


Highly motivated, problem solver, dot connector, energetic multi-dimensional & professional management with commercially oriented, customer service skills & PMO abilities in high-growth, fast-paced organizations.
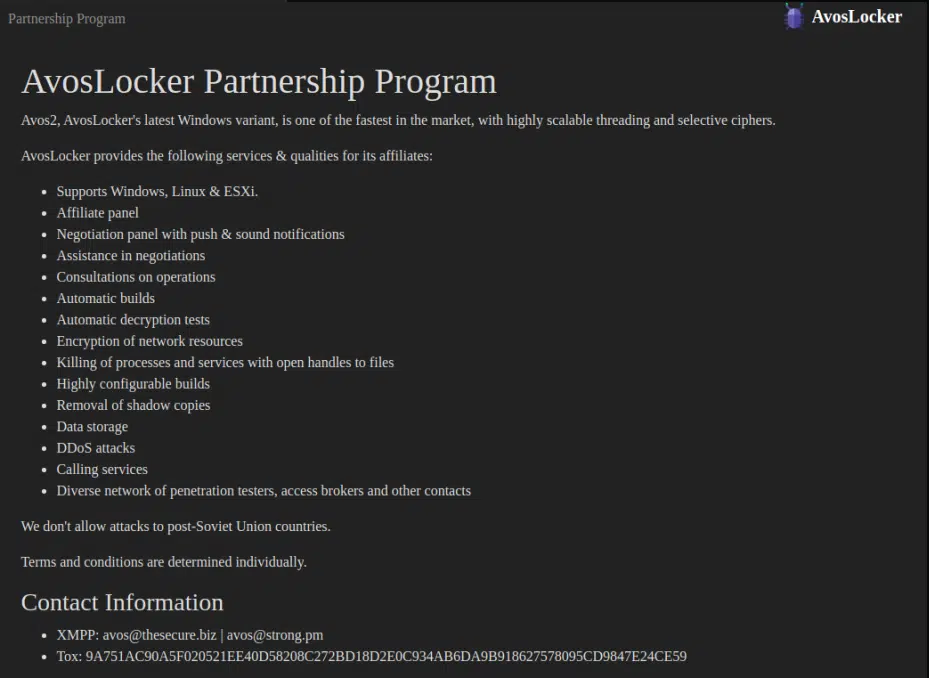
AvosLocker is a relatively new ransomware written in C++ that was first seen in June 2021. Their business model is ‘Ransomware-as-a-Service’ (RaaS), and even though they have been operating for less than a year now, they’ve been successful overall when it comes to victims. The group openly and publicly tries to recruit new members to its team and operates a TOR leak site, showcasing the latest victims, as all other ransomware groups do.
In the hope of staying updated, the group recently created a Linux version that targets the ESXi platform, which tries to appear in markets other than the usual major Windows.
AvosLocker uses what is called “double-extortion”, which relies both on encrypting the data and files, making them unusable, as well as stealing the data, and demanding a ransom for not leaking it publicly.
The team’s top priorities, as with other ransomware groups, are both money and fame.
To this point, since AvosLocker ransomware operations started, there have already been over 60 different victims mentioned in their leak site, a good indication of their ongoing attempts to make a dramatic impact on the ransomware landscape.
Based on the ransomware business model employed by most groups, AvosLocker included, victims will typically be selected based on their ability to pay a significant ransom.
As AvosLocker uses a Ransomware-as-a-Service (RaaS) business model, which is a subscription-based model, that allows affiliates to use developed ransomware tools, the focus of specific sectors or regions tends to spread, As the ability to infect different sectors or geo-locations rise, more companies could find themselves victims.
We have also seen the AvosLocker group posting ads on different forums, to attract new affiliates, offering them a share of the ransom payments.
As with most ransomware attacks, malspam email campaigns are the more dominant way of initial intrusion, since they are relatively easy to deploy and could be somewhat targeted at several employees of a company, with some likelihood of success.
Other than the usual case of malspam, we’ve also noticed chatters about malicious ads being used as an initial intrusion method. These are used by a service called HQ Advert. This service is used to distribute advertisements on different forums and messaging services.
It has been reported that the use of HQ Advert, as well as other similar services, has been used to distribute AvosLocker as malicious ads. However, we can tell that these are not the majority of cases, and malspam campaigns still remain the key method of propagation.
Before going into the active phase of encrypting the files, AvosLocker will set the ground, and try to delete both shadow copies of the Windows OS, as well as backups, to disrupt any restore processes to overcome the ransomware infection.
It will also leverage PDQ Deploy, which is a commercial software deployment tool built to allow you to automate your patch management, and used to push Windows scripts to the targeted machines. These scripts are sent before the victims’ machines are rebooted into Safe Mode, which is done to try and bypass security controls, as they will usually not run on Safe Mode.
AvosLocker, reported being used manually, also makes use of the AnyDesk remote administration tool, to allow remote connection to the infected machine to further manually inspect and operate it, even when a bug or a mishap occurs during normal infection of the ransomware.
Since the reboot will disable different types of drivers from loading after the reboot to Safe Mode, AvosLocker threat actors have set up the supported drivers to load after the restart, to allow the AnyDesk tool to still run in Safe Mode. This indicates a certain level of sophistication within their operations. Using AnyDesk could also be as another way of future backdoors to be deployed on the infected instances, for future attack or access at any time.
The encryption phase takes place using a multi-threaded process, to allow it to encrypt all located files at a relatively fast pace, to allow the ransomware activity to finish.
The encryption is 256-bit custom AES.
During the encryption phase, AvosLocker will first try and map all relevant files for encryption, and then both encrypt all drives and their content, as well as search for hidden or not network shares.
This will allow it to propagate internally and laterally move to other locations that might hold more valuable content that will be used as an extortion method when asking for the ransom.
After each file is successfully encrypted, the extension .avos will be appended to the file name.
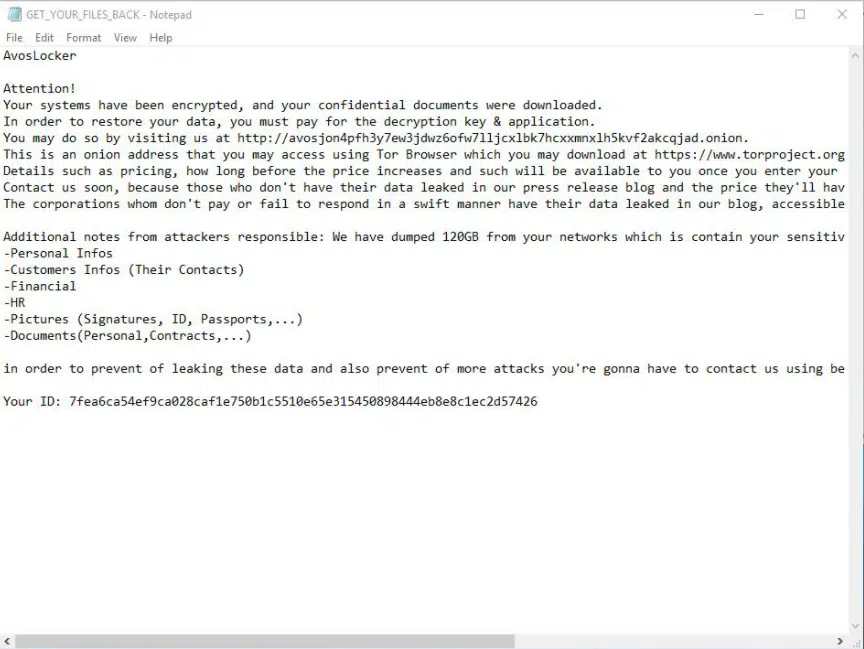
A ransom note is created with the name GET_YOUR_FILES_BACK.txt in every directory, and once opened will tell you about your encrypted files, and detailed instructions on how to retrieve them.
Each infection will have its own ID, which will be used to approach the TOR site, to continue the ransom payment process.
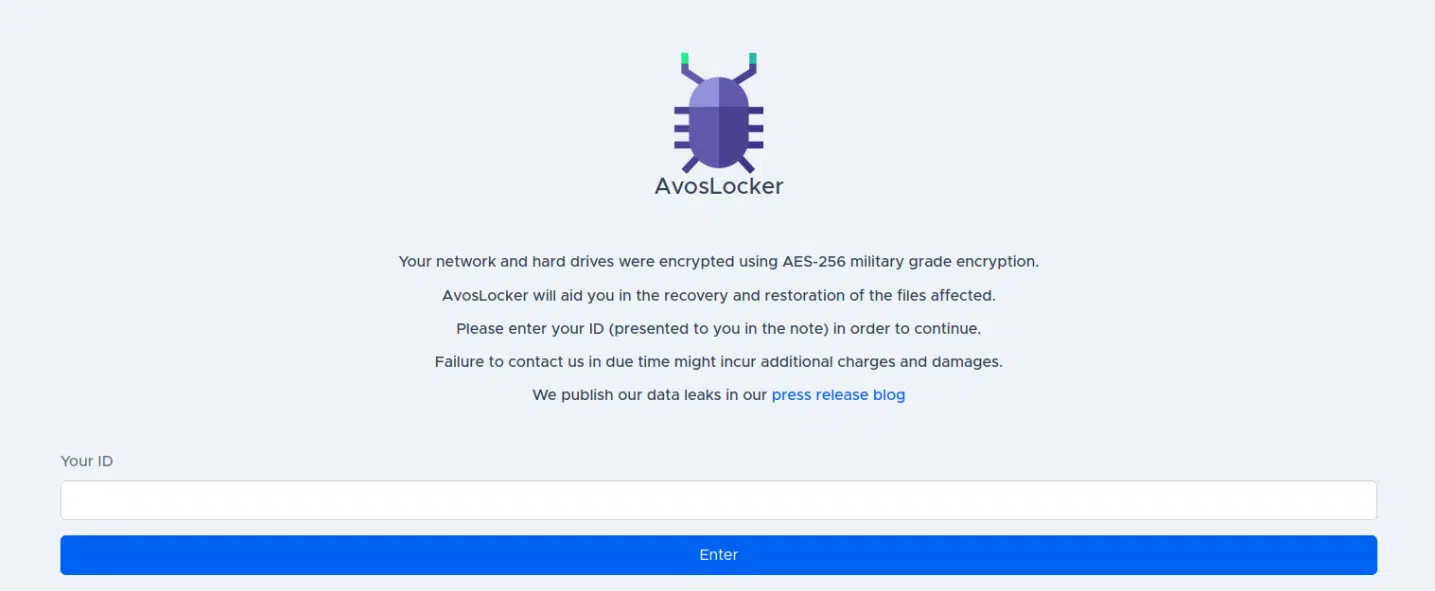
After providing the ID to the TOR landing page of AvosLocker, a new screen with a chat window will appear, and a countdown clock with the requested amount will appear.
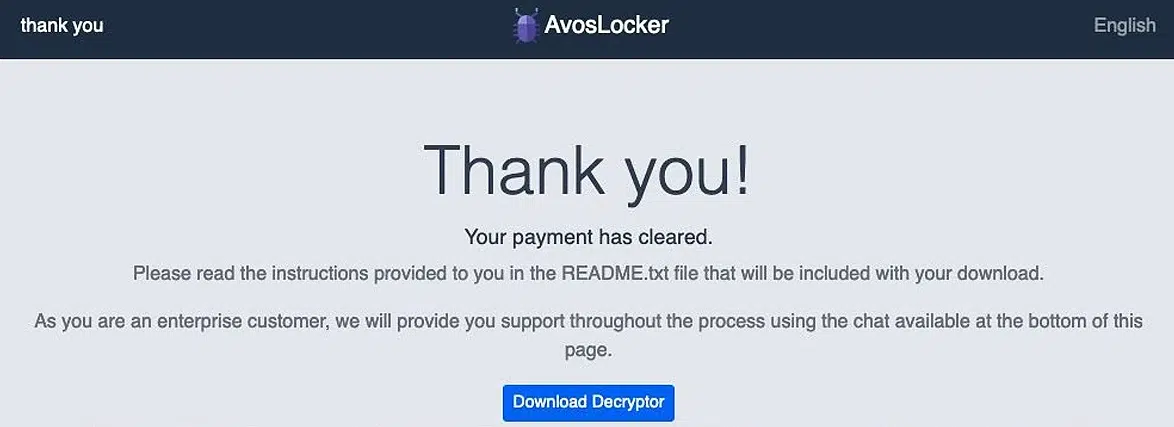
Once you complete the transaction, a thank you message will appear, and the decryptor will be provided to allow the victim to regain his files.
AvosLocker, only months from its “launch”, already made headlines. It appears that the group does not use any third-party services or collaboration with other groups, as already seen with the Conti ransomware group, delivered using Emotet malware, ever since its return last year.
We have seen what we can call “knowledge collaboration”, where we see several groups copying, or using the same techniques, incorporating them into their own arsenal, as we have recently seen with AvosLocker’s latest mention of a Linux variant targeting ESXi servers, a method performed by other ransomware gangs in the past, including Darkside, RansomExx, and Babuk Locker.
After several months of operation, the AvosLocker gang started to add to the already massive pressure on victims using the “Buy” button, which allows the highest bidder to buy the leaked data, instead of making it publicly available.
Once you click the “Buy” button, nothing happens. At the moment, you are redirected to a “Missing page” error. This could be a setup for a future business or simply another way of pressure towards the victims.
As part of their effort to increase their operations and the RaaS business model, some glitches can occur, as seen by the gang last December. Bleeping computer reported that one of the gang’s affiliates successfully targeted a US government police agency. The gang posted an apology and published the decryptor for free since this is not on their agenda for target sectors. “You should note, however, that sometimes an affiliate will lock a network without having us review it first” the AvosLocker operator told BleepingComputer. The result is that sometimes the gang’s “agenda” is disregarded, just for the sake of another successful infection.

AvosLocker made quite a name for themselves, there is no question about it.
Looking at Q4 2021, with over 40 victims, and comparing it to Q1 2022, even though there’s still time in Q1, there are only 6 victims so far, and it appears that the AvosLocker gang has a lower success rate compared to the previous quarter. However, with more tricks up its sleeve, we will probably keep on hearing about this group.
Cyberint Research Team predicts that they could return to one of the “top” ranked ransomware gangs, right below Lockbit and Conti, which currently dominate the market. They keep updating their tools, with the latest addition of ELF files to approach the Linux market, and recruitment ads still appear on forums to allow their growth to continue.
Sha256
ELF Linux samples
10ab76cd6d6b50d26fde5fe54e8d80fceeb744de8dbafddff470939fac6a98c4
7c935dcd672c4854495f41008120288e8e1c144089f1f06a23bd0a0f52a544b1
0cd7b6ea8857ce827180342a1c955e79c3336a6cf2000244e5cfd4279c5fc1b6
Recent Windows samples
f810deb1ba171cea5b595c6d3f816127fb182833f7a08a98de93226d4f6a336f
c0a42741eef72991d9d0ee8b6c0531fc19151457a8b59bdcf7b6373d1fe56e02
84d94c032543e8797a514323b0b8fd8bd69b4183f17351628b13d1464093af2d
Onion Sites
Leak site
hxxp[:]//avosqxh72b5ia23dl5fgwcpndkctuzqvh2iefk5imp3pi5gfhel5klad[.]onion
Drop site
hxxp[:]//avosjon4pfh3y7ew3jdwz6ofw7lljcxlbk7hcxxmnxlh5kvf2akcqjad.onion
©1994–2025 Check Point Software Technologies Ltd. All rights reserved.
Copyright | Privacy Policy | Cookie Settings | Get the Latest News
Fill in your business email to start


