


As with every year, the Verizon DBIR is released, with data involving more than 10,000 breaches that
have been dissected and used to create the report’s baseline.
Cyberint’s Research team inspected the document to understand where the cyber security realm is heading, the important trends in data breaches and incidents, and what we need to look for moving forward in 2024.
The key points we found valuable and insightful in this report are the significant rise in vulnerability exploitation, the solid state of the ransomware threat in our landscape, the human factor, and supply chain campaigns and how they intertwine and affect the scale and severity of successful attacks.
After the initial reading, it is pretty noticeable how “MOVEit” made an impact in 2023 and shows the direction it leads in 2024. Even 2025. The phrase “MOVEit” appears over 25 times (!!!) on the new DBIR report, causing us to delve deeper into the data.


As the 100-page report suggests, the 2024 trend (continuing from 2023) is the ongoing rise in vulnerability exploitation, their use by Ransomware groups, and the fact that zero-days can be used as a lethal weapon in the battle for the next supply chain attack.
One data point that first pops out is the “180% increase in the exploitation of vulnerabilities”.
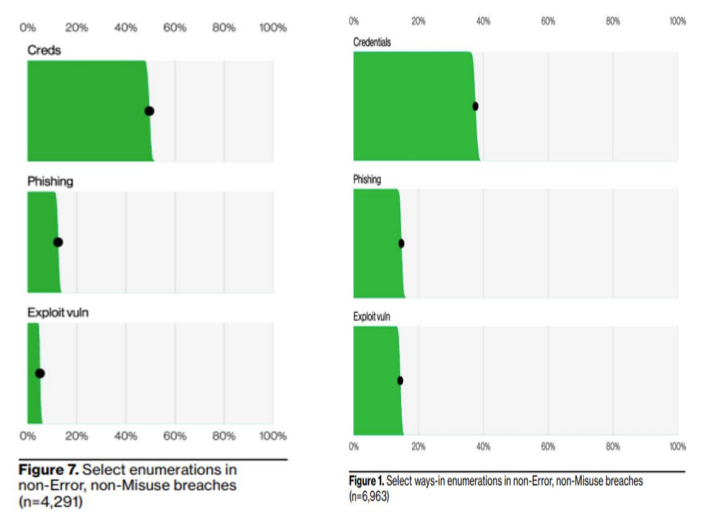

The figure above shows that credential-based attacks and phishing are stuttering compared to the rise of “Exploit Vuln” and marks it as a true contender for the initial breach entry point. Vulnerabilities are clearly marked as a solid initial access vector.
We can learn from this stat that, presumably, employee awareness and cybersecurity awareness, in general, led to a decrease in social engineering-based attacks such as phishing – forcing threat actors to “step up” and use the heavy cannons as they look to exploit and research for zero-day vulnerabilities.
The report mentions “Log4j” and the fact that the market was swift to understand the volume and magnitude of such vulnerability’s impact on the industry and the minimal impact it suffered. However, that will not be the case with every new vulnerability that is being discovered.

Another important Verizon insight discusses “the weakest links” – supply chain attacks. For us to solve modern complex technological issues, many companies – both enterprises and startups, use third-party SaaS products that enhance and make our lives much easier. Examples of day-to-day uses are file storage services, authentication services, password managers and even computing on demand.
Although very useful, these services are also expanding our attack surface. Given that, we can see in Verizon’s report a significant rise in recent years in the connections between breaches and supply chain solutions that have been compromised by threat actors.
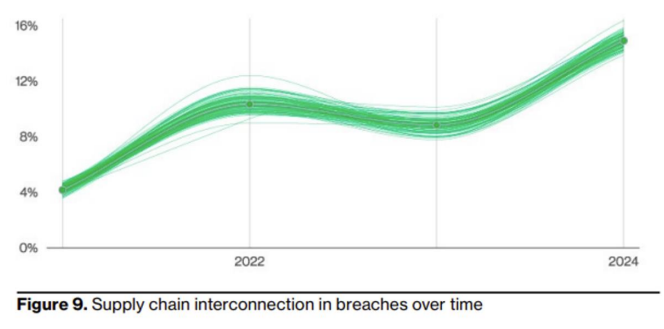
Although it has been fairly slow to be adopted by threat actors, it seems like in 2024, more and more threat actors will adopt this trend and look to compromise third-party services as much as possible.
Supply Chain + Vulnerability + MOVEit + Extortion = Chaos
As the report suggests, Ransomware is still one of the top threats. The focus on encryption is no longer, and the Extortion part is more dominant than ever when every small-time threat actor can use/create a ransomware tool/buy credentials in the underground, whether from a broker or from an underground marketplace, infiltrate, and deploy their tool.
However, more groups will be using zero-days or known vulnerabilities.
Although we believe that a great enterprise must consider and adopt the proven method of working with SaaS and third-party services, we must mention its associated risks.
As mentioned, we expand our attack surface once we expand our toolset. A great example is the MOVEit campaign initiated by Cl0p earlier in 2023 as they were able to compromise the MOVEit service of hundreds of companies, leading to a massive campaign that caused estimated damage of tens of millions of U.S. dollars, both in disturbing business continuity and ransom paid by the victims.
On the one hand, Verizon strongly claims that the ransomware threat is still the most prominent threat for organizations worldwide, and we in Cyberint see the creation of new groups almost weekly. On the other hand, we can’t expect every group to be as talented and as capable (even in a matter of funds), as the major groups we have today, such as Cl0p, LockBit3.0, ALPHV and even the dismantled Conti – Group. These groups have the capabilities of not just infiltrating an organization by phishing, leaked credentials and bribes, but also the means and talent to research for zero-day vulnerabilities in strategic services that many organizations use like in the MOVEit example.
The human element of our attack landscape is a noticeable threat we must consider. According to Verizon’s report, 68% of the breaches involved the human element – roughly the same percentage as last year’s 2023 DBIR report.
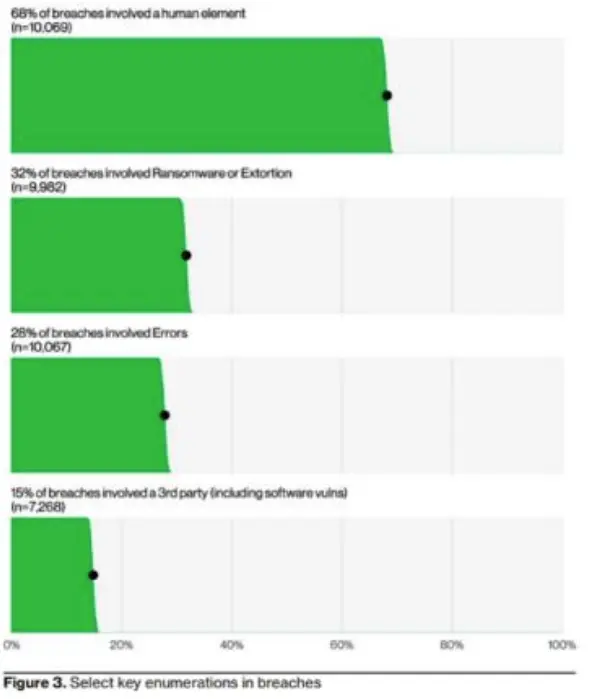
Phishing, as expected, is one of the top vectors of gaining initial access, and, as presented in the report, only 20% of users reported phishing in simulation engagement while 11% of the users who clicked the email also reported it as phishing.
The report also states the median time for users to click on a phishing simulation link is just 21 seconds, and the median time to actually submit your sensitive data is 28 seconds, which, as the reports states, “leads to an alarming finding: The median time for users to fall for phishing emails is less than 60 seconds.” However, most of this is already known, and almost all organizations routinely imply security training and awareness.
In addition, The Cyberint Research Team’s claim is that a successful campaign from a threat actor’s perspective is whether the credentials were obtained, and not the time it took the victim to make a mistake, and 60 seconds or 60 minutes is the same in that matter.
The report also emphasizes breaches caused by human errors, such as service misconfiguration and other non-compliance with best practices.
When looking at the numbers, there seems to be a significant increase from 20% of the cases last year to 35% in this year’s report. In addition, the report also claims that there is a chance that these cases “possibly indicate a rise in Carelessness, although it may also reflect increased data visibility with new contributors” — meaning that given that we have more data to rely on, we have more cases to show.
The DBIR 2024 report shed a lot of light that enforces many of the Cyberint’s Research Team’s predictions for 2024 as we have a more solid point of view on the threats, we shared in concluded in our own early year report.
While third-party services are making our lives much easier, they also attract the attention of many threat actors, especially after last year’s successful MOVEit campaign. The ransomware threat is here to stay, as it has been for the past few years, going back to at least 2019. Although we had some amazing operations done by the law authorities, it still poses the main threat to organizations worldwide.
Finally, given these two important points, threat actors are forced to step up their game as they will look to target more vulnerabilities as an initial access vector rather than phishing campaigns and bribes—which we already see happening in this report as well.
©1994–2026 Check Point Software Technologies Ltd. All rights reserved.
Copyright | Privacy Policy | Cookie Settings | Get the Latest News
Fill in your business email to start


