


In recent years, “Pig Butchering” (also referred to as “杀猪盘 shāzhūpán“) scams have rapidly emerged as a significant global threat, primarily targeting individuals with fraudulent investment schemes. This type of scam, originally known for its roots in China, has transformed into a global phenomenon, where victims are led to believe they are making lucrative investments, often in cryptocurrency. The name “pig butchering” comes from scammers “fattening up” their victims by gaining their trust before seizing their funds, leaving the victims with significant losses.
The scam involves criminals engaging with targets through social media, direct messaging apps, and dating apps, sometimes for months, to build a sense of trust and familiarity.
Eventually, the victims are convinced to invest in what appears to be a legitimate venture, only to realize later that their money has been stolen. This scam is now global, with operations frequently run by groups in Southeast Asia.
According to the FBI, cryptocurrency-related scams, including pig butchering scams, accounted for a staggering $5.6 billion in reported losses in 2023, a sharp increase from previous years.
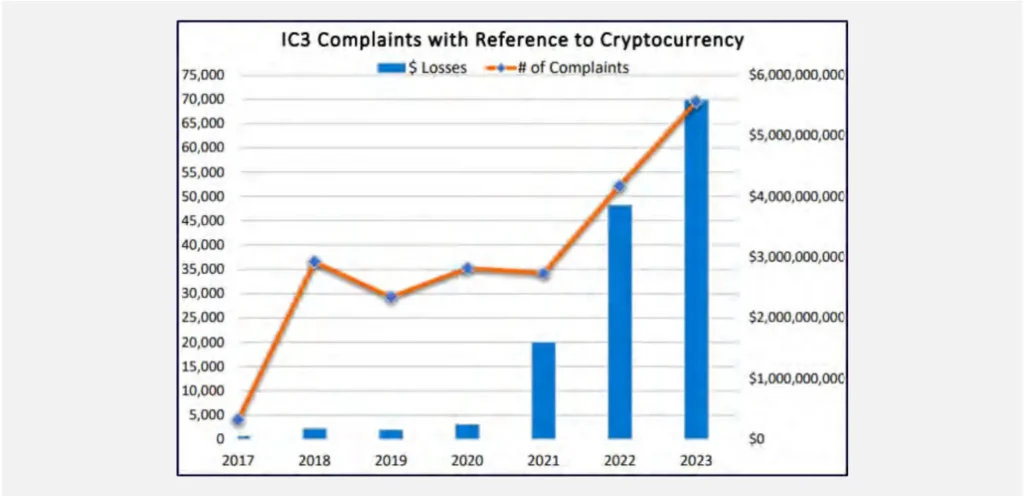
On a global scale, losses attributed to pig butchering and similar schemes were conservatively estimated at around $64 billion annually.
To demonstrate the dangers of pig butchering and investment scams, we have focused on analyzing and exploring domains that are known to be associated with these scams based on their website structure. These fraudulent websites often follow a similar template, aimed at deceiving potential victims into thinking they are engaging with a legitimate investment platform.
While most pig butchering scams are associated with Chinese-speaking threat actor groups, our investigation suggests that this specific scam appears to be linked mainly to threat actors originating in Africa, indicating the global expansion and diversification of such operations.
Scam websites typically feature a professional-looking home page promising high returns, a fabricated “About Us” section to establish credibility, and an “Investments” page promoting quick profits, often through cryptocurrency. Additional pages, such as Statistics, Registration, Login, and Cryptocurrency Prices, further enhance the illusion of legitimacy. A key feature across these sites is a chatbot, used to direct victims to messaging platforms like WhatsApp or Telegram for more personal interaction with scammers.
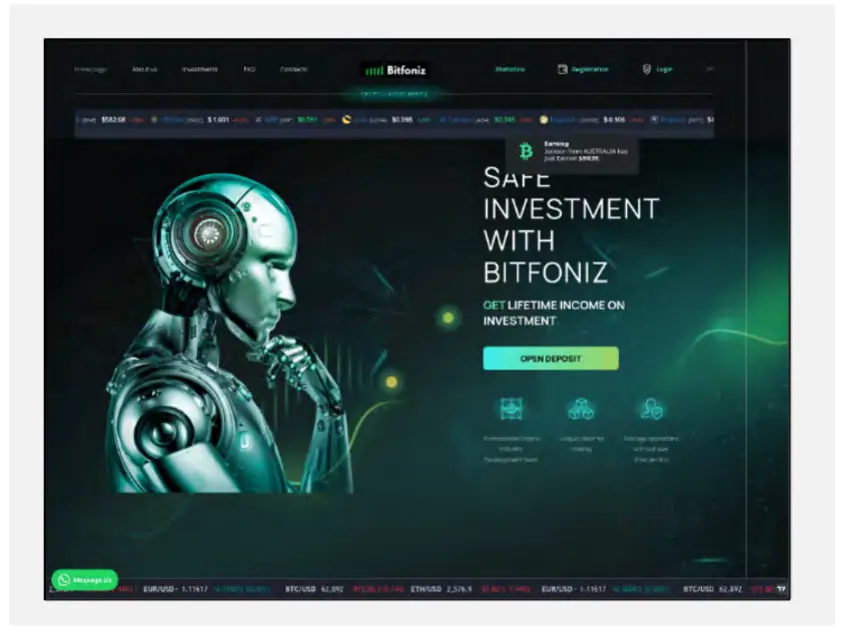
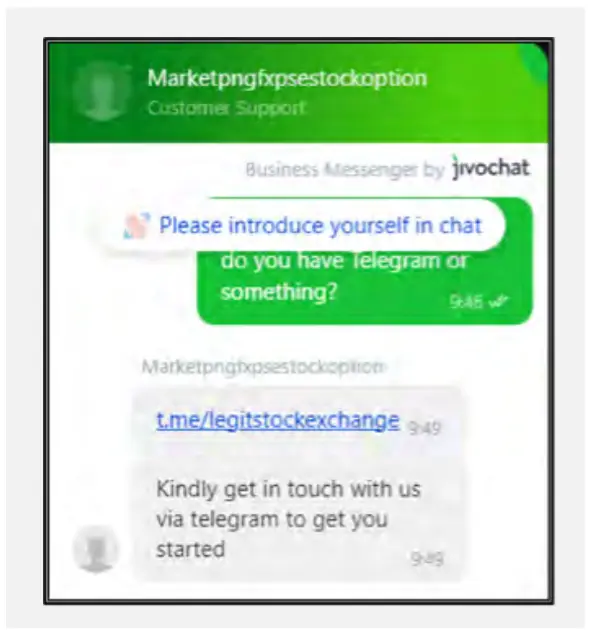
The combination of easily replicated website templates, the use of social engineering through chatbots, and the promise of high investment returns makes this scam highly effective in targeting all kinds of victims worldwide.
Origins and Components of Websites
We have identified that the first indications of threat actors using these website templates appeared in March 2022. In total, Cyberint identified over 1,000 domains that used this website template. The earliest YouTube instructional video we discovered was uploaded in September 2022 on a channel named “blex ony.” The video, narrated by a Nigerian individual, provides step-by-step instructions on setting up such a website. The video’s description includes a phone number, +2348088522446, for those interested in purchasing this template. It appears the channel features additional scam website templates for sale, which might indicate the involvement of a larger threat actor group.
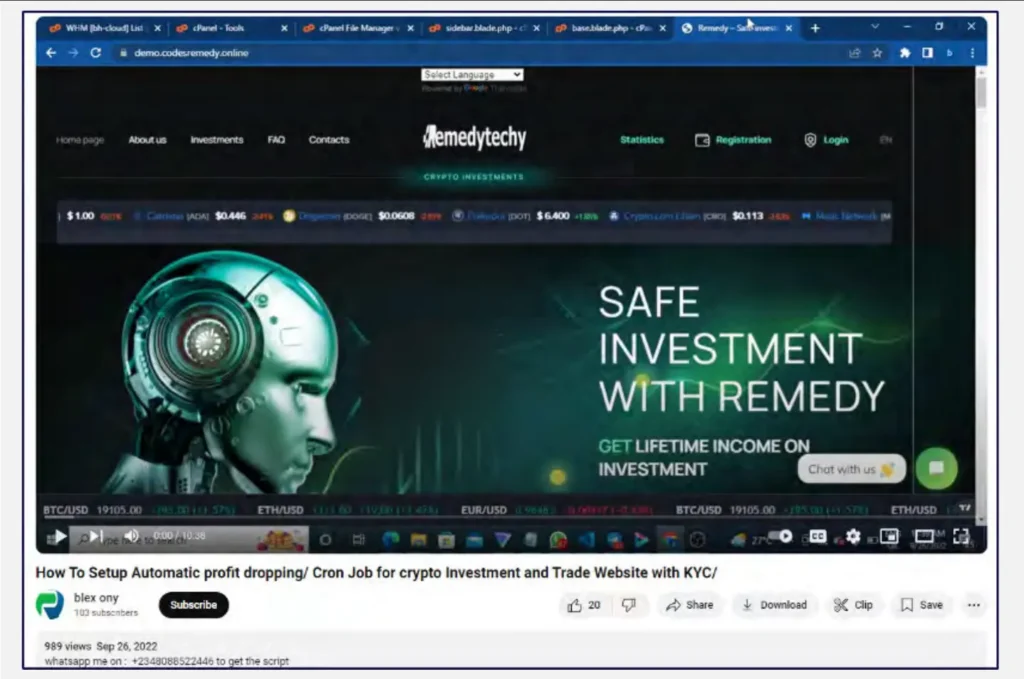
Furthermore, we identified another YouTube video offering the script for free, published by a channel named “Codexoo.” Upon accessing the link in the description, we were able to download the template script.
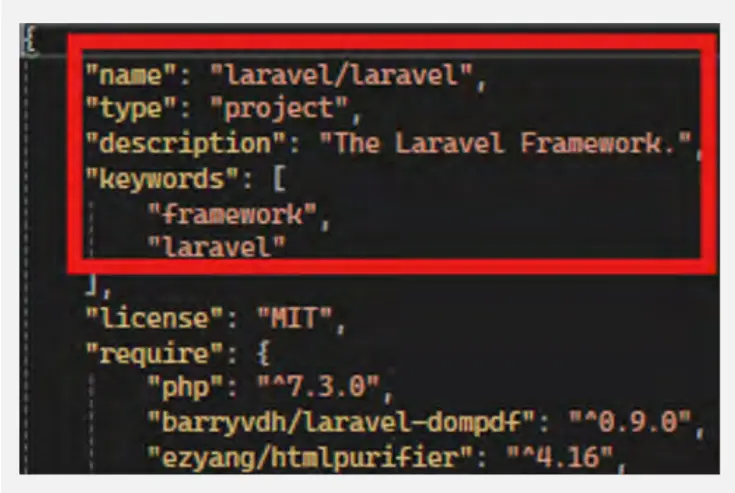
We identified that the scammers are using the Laravel framework based on the presence of certain files. The script folder includes files such as “composer.json” and other default files that are typically generated automatically when creating web applications with Laravel.
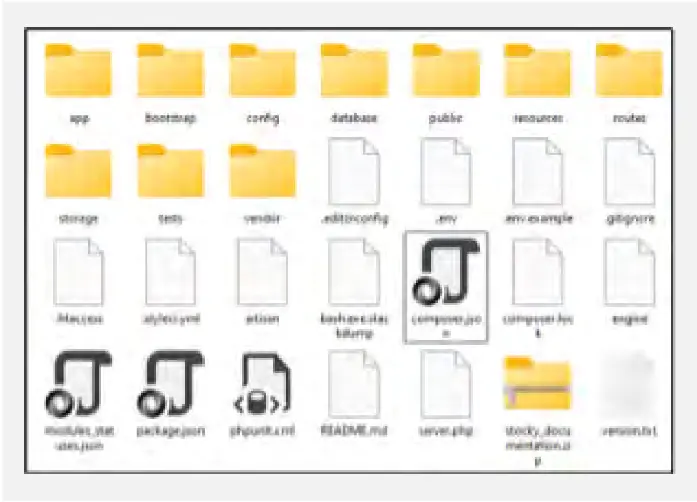
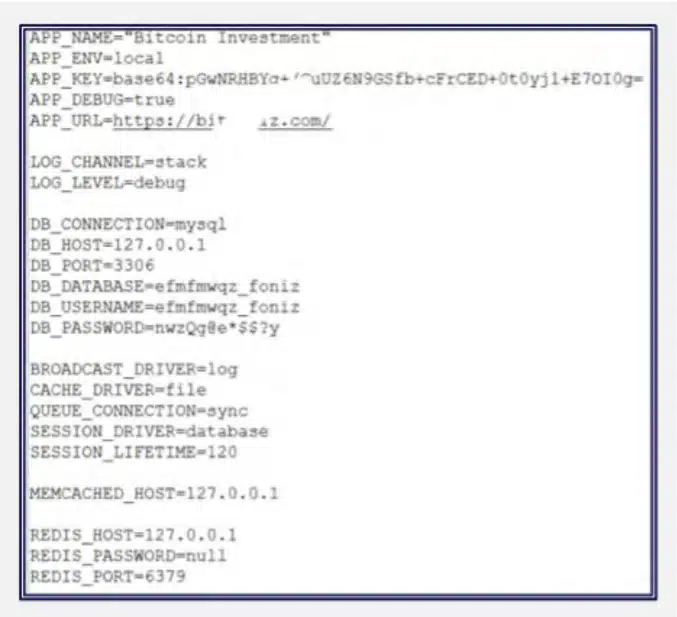
Our investigation actively leveraged poor security practices on six of the fraudulent platforms, enabling us to access internal directories and various sensitive files which are stored on these sites’ backends, including .env configuration files, logs files, and more. These types of files and directories are known to be associated with Laravel framework.
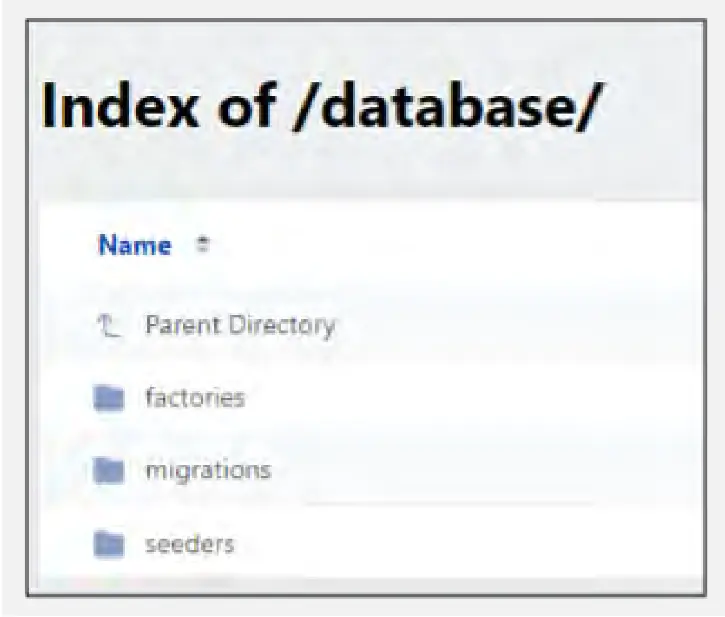
Additionally, we located directories where uploaded images are stored.
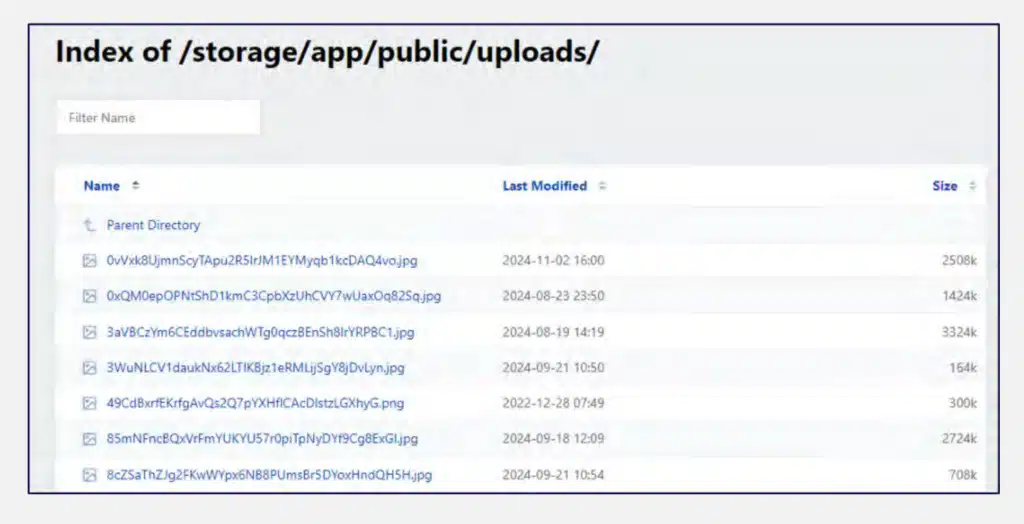
These platforms require victims to submit personal identification, such as ID cards, driver’s licenses, or passports, during registration, which can later be used for blackmail or sold as personal data.

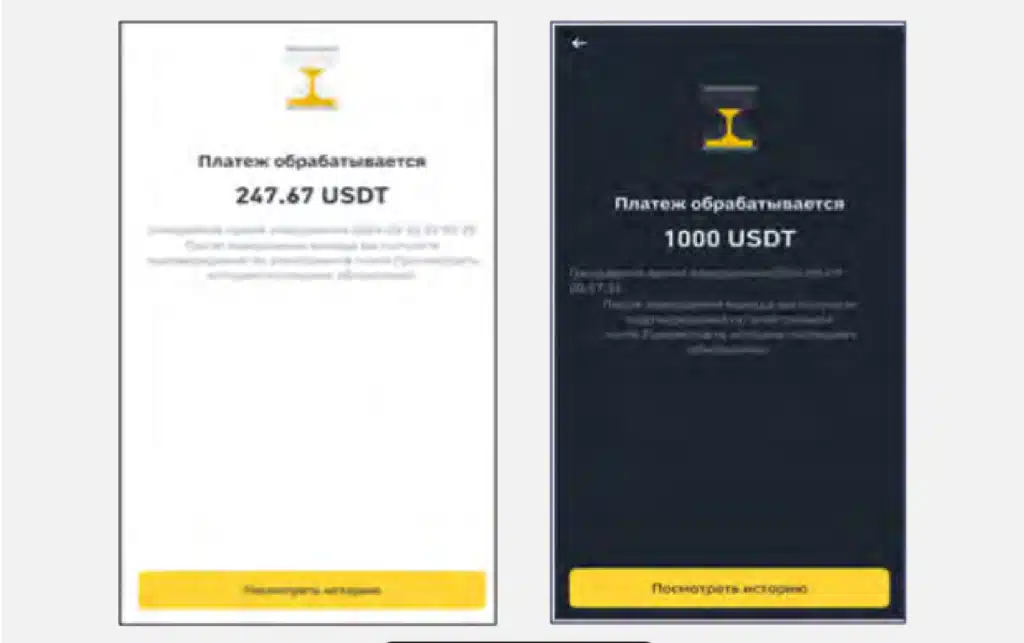
We also discovered images related to transaction confirmations, which reveal victims’ attempts to transfer funds to these fraudulent schemes. The total estimated losses for victims impacted by these six platforms amounts to several thousand dollars. However, as Cyberint has identified over 1,000 domains using this specific scam template, victim losses are likely in the tens or even hundreds of thousands of dollars.
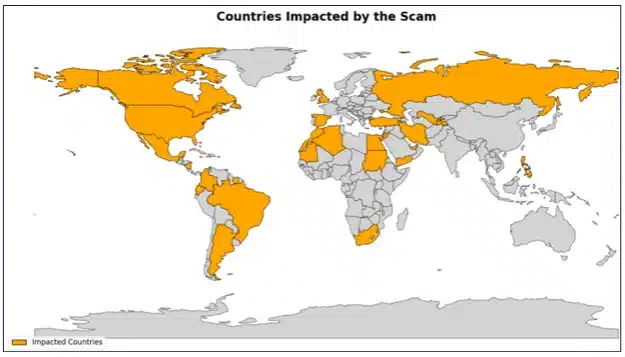
The impact of these 6 scam websites is worldwide, affecting a broad range of 27 countries, including: Algeria, Argentina, Brasil, Canada, Colombia, Dubai, Ecuador, Egypt, Iran, Jordan, Mauritania, Mexico, Morocco, Nicaragua, Philippines, Russia, South Africa, Spain, Sudan, Suriname, Tajikistan, Turkey, United Arab Emirates, United Kingdom, United States, Uzbekistan, and Yemen.
Based on the images, the victims come from diverse backgrounds, with no specific gender, age, or other demographic making an “ideal” target.
Our investigation has revealed that scam operations are primarily promoted via social media, with Facebook being a key platform. Scammers often impersonate “attractive” and “successful” men and women to lure potential victims into investing in fraudulent forex schemes. This tactic was first used by Chinese threat actors when pig butchering began in 2016, with romance scams being the primary method to lure victims. Scammers built fake relationships to gain trust before introducing fraudulent investments, similar to today’s approach of impersonating attractive, successful individuals on social media.
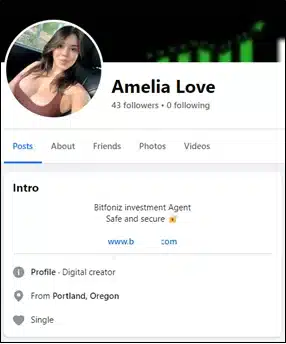
Scammers post about financial success and the ease of investment, often sharing fabricated success stories and providing step-by-step instructions for depositing funds. Some examples include:
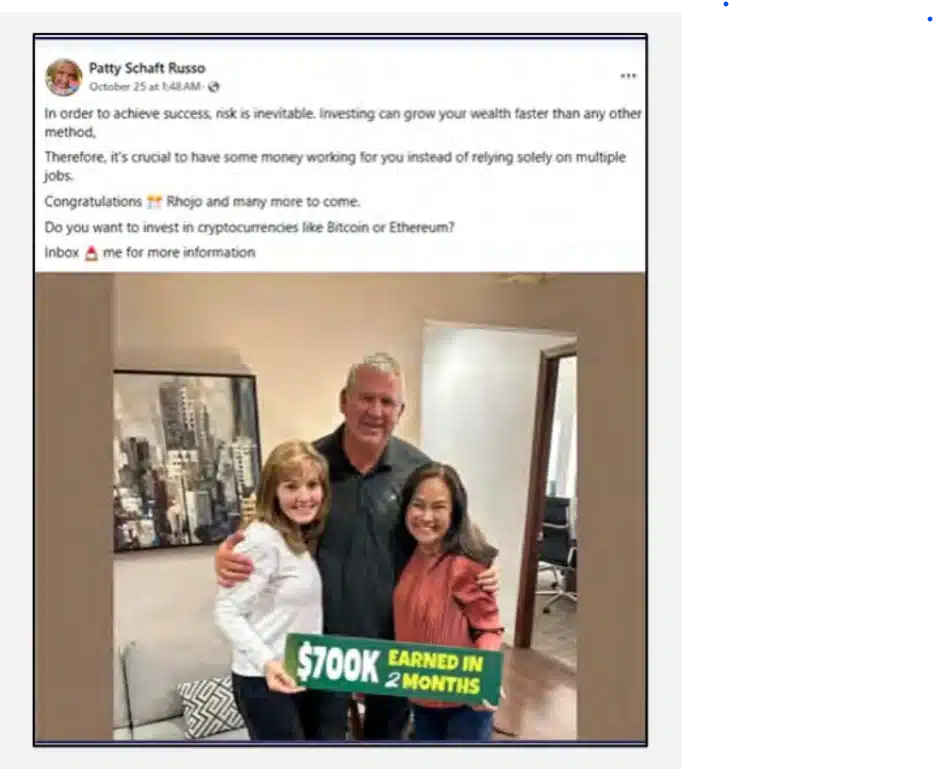
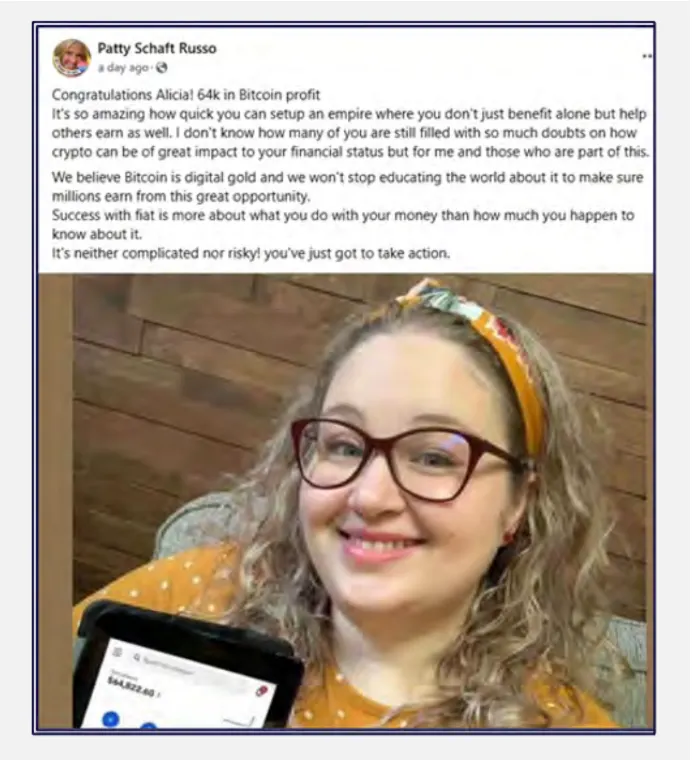
2. Motivational Posts:
Inspirational quotes paired with links to fraudulent sites, appealing to users’ desire for financial success
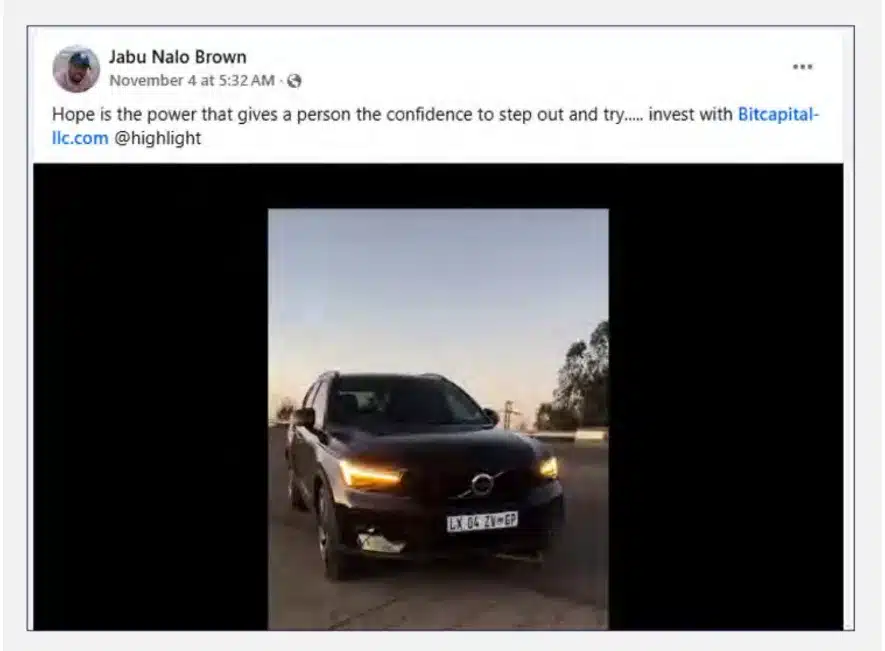
Our proactive controlled engagement revealed several key characteristics of this scam:
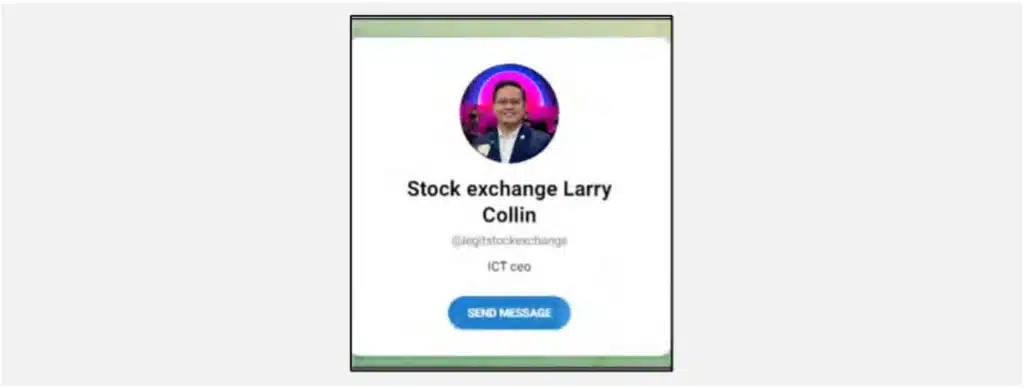
The original social media profiles of Larry Collin have issued warnings about impersonation and scams.
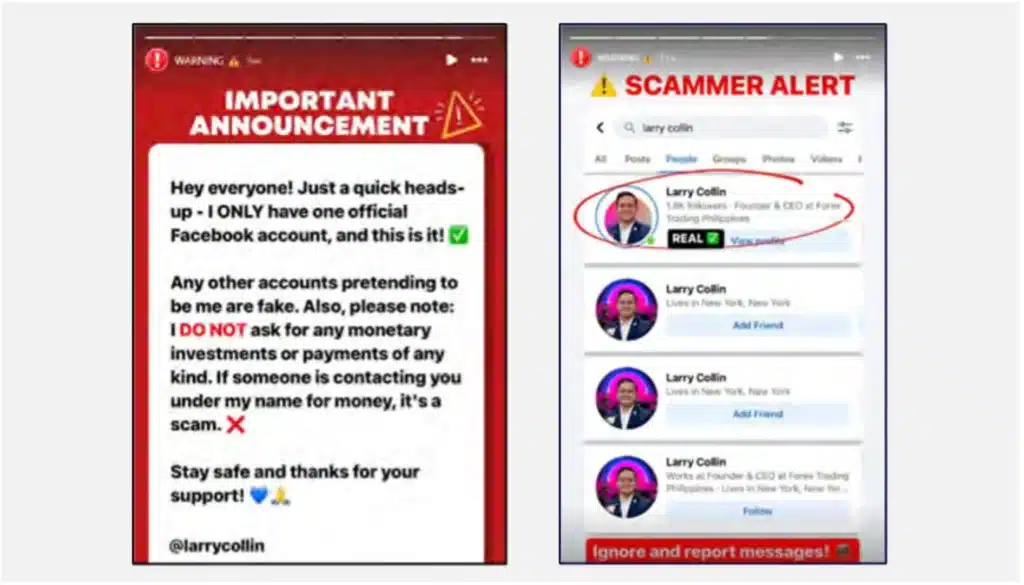
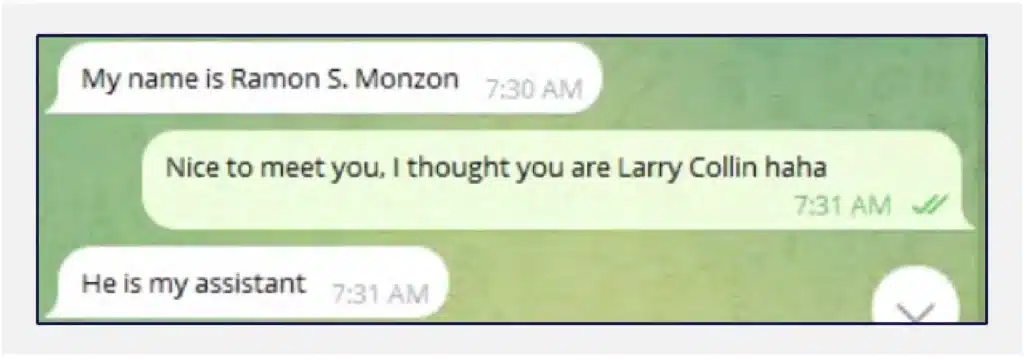
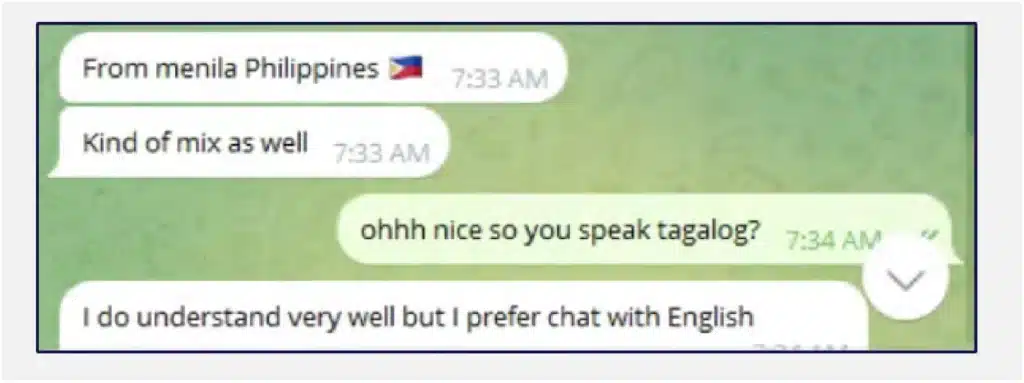

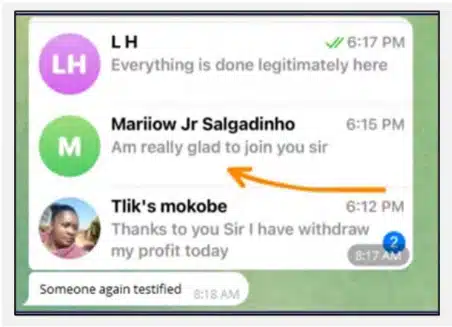

Pig butchering scams have grown from their origins in China to become a global threat, with some operations led by groups in Africa. Using social media, especially Facebook, scammers impersonate successful individuals to lure victims into fake investment schemes.
Threat actors exploit the general public’s limited knowledge of cryptocurrency, and combined with pig butchering techniques, this makes these types of scams increasingly prevalent and efficient.
Our investigation uncovered over 1,000 domains promoting these scams, relying on low-sophistication tactics to interact with victims. Despite this simplicity, these scams are estimated to cause significant financial losses across 27 countries, impacting diverse demographics with no specific “ideal victim” profile.
With the rise of AI, creating convincing and functional fraudulent platforms has become easier, likely fueling the continued growth of these scams as more types of threat actors get involved, attracted by high success rates.
Cyberint, now a Check Point company, reduces risk by helping organizations detect and mitigate external cyber threats before they have an adverse impact. The Check Point External Risk Management solution provides superior visibility through continuous discovery of the evolving attack surface, combined with the automated collection and analysis of vast quantities of intelligence from across the open, deep and dark web.
A team of global military-grade cybersecurity experts work alongside customers to rapidly detect, investigate, and disrupt relevant threats – before they have the chance to develop into major incidents. Global customers, including Fortune 500 leaders across all major market verticals, rely on Check Point External Risk Management to protect themselves from an array of external risks, including vulnerabilities,
misconfigurations, phishing, impersonation attacks, malware infections, exposed credentials, data leaks, fraud, and 3rd party risks.


©1994–2025 Check Point Software Technologies Ltd. All rights reserved.
Copyright | Privacy Policy | Cookie Settings | Get the Latest News
Fill in your business email to start


