

Cross-site scripting (XSS) is one of the greatest security threats organizations face. Malicious codes are injected into otherwise trusted websites using HTML, JavaScript, VBScript, ActiveX and Flash allowing attackers to hijack accounts to steal user data, change user settings, access cookies and falsely advertise.
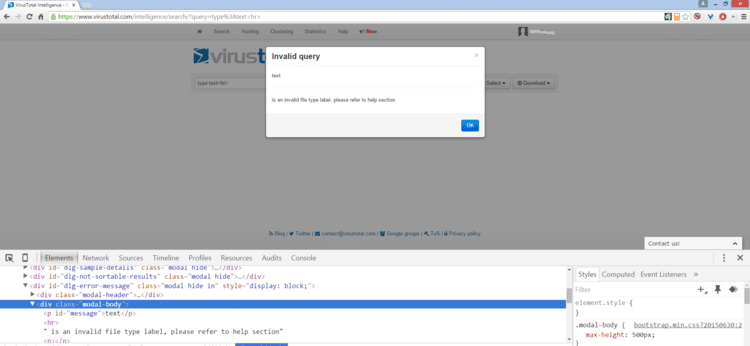
CyberInt’s offensive team recently identified a reflected cross-site scripting vulnerability within VirusTotal’s intelligence search component. VirusTotal allows organizations to use various search queries; however, if a search query is filled with a mismatched value, an error code pops up. For example, when we tried to launch a search for “type: Test” the application said there is no such search query and returned the error code below.
Our team found that the VirusTotal application does not perform input validation on the search query parameter, which could contain malicious code that would trigger a successful reflected XSS attack. This could happen, for example, by injecting the <hr> HTML tag as a search query parameter.
By using WAF or other security protections, VirusTotal blocked some XSS payloads that perform malicious action by disallowing the following characters:
We were able to get around that by developing a unique payload without the disallowed characters. To evade the use of spaces, for example, we figured out that using the ‘/’ character converted to a space on the server side, allowing the beginning of our payload to start with ‘<script/src=’. Next, we evaded the URI restriction by figuring out that “//” characters converted to ‘http://’ or ‘https://’ on the server side, creating the payload: ‘//path_to_external_js_file’. By connecting all the dots, we were able to generate this successful payload.
It’s crucial for all organizations to understand the risks and threats associated with XSS. Security experts have identified this vulnerability even in some of the world’s most popular and highly-secure websites, including Google, Amazon, Facebook and PayPal. Free prevention tools don’t go far enough.
Our advice for preventing XSS attacks includes:
Fill in your business email to start


