt6vx57t3eeqjofwgcglmutr3a35nygvokja5uuccip4ykyd[.]onionhxxp://lockbitsap2oaqhcun3syvbqt6n5nzt7fqosc6jdlmsfleu3ka4k2did[.]onionhxxp://lockbitsup4yezcd5enk5unncx3zcy7kw6wllyqmiyhvanjj352jayid[.]onionhxxps://bigblog[.]athxxps://decoding[.]atAdditionally, the following URLs have previously been used by the threat group:
hxxp://lockbit-decryptor[.]tophxxp://lockbitks2tvnmwk[.]onion
Fill in your business email to start


