I love to get stuck in and let the creative juices flow. My strengths lie in idea generation, development and execution. Over 5 years experience in B2B cybersecurity. I reign supreme when my imagination and creativity can run wild.
We know how busy security teams are now, so to save you time, we thought we would answer the top questions we get asked before you jump on a call with us. Here are our top 20:
Cyberint continuously discovers the open, deep and dark web to detect all of the external IT assets in a customer’s digital footprint. The process is fully automated and passive so it does not actively validate or test any security controls. The discovery process will not “set off any alarm bells” or give security teams the impression an attack is underway. There is no impact on normal operations.
There is an optional additional feature named active exposure validation, which we detail below that does actively validate.
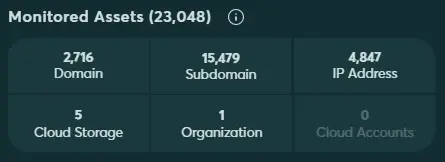
Using publicly-available data, like DNS records, WHOIS data, and SSL certificates, Cyberint’s Attack Surface Management module is able to map out an organization’s external attack surface. All discovered assets are checked for common security issues. The categories of assets detected are: IP addresses, domains, subdomains, cloud storage, and organizations (i.e. trademarked brands).
These are the types of security issues we identify:
About Active Exposure Validation (AEV): Cyberint’s AEV capability goes beyond typical CVE detection to actively test for exploitability. AEV also performs other automated tests to uncover common security issues in your organization’s digital assets that fall outside the scope of a vulnerability database. Alerts are issued in real time so you can quickly identify and remediate your most urgent risks. AEV enables the crucial validation step to be tackled in the CTEM framework.
By default – weekly, but this can be changed per the client request and needs (can be daily if needed). We have 5 asset types: IPs, domains, Sub-domains, Cloud storage and organization names. Each discovered asset is counted as a single asset.
Yes and yes, each asset has one of three defined statuses: “in scope”, “out of scope” or “unvalidated”.
Whenever you manually add an asset, you have two options: you can either manually run a scan or wait until the next discovery cycle, which checks for issues on your assets. Once the discovery process starts, the new assets will be included, and any issues will be identified alongside the newly added assets. Additionally, the security score is subject to change based on the findings related to the new assets.
Yes, we discover S3 buckets, Google cloud storage, Azura data lakes, Aazure storage blob, AWS accounts & more.
Yes, as our platform is multi-tenant, we can set up an Attack Surface Management (ASM) instance for each brand and monitor the brands separately.

With Cyberint, now a Check Point Company’s automation, we can precisely determine which assets are part of your organization’s external IT infrastructure. Moreover, we offer automated validation and scoping based on your preferred confidence level (e.g. 80% or 90%). This reduces the time and effort involved in scoping and asset validation, resulting in a seamless single flow that occurs automatically from discovery to alerting (Figure 2 & 3).
Discovered assets that are below your selected threshold are not automatically added into your inventory and instead await a manual review. In addition, our team of highly skilled and experienced analysts review the discovered assets and only if it is relevant do they update the confidence score and send it to you.
We assign a confidence score to each discovered asset that says how confident Cyberint is that the asset belongs to you. So if a newly discovered asset has an 80% confidence score, that means we are 80% sure that asset is part of your attack surface.
When the automation shows a finding of medium confidence, before it reaches you, our analysts act as an extension of your team and review it, either deciding if it is a false positive or forwarding it on to you with added context.
All active exposure validation alerts have gone through validation and therefore have a high confidence score.
Each issue’s risk score is calculated according to a sophisticated algorithm and depends on a number of factors including the type of issue found and the asset that is related to the issue.
Each issue then get’s a score (low, medium, high, very high) and an overall calculation is then made to give the total risk of the issue type.
Yes. All alerts can be automatically sent to SIEM/SOAR platforms to trigger automated playbooks. We have an API that can integrate our information into existing SIEM/SOAR solutions and corelate with information from other intelligence platforms. We also integrate with Splunk, Azure AD, AWS, JIRA, OKTA, Qradar, XSOAR out of the box.
The takedown time varies between hours and days. Our average takedown MTTR is 22 hours. Since the takedown process also involves hosts/registrars/SM platforms that are not under Cyberint’s control, we cannot predict the time it takes them to respond and takedown illegal content based on our request.

We cannot guarantee that a take down will be successful. That being said, our success rate is very high at over 98% in Q1 2025 (99% for phishing takedowns)
We have a dedicated takedown team that specializes in takedowns. We have forged partnerships with a diverse range of hosting providers, registrars, social media platforms, and app stores, and we have streamlined processes that are customized to each case. When a takedown request is initiated, a form is automatically completed and sent from a Cyberint email address to the relevant host, outlining the reasons for the request and the associated risks. Our team then tracks the requests, and the status can be seen in the “Takedown Requests” dashboard. We can take down phishing webpages, phishing domains, social media accounts, social media posts, paste sites, GitHub repositories, mobile apps, and more.
Yes, you can define this use case as a prioritized requirement with your dedicated analyst and we can add websites like these into scope for continuous monitoring.
We cannot prevent your website from being copied BUT we can alert you immediately if it happens and help with the steps to get it taken down. We can also monitor for lookalike domains.
We cover thousands of sources from the clear, deep, and dark web. We cover:
and more. 5% of our sources are considered “Dark web”. The rest are in the clear/deep web.

Each source is crawled and scraped according to the allowed policies on it. For example, if a dark web forum is monitored for suspicious scraping activity, we will make sure we collect information at a pace that does not raise any suspicion. We try to keep each source up to date with no longer than a week between each scraping (often much much more).
We have automated translation mechanisms in place and our the Cyberint team speaks over 22 languages fluently, including Russian, Arabic, English, Chinese, Japanese, Filipino languages like Tagalog, Ilocano and Ilonggo and more.
Our sources team is constantly looking for and adding more sources. Every request is examined by the team and we are more than happy to add additional sources that can provide value to our customers. The turn-around time for adding a source is relatively short (1-4 weeks usually).
Cyberint has a very experienced research team that tracks global threat events and releases periodic research reports. Every major global event that occurs is covered by the Cyberint research team. – For example, we have published report on: Scattered Spider, The Russian – Ukraine war, the Log4shell vulnerability, specific Ransomware groups tracking and more.
Cyberint’s research team can create reports on any desired subject, using “investigation hours”. Each customer can purchase these hours and each research is priced based on the number of hours required to complete it. The subjects vary between VIP exposure reports, industry related threats, Incident response, Deep investigations and more

Cyberint continuously discovers the open, deep and dark web to detect all of the external IT assets in a customer’s digital footprint. The process is fully automated and passive so it does not actively validate or test any security controls. The discovery process will not “set off any alarm bells” or give security teams the impression an attack is underway. There is no impact on normal operations.
Using publicly-available data, like DNS records, WHOIS data, and SSL certificates, Cyberint’s Attack Surface Management module is able to map out an organization’s external attack surface. All discovered assets are checked for common security issues. The categories of assets detected are: IP addresses, domains, subdomains, cloud storage, and organizations (i.e. trademarked brands).
These are the types of security issues we identify:
Certificate Authority issues
Compromised Credentials
Email Security issues
Exploitable Ports
Exposed Cloud Storage
Exposed Web Interfaces
Hijackable Subdomains
Mail Servers In Blocklist
SSL/TLS issues
By default – weekly, but this can be changed per the client request and needs (can be daily if needed). We have 5 asset types: IPs, domains, Sub-domains, Cloud storage and organization names. Each discovered asset is counted as a single asset.
Yes and yes, each asset has one of three defined statuses: “in scope”, “out of scope” or “unvalidated”.
Whenever you manually add an asset, you have two options: you can either manually run a scan or wait until the next discovery cycle, which checks for issues on your assets. Once the discovery process starts, the new assets will be included, and any issues will be identified alongside the newly added assets. Additionally, the security score is subject to change based on the findings related to the new assets.
Yes, we discover S3 buckets, Google cloud storage, Azura data lakes, Aazure storage blob, AWS accounts & more.
Yes, as our platform is multi-tenant, we can set up an Attack Surface Management (ASM) instance for each brand and monitor the brands separately.
With Cyberint’s automation, we can precisely determine which assets are part of your organization’s external IT infrastructure. Moreover, we offer automated validation and scoping based on your preferred confidence level (e.g. 80% or 90%). This reduces the time and effort involved in scoping and asset validation, resulting in a seamless single flow that occurs automatically from discovery to alerting.
Discovered assets that are below your selected threshold are not automatically added into your inventory and instead await a manual review. In addition, the Cyberint’s team of highly skilled and experienced analysts review the discovered assets and only if it is relevant do they update the confidence score and send it to you.
We assign a confidence score to each discovered asset that says how confident Cyberint is that the asset belongs to you. So if a newly discovered asset has an 80% confidence score, that means we are 80% sure that asset is part of your attack surface.
When the automation shows a finding of medium confidence, before it reaches you, our analysts act as an extension of your team and review it, either deciding if it is a false positive or forwarding it on to you with added context.
Each issue’s risk score is calculated according to a sophisticated algorithm and depends on a number of factors including the type of issue found and the asset that is related to the issue.
Each issue then get’s a score (low, medium, high, very high) and an overall calculation is then made to give the total risk of the issue type.
Yes. All alerts can be automatically sent to SIEM/SOAR platforms to trigger automated playbooks. We have an API that can integrate our information into existing SIEM/SOAR solutions and corelate with information from other intelligence platforms. We also integrate with Splunk, Azure AD, AWS, JIRA, OKTA, Qradar, XSOAR out of the box.
The takedown time varies between hours and days. Since the takedown process also involves hosts/registrars/SM platforms that are not under Cyberint’s control, we cannot predict the time it takes them to respond and takedown illegal content based on our request.
Got questions for a Cyberint analyst? Contact us today!
We cannot guarantee that a take down will be successful. That being said, our success rate is very high at over 95% for 6 consecutive quarters.
We have a dedicated takedown team that specializes in takedowns. We have forged partnerships with a diverse range of hosting providers, registrars, social media platforms, and app stores, and we have streamlined processes that are customized to each case. When a takedown request is initiated, a form is automatically completed and sent from a Cyberint email address to the relevant host, outlining the reasons for the request and the associated risks. Our team then tracks the requests, and the status can be seen in the “Takedown Requests” dashboard. We can take down phishing webpages, phishing domains, social media accounts, social media posts, paste sites, GitHub repositories, mobile apps, and more.
Yes, you can define this use case as a prioritized requirement with your dedicated analyst and we can add websites like these into scope for continuous monitoring.
We cannot prevent your website from being copied BUT we can alert you immediately if it happens and help with the steps to get it taken down. We can also monitor for lookalike domains.
We cover thousands of sources from the clear, deep, and dark web. We cover:
Search engines such as Bing and Google
All the major cybercrime forums such as ExposedVC, GenesisMarket and Nulled
Instant messaging platforms such as Telegram & Discord
Social media
Blogs
GitHub and other pastesites
Application stores
File sharing websites
Security Feeds
Data leakage sites
Credit Card stores
Blackmarkets such as RussianMarket and 2easy.shop
Malware logs
Dark networks
and more. 5% of our sources are considered “Dark web”. The rest are in the clear/deep web.
Each source is crawled and scraped according to the allowed policies on it. For example, if a dark web forum is monitored for suspicious scraping activity, we will make sure we collect information at a pace that does not raise any suspicion. We try to keep each source up to date with no longer than a week between each scraping (often much much more).
We have automated translation mechanisms in place and our the Cyberint team speaks over 22 languages fluently, including Russian, Arabic, English, Chinese, Japanese, Filipino languages like Tagalog, Ilocano and Ilonggo and more.
Our sources team is constantly looking for and adding more sources. Every request is examined by the team and we are more than happy to add additional sources that can provide value to our customers. The turn-around time for adding a source is relatively short (1-4 weeks usually).
Cyberint has a very experienced research team that tracks global threat events and releases periodic research reports. Every major global event that occurs is covered by the Cyberint research team. – For example, we have published report on: Tthe Russian – Ukraine war, the Log4shell vulnerability, specific Ransomware groups tracking and more.
Cyberint’s research team can create reports on any desired subject, using “investigation hours”. Each customer can purchase these hours and each research is priced based on the number of hours required to complete it. The subjects vary between VIP exposure reports, industry related threats, Incident response, Deep investigations and more
Fill in your business email to start