

Highly motivated, problem solver, dot connector, energetic multi-dimensional & professional management with commercially oriented, customer service skills & PMO abilities in high-growth, fast-paced organizations.
During the past month, the following notable high-severity vulnerabilities have been observed. It is recommended that those using affected products take immediate action to assess their exposure and patch and/or remediate as necessary.
A new vulnerability was found in Windows Installer allowing elevation-of-privilege (EoP). Exploiting this vulnerability which received a CVSS score of 7.8, will be possible when a threat actor already has gained access to the targeted Windows machine with Microsoft Edge installed. Although Microsoft claims the issue was fixed on November’s patch Tuesday, Abdelhamid Naceri, the researcher that found this vulnerability, claims that the fix provided for this issue does not work properly and the published proof-of-concept (POC) still works on patched Windows 10, 11 and Server 2022.
The specific flaw exists within the Windows Installer service. By creating a junction, an attacker can abuse the service to delete a file or directory. A threat actor looking for an elevation of privileges can utilize this vulnerability and execute an arbitrary code with SYSTEM privileges.
The proof-of-concept (POC) technique that is implied is an overwrite of Microsoft Edge elevation service “Discretionary Access Control List” (DACL) and copy desired executable to the service location, then executes it to gain elevated privileges.
Given the fact that the POC is efficient and works properly with minimal effort, it is highly likely to see many threat actors utilizing this POC as a part of their campaigns. Although a threat actor still needs to have local access to the targeted Windows machine, It still might be a popular weapon as part of the deployment process of a certain malware, taking part in a bigger campaign.
While Microsoft didn’t address the issue rather the POC exploits the patched versions or if another fixed should be expected, Cyberint has already found a high number of malwares that are weaponized with the exploit mechanism.
norm_id=WinServer label=Application label=Install application="test pkg"
Released on November 9th, 2021, and with CVSS 8.8, a new Remote Code Execution (RCE) vulnerability was discovered in Microsoft Exchange 2019 and 2016 servers, including exchange hybrid mode users.
A proof-of-concept (POC) was published, and the most popular is the one a security researcher name “Janggggg” has released.
This exploit enables authenticated threat actors to execute code remotely on vulnerable servers.
Microsoft’s November 2021 Patch Tuesday addresses this issue.
Remote code execution vulnerabilities might have severe consequences, and this case is not different. As mentioned, successful exploitation will grant a threat actor the ability to set up for an attack on an organization network without local access to the machine itself.
The overall flow of the attack according to the POC published goes through 4 different POST Requests, all to the /ews/exchange.asmx URL, while using a User-Agent ExchangeServicesClient/15.01.2308.008.
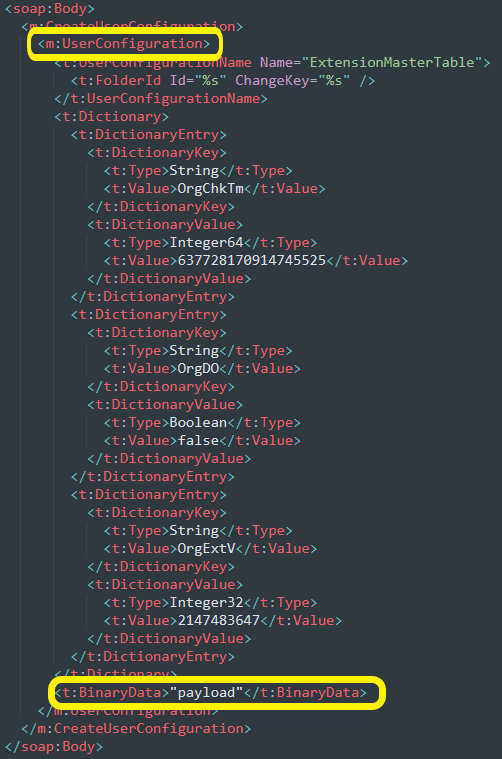
Microsoft Exchange servers, allowing certain data to be stored in the BinaryData section of a UserConfiguration (Figure 1) on a directory /ews within the server. When a UserConfiguration is set with a payload in the BinaryData, threat actor can perform a POST request for the ClientAccessToken, leading to a deserialization bug that results in the execution of the payload stored in the BinaryData.
Although this exploit is fairly simple to exploit, especially when POC is already provided, it seems that threat actor will need to be authenticated, making this exploit less probable and demands compromised credentials to be leaked prior.
While Microsoft claims they are aware of ‘limited targeted attacks’ using this vulnerability, They have also published a fix is already available and urges everyone using the affected products to update as soon as possible.
Application Source and the ErrorType Object should be “BinaryFormatter.Deserialize”.POST requests containing the /ews/exchange.asmx URL and the ExchangeServicesClient/15.01.2308.008 User-Agent in a relatively short time coming from a remote host. Although this solution might cause a number of false positives.
A new critical vulnerability with CVSS score of 8.4 was found in:
The vulnerability exists due to an input validation bug when processing Excel files.
Threat actor that is looking to utilize this vulnerability should create a specially crafted Excel file and have the victim open it and execute arbitrary code on the system.
The vulnerability was apparently discovered by Microsoft’s Security Threat Intelligence Center (MSTIC). While the issue was addressed on Microsoft’s Patch Tuesday on the 9th of November, There are reports that suggest that the vulnerability is being exploited in the wild.
In order for the attack to go through, it is expected that a threat actor looking to utilize this attack should form a malspam campaign or apply other social engineering technique to lure a victim to open a weaponized document that exploiting the bypass.
Once successful, likely due to loading bug, the threat actor is able to execute code, thus compromising the victim’s machine.
As far is putting this scenario in a proper place as a campaign phase, it seems that this vulnerability will be a part of delivery phase of other malwares such as Trojans, RATs and ransomwares.
Fill in your business email to start