


Original Article published Decmber 2023.
Update May 22nd 2025: The FBI has seized user panels and other Lumma C2 infrastructure.
As of now, we don’t see the Lumma info-stealer disappearing from the arena. Our team is on guard to check and analyze the changes.
This case shares similarities with the so called seizure of infrastructure of RedLine and Metta info stealers in October 2024 by the FBI, DOJ, Dutch authorities, etc.
Many experts believe that the disruption isn’t significant enough at the moment and currently we concur as in the past 24 hrs we have been able to collect a significant number of new Lumma logs.
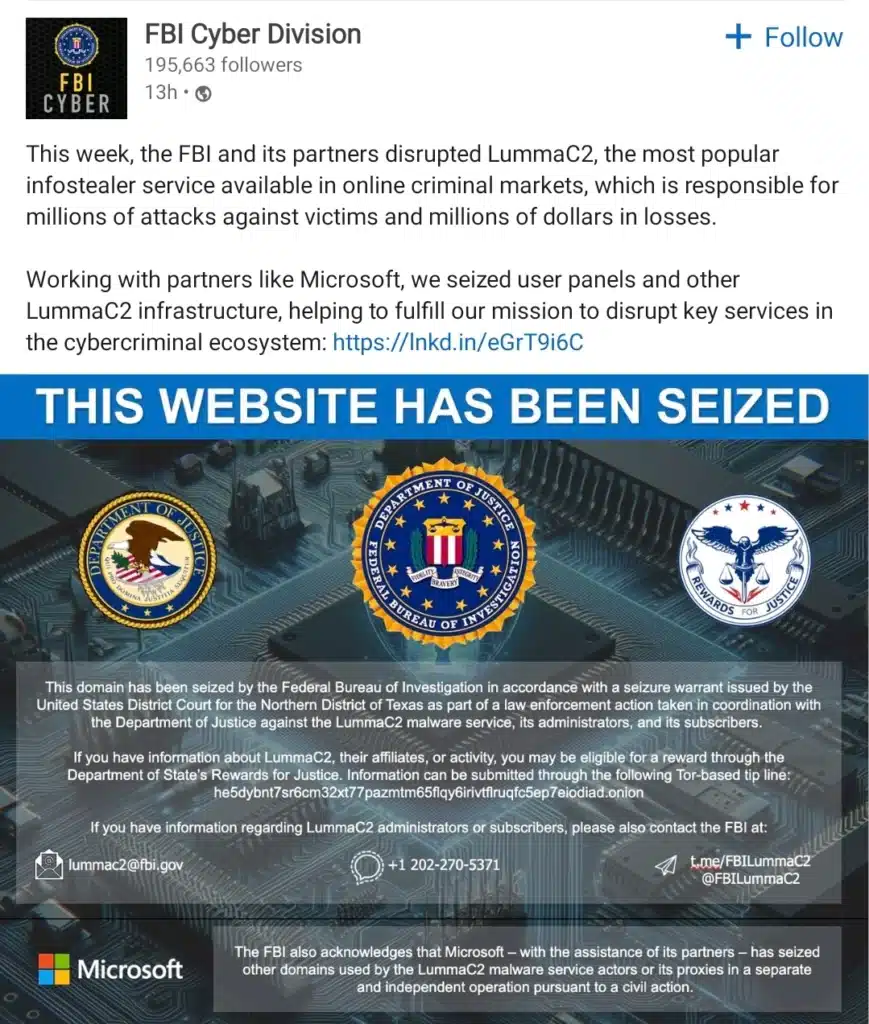
InfoStealer malware has become increasingly widespread, new business models are being introduced and new detection evasion capabilities are being implemented. Lumma Stealer was initially identified in August 2022 and is currently trending.
Lumma Stealer is specifically crafted to illicitly obtain sensitive data from compromised devices. This encompasses an array of information such as private browser data, browser extensions, configuration details for crypto wallet software, wallet contents, and even employing a grabber function to seize entire files based on specified patterns.
The malware is available for purchase through dark web forums, and the official lumma shop, which evidence shows is facilitated by the threat actor “Shamel”. Its pricing structure includes a standard version at $140 per month and an extended version at $160 per month.
Regarded as a potent menace for crypto users, Lumma Stealer targets web browsers, cryptocurrency wallets, 2FA extensions, and instant messaging services like Telegram to extract valuable data. The malware also boasts the capacity to introduce supplementary malware and execute additional commands using its Loader module.
Traced back to its initial identification in August 2022, Lumma Stealer has undergone subsequent updates and improvements. Engineered to elude detection, it poses a challenge when attempting to uncover and eradicate its presence from a compromised system.
Lumma Stealer can spread through various methods:
Lumma Stealer can have a significant negative impact on the security and privacy of affected systems. Based on available information, its potential consequences are as follows:
To learn more about how our threat intelligence research helps protect businesses against ransomware and other risks, request a demo.
| tacticName | technique |
|---|---|
| Defense Evasion | T1444 – Masquerade as Legitimate Application |
| Initial Access | T1444 – Masquerade as Legitimate Application |
| Defense Evasion | T1036 – Masquerading |
| Collection | T1115 – Clipboard Data |
| Collection | T1113 – Screen Capture |
| Collection | T1513 – Screen Capture |
| Collection | T0852 – Screen Capture |
| Reconnaissance | T1590 – Gather Victim Network Information |
| Credential Access | T1417 – Input Capture |
| Collection | T1417 – Input Capture |
| Initial Access | T1199 – Trusted Relationship |
| Initial Access | T1189 – Drive-by Compromise |
| Initial Access | T1195 – Supply Chain Compromise |
| Initial Access | T1456 – Drive-By Compromise |
| Reconnaissance | T1592 – Gather Victim Host Information |
| Initial Access | T1190 – Exploit Public-Facing Application |
| Persistence | T0859 – Valid Accounts |
| Lateral Movement | T0859 – Valid Accounts |
| Initial Access | T0817 – Drive-by Compromise |
| Initial Access | T0862 – Supply Chain Compromise |
| Reconnaissance | T1591 – Gather Victim Org Information |
| Initial Access | T1566 – Phishing |
| Initial Access | T0819 – Exploit Public-Facing Application |
| Initial Access | T1474 – Supply Chain Compromise |
| Credential Access | T1056 – Input Capture |
| Collection | T1056 – Input Capture |
| Defense Evasion | T1078 – Valid Accounts |
| Persistence | T1078 – Valid Accounts |
| Privilege Escalation | T1078 – Valid Accounts |
| Initial Access | T1078 – Valid Accounts |
| Credential Access | T1414 – Clipboard Data |
| Collection | T1414 – Clipboard Data |

| Type | Value | Last Observation Date |
|---|---|---|
| SHA-256 | 15e2377abd28c57a3360fbc22904a3ff6d7dc26fe9b0294db7a986535c81d324 | 2025-05-22 |
| SHA-256 | a16a0db9482b59ae04fcac88b8181162f7433e67280450e78aecff01b217a02f | 2025-05-22 |
| SHA-256 | 314f6084e02ebad9e34820a34a6e6becd2f5e01adc6de008573fb6bdaf6df087 | 2025-05-22 |
| SHA-256 | e975b7fb541da40f73616e3839773e2ceb464bed554128c68e1f617253b5d3c0 | 2025-05-22 |
| SHA-256 | 163d9e5ba3c93d6b5041ba234571f393ed688a4005bb3570a42196080ff1594c | 2025-05-22 |
| SHA-256 | 5319fbed87f7a523a485e05e702d1148fc1653a2d6ec0e35cd20a5d27e859e27 | 2025-05-22 |
| SHA-256 | a5c9d15e72cc65a01084e88e8d6a99a5459e5d060d8417f060e8badff184d8cd | 2025-05-22 |
| SHA-256 | bdfb1adb14883e192822dd055819e5841f92252ada0a9b6efb5318f4c1ab8b6f | 2025-05-22 |
| SHA-256 | 5612a695dc215ee1311d8dd47a703fc40e37dffbe810a0d2ec6e3ce7a9fae530 | 2025-05-22 |
| SHA-256 | e35e7b278fe49d946e59e3dc256d49d4444fd20824eeee30531e0e174b6b7c75 | 2025-05-22 |
| SHA-256 | b7c59aafd519e5290c3180bca5f244f12c84076be98ab5734b9b216daf4c0bf6 | 2025-05-22 |
| SHA-256 | 377377287369ce799e19f1b88a02475be707066e0fa2f34873dac181b606504d | 2025-05-22 |
| SHA-256 | 0d3cd229ab20efc2e57326ef720ea92b0a8abc1915b65db97b186c2556a3dbeb | 2025-05-22 |
| URL | https://bnarrathfpt.top/tekq | 2025-05-22 |
| Domain | trotwhvn.live | 2025-05-22 |
| Domain | shoresolfe.live | 2025-05-22 |
| Domain | moondips.bet | 2025-05-22 |
| Domain | genusbwaiw.live | 2025-05-22 |
| URL | https://1techsyncq.run/riid | 2025-05-22 |
| URL | https://ibuzzarddf.live/ktnt | 2025-05-22 |
| URL | https://vbearjk.live/benj | 2025-05-22 |
| Domain | strejqt.bet | 2025-05-22 |
| Domain | ordntx.top | 2025-05-22 |
| Domain | scricn.digital | 2025-05-22 |
| Domain | cirxr.digital | 2025-05-22 |
| Domain | miskfg.digital | 2025-05-22 |
| Domain | indict.digital | 2025-05-22 |
| Domain | firzql.digital | 2025-05-22 |
| Domain | hasta.digital | 2025-05-22 |
| Domain | untikr.digital | 2025-05-22 |
| Domain | gejezu.digital | 2025-05-22 |
| Domain | caniir.digital | 2025-05-22 |
| Domain | rechq.digital | 2025-05-22 |
| Domain | sharpy.digital | 2025-05-22 |
| Domain | bushzy.digital | 2025-05-22 |
| Domain | ectacz.digital | 2025-05-22 |
| Domain | twinwx.digital | 2025-05-22 |
| Domain | dusrb.digital | 2025-05-22 |
| Domain | incxwf.shop | 2025-05-22 |
| URL | https://cescczlv.top/bufi | 2025-05-22 |
| URL | https://dordntx.top/pxla | 2025-05-22 |
| URL | https://kqstrejqt.bet/mbnj | 2025-05-22 |
| URL | https://releaswrlf.run/jadz | 2025-05-22 |
| URL | https://0citellcagt.top/gjtu | 2025-05-22 |
| URL | https://ankyufh.live/qfei | 2025-05-22 |
| URL | https://gcitellcagt.top/gjtu | 2025-05-22 |
| URL | https://judiivk.live/tuhd | 2025-05-22 |
| URL | https://strejqt.bet/mbnj | 2025-05-22 |
| URL | https://x3hmaxmtsq.bet/xzid | 2025-05-22 |
| URL | https://o-narrathfpt.top/tekq | 2025-05-22 |
| URL | https://uonehunqpom.life/zpxd | 2025-05-22 |
| Domain | localixbiw.top | 2025-05-22 |
| Domain | diecam.top | 2025-05-22 |
| Domain | korxddl.top | 2025-05-22 |
| Domain | bogtkr.top | 2025-05-22 |
| URL | https://korxddl.top/qidz | 2025-05-22 |
| URL | https://localixbiw.top/zlpa | 2025-05-22 |
| SHA-256 | 6c0816cd05cc9c52d1356c90e09110159968f39078bd4ebe90842637bd9d544b | 2025-05-21 |
| SHA-256 | 8fdfa05d17b5cfce71c32e31f94e51975830c9a6b1fd117a258e2efdacaf0c42 | 2025-05-21 |
| SHA-256 | d6a6c0585d9d15744b2f3ff454e47ef583f4223fb248c1d3983b883684b54de0 | 2025-05-21 |
| SHA-256 | 54e338e97ca7ff1954dad0e7810a8fea3d6e6085ae8895b3d4be12ff57826516 | 2025-05-21 |
| SHA-256 | eccd12339b9e5840bc2e5fbde527e540c13286f1655c488d0b4057c35a11e837 | 2025-05-21 |
| SHA-256 | 961c16498ba05d25ee87e4a2b4388603b926833f97f16031a90b7903849425c7 | 2025-05-21 |
| SHA-256 | a22bcc1320cb3cdd7165515d13d810a60a4acf850482af33c02a2f74d417205b | 2025-05-21 |
| SHA-256 | 9d3c7c61f62db3e7d5a779a226891559ab970ec6d2ca3c79182aee5bdbecba2e | 2025-05-21 |
| URL | https://lclarmodq.top/qoxo | 2025-05-21 |
| URL | https://jparakehjet.run/kewk | 2025-05-21 |
| URL | https://kfishgh.digital/tequ | 2025-05-21 |
| Domain | worldpofadventure.today | 2025-05-22 |
| Domain | strengbllk.live | 2025-05-21 |
| Domain | retechlabp.run | 2025-05-21 |
| Domain | ofttimkong.run | 2025-05-21 |
| Domain | jugulagklc.live | 2025-05-21 |
| Domain | anesthwtcm.run | 2025-05-22 |
| URL | https://scaitraohvi.bet/adks | 2025-05-21 |
| URL | https://yescczlv.top/bufi | 2025-05-21 |
| URL | https://9gettoknwg.life/xapd | 2025-05-21 |
| URL | https://bubblezdjw.live/kudf | 2025-05-21 |
| URL | https://enarrathfpt.top/tekq | 2025-05-21 |
| URL | https://nwinterghzp.digital/ywq | 2025-05-21 |
| URL | https://quaterujrb.shop/fasj | 2025-05-21 |
| URL | https://w2bhaircuirfm.top/aldk | 2025-05-21 |
| URL | https://catsuiqdmn.live/euwq | 2025-05-21 |
| URL | https://rparakehjet.run/kewk | 2025-05-21 |
| URL | https://ubtcgeared.live/lbak | 2025-05-21 |
| URL | https://definitnve.run/ioqn | 2025-05-21 |
| URL | https://2posseswsnc.top/akds | 2025-05-21 |
| URL | https://escapadue.live/SPzkwq | 2025-05-21 |
| URL | https://hdjackthyfuc.run/xpas | 2025-05-21 |
| URL | https://ktlaminaflbx.shop/twoq | 2025-05-21 |
| URL | https://ibtcgeared.live/lbak | 2025-05-21 |
| URL | https://hemphatakpn.bet/ladk | 2025-05-21 |
| URL | https://2flowerexju.bet/lanz | 2025-05-21 |
| URL | https://1uaraucahkbm.live/baneb | 2025-05-21 |
| URL | https://0araucahkbm.live/baneb | 2025-05-21 |
| URL | https://jfeaturlyin.top/pdal | 2025-05-21 |
| URL | https://ftracxilb.digital/ozi | 2025-05-21 |
| URL | https://racxilb.digital/ozi | 2025-05-21 |
| URL | https://fkposseswsnc.top/akds | 2025-05-21 |
| URL | https://kmeteorplyp.live/lekp | 2025-05-21 |
©1994–2026 Check Point Software Technologies Ltd. All rights reserved.
Copyright | Privacy Policy | Cookie Settings | Get the Latest News
Fill in your business email to start


