


According to CISA, since the latter part of 2021, the perpetrators behind Snatch Ransomware have persistently adapted their strategies, capitalizing on prevailing tendencies and the operational successes of other ransomware variants within the cybercrime arena.
Snatch has cast a wide net, targeting numerous sectors critical to infrastructure, including but not limited to the Defense, Industry, Food and Agriculture, and Information Technology sectors.
The modus operandi of Snatch encompasses ransomware operations that involve the exfiltration of data and double extortion tactics. Following data exfiltration, which often includes direct ransom demands communicated to the victims, the Snatch threat actors may employ a double extortion strategy. If the ransom remains unpaid, the victim’s data is threatened to be published on Snatch’s extortion blog.
Snatch’s targets include Information and Manufacturing industries, in line with a standard ransomware operator, but one of the notable industries seems to be Healthcare. Although their most significant leaks are government-related, they also frequently target other sectors to meet their financial targets.
Analyzing the geographical distribution of the organizations impacted by Snatch, one can deduce that their primary operations are concentrated in North America and Europe, with the United States being notably the most heavily impacted country.
The last victims of Snatch operators, were US-based retail company Jerry Pate, SA National Defence Force, Italian based Cogal, US-based Ancillae-Assumpta Academy, Intech and Detroit Symphony Orchestra.
Snatch threat actors and their affiliates proactively participate in data exfiltration, utilizing a dual extortion strategy that involves leaking victims’ data if the ransom demands are unmet. Interestingly, these actors have been identified as obtaining previously compromised data from other ransomware variants, intending to coerce victims into paying a ransom to avoid disclosing their data on Snatch’s extortion blog.
It also features data related to victims from other ransomware groups, namely Nokoyawa and Conti, further complicating the cyber threat landscape. In other words, if they have the data of companies whose ransom payment has not been received, they do not let go of it for a long time.
Snatch group may not solely manage these attacks themselves, but even if they do not have “ransomware” of their own, there are certain patterns in the attack scheme used by the Snatch team or its affiliates.
According to CISA’s advisory, the threat actors behind Snatch have been known to exploit weaknesses in Remote Desktop Protocol (RDP) as a primary method of gaining unauthorized access to victims’ networks. This is often achieved through brute-forcing, where they leverage administrator credentials, sometimes even seeking compromised credentials from criminal forums and marketplaces.
Once inside, the Snatch threat actors ensure persistence on a victim’s network by compromising an administrator account and establishing connections over port 443 to a Command and Control (C2) server, typically located on a Russian bulletproof hosting service. Although blocking such hosting, which you can find the necessary IoCs in the CISA advisory, can directly cut off the connection with CC, in many cases, they can avoid this because intermediary servers and proxies are used.
This meticulous approach to maintaining a foothold within the network underscores the group’s strategic planning and execution. The threat actors have been observed using various tactics to discover data, move laterally, and search for data to exfiltrate. Notably, they utilize “sc[.]exe” to manipulate system services using the Windows Command line and also employ tools like Metasploit and Cobalt Strike for their operations.
In a particular incident, Snatch threat actors have been observed spending up to three months on a victim’s system before deploying the ransomware. During this time, they exploit the victim’s network, moving laterally across it with RDP and searching for files and folders for data exfiltration, followed by file encryption. This extended presence on the network before making a move indicates a calculated approach, ensuring they maximize the impact of their eventual attack.
In the early stages of ransomware deployment, Snatch threat actors attempt to disable antivirus software and run an executable, often named “safe[.]exe” or a variation thereof. In some instances, the ransomware executable’s name consisted of a string of hexadecimal characters, which match the SHA-256 hash of the file, a tactic employed to defeat rule-based detection.
The Snatch ransomware payload then queries and modifies registry keys, uses various native Windows tools to enumerate the system, finds processes, and creates benign processes to execute Windows batch (.bat) files. Sometimes, the program attempts to remove all the volume shadow copies from a system.
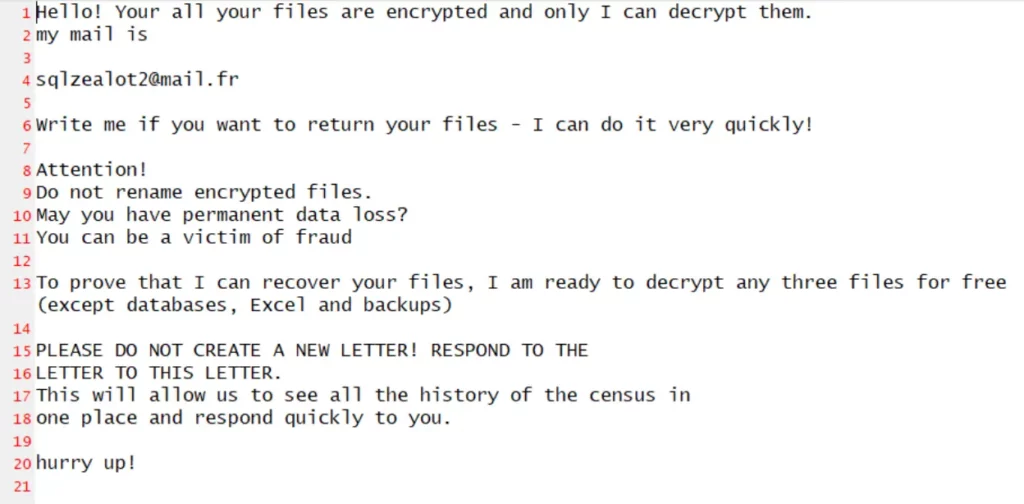
Upon successful encryption, the Snatch ransomware executable appends a series of hexadecimal characters to each file and folder name it encrypts, leaving behind a text file titled “HOW TO RESTORE YOUR FILES.TXT” in each folder. Communication with victims may be established through e-mail and the Tox communication platform, based on identifiers left in ransom notes or through their extortion blog by getting a UUID (Universal Unique Identifier).
Snatch victims may have had a different ransomware variant deployed on their systems but received a ransom note from Snatch threat actors, resulting in the victims’ data being posted on the ransomware blog.
It is widely suspected that Snatch are a Russian/Eastern Europe Group.
Snatch Ransomware emerged on the cyber threat landscape in 2019 and has since established itself as a formidable player in the ransomware arena. Initially known as Team Truniger, derived from the alias of a pivotal member, Truniger, who had formerly been an affiliate of GandCrab. Originating with a distinct modus operandi, the group has been linked to high-profile cyber-attacks, with many operations traced back to Russian origins.
The report from the FBI/CISA indicates that Truniger had past affiliations as an operative with GandCrab, a precursor in the Ransomware-as-a-Service domain, which ceased operations after extracting over $2 billion from its victims. GandCrab disbanded in July 2019 and is speculated to have evolved into “REvil,” recognized as one of the most merciless and predatory Russian ransomware groups in history.
Their name, seemingly a reference to the movie Snatch, is also written as S.N.Atch (Security Notification Attachment) in the logo of their official Telegram channel. However, contrary to security researchers’ assertions, the operators of Snatch Ransomware present a different claim about their origins and operations.
The threat actors have asserted on leak sites that the allegations from CISA and the security community are unfounded, stating they have no connections to prior Snatch operations and do not adhere to a conventional ransomware model. The group emphasizes its concentration on data leaks and clarifies that the malware utilized in its operations is indirectly sourced from various affiliates and threat actors with whom they collaborate. Additionally, they specify that there is no malware referred to as “Snatch” in their operations.
However, it is not easy to accept their defense as valid. Utilizing domains once used by the Snatch ransomware group has not justified their domain name choices and claims ignorance of the ransomware group’s existence at their inception two years ago. Their website serves as a data marketplace, advocating free access to information and welcoming any team to contribute data for publication. While they deny owning ransomware, they are open to data placement and monetization collaborations.
To learn more about how our threat intelligence research helps protect businesses against ransomware and other risks, request a demo.
| Tactic | Technique |
|---|---|
| Initial Access | Collection T1114.001 – Local Email Collection |
| Exfiltration | Scheduled Transfer T1029 – Scheduled Transfer |
| Execution | Service Execution T1569.002 – Service Execution |
| Initial Access | Supply Chain Compromise T1195 – Supply Chain Compromise |
| Execution | Windows Command Shell T1059.003 – Windows Command Shell |
| Discovery | Internet Connection Discovery T1016.001 – Internet Connection Discovery |
| Exfiltration | Transfer Data to Cloud Account T1537 – Transfer Data to Cloud Account |
| Privilege Escalation | Shortcut Modification T1547.009 – Shortcut Modification |
| Persistence | Shortcut Modification T1547.009 – Shortcut Modification |
| Privilege Escalation | Registry Run Keys / Startup Folder T1547.001 – Registry Run Keys / Startup Folder |
| Persistence | Registry Run Keys / Startup Folder T1547.001 – Registry Run Keys / Startup Folder |
| Defense Evasion | Match Legitimate Name or Location T1036.005 – Match Legitimate Name or Location |
| Defense Evasion | Binary Padding T1027.001 – Binary Padding |
| Impact | Data Encrypted for Impact T1486 – Data Encrypted for Impact |
| Persistence | Valid Accounts T1078 – Valid Accounts |
| Initial Access | Valid Accounts T1078 – Valid Accounts |
| Privilege Escalation | Valid Accounts T1078 – Valid Accounts |
| Defense Evasion | Valid Accounts T1078 – Valid Accounts |
| Execution | PowerShell T1059.001 – PowerShell |
| Initial Access | Spearphishing Attachment T1566.001 – Spearphishing Attachment |
| Exfiltration | Exfiltration Over C2 Channel T1041 – Exfiltration Over C2 Channel |
| Initial Access | Spearphishing Link T1566.002 – Spearphishing Link |
| Exfiltration | Exfiltration Over Web Service T1567 – Exfiltration Over Web Service |
| Exfiltration | Automated Exfiltration T1020 – Automated Exfiltration |
| Initial Access | Exploit Public-Facing Application T1190 – Exploit Public-Facing Application |

Fill in your business email to start.
©1994–2026 Check Point Software Technologies Ltd. All rights reserved.
Copyright | Privacy Policy | Cookie Settings | Get the Latest News
Fill in your business email to start


