

The conflict that commenced on the morning of October 7 between Israel and Hamas, known as “Iron Swords,” has not only engaged physical battlegrounds but has also drawn the focus of numerous actors in the realm of cyberspace. Similar to the Russian-Ukrainian conflict, there’s a proliferation of individuals and groups attempting to utilize cyberspace as an additional arena. Their objectives extend beyond causing harm, often encompassing the orchestration of information campaigns and the shaping of global narratives.
The cyber landscape reflects diplomatic alignments worldwide. With public support from Russia and Iran for Hamas, various hacktivist groups affiliated with the Middle East, Islam, and Russia have reported launching numerous attacks on Israeli digital platforms. However, the impact of these attacks on Israel and its affiliates remains minimal at the time of this writing.
On October 7, 2023, at 03:30 GMT (06:30 AM local time), Hamas initiated attacks on Israeli cities, launching thousands of rockets toward densely populated areas in southern and central Israel, including Tel Aviv and Jerusalem. Air raid sirens prompted civilians to seek shelter.
A distributed denial-of-service (DDoS) attack is a malevolent effort to disrupt the regular flow of traffic to a designated server, service, or network by inundating the target or its adjacent infrastructure with an excessive volume of internet traffic. The effectiveness of DDoS attacks is realized through the utilization of numerous compromised computer systems serving as sources of attack traffic. These exploited machines encompass not only computers but also other networked resources, such as IoT devices.
DDoS attacks stand out as one of the most commonly employed methods in cyber conflicts between nations. Instances of these attacks have been observed in the ongoing cyber warfare between Russia and Ukraine, as well as in activities involving state-sponsored groups from Iran and China. The Israel-Hamas conflict has also witnessed the use of DDoS attacks, as the main attacking method.
On October 7, as per Cloudflare systems, approximately twelve minutes later, they autonomously identified and mitigated Distributed Denial of Service (DDoS) attacks targeting websites crucial for providing information and alerts to civilians regarding rocket attacks. The initial attack peaked at 100k requests per second (rps) and lasted ten minutes. Subsequently, forty-five minutes later, a second, much larger attack occurred, peaking at 1M rps and lasting six minutes. Additional smaller DDoS attacks continued to target the websites in the following hours.
The conflict between Israel and Hamas has witnessed a notable resurgence of hacktivism. In response to the events on the ground, various groups have turned to the digital realm to express their viewpoints, support their respective sides, or disrupt the opposition. This renewed interest in hacktivism highlights its effectiveness as a tool for non-state entities to shape global perceptions and impact international events. The conflict serves as a reminder that, in the digital age, a keyboard can be as influential as a missile in shaping global narratives.
The Israel-Hamas conflict demonstrated the rapid evolution of hacktivist tactics, with groups employing various strategies, including leveraging botnets and implementing automated attacks for increased impact. Furthermore, hacktivist groups distributed tools and scripts to their supporters to amplify their efforts. They set specific goals, fostered collaboration among different groups, and even encouraged individuals without technical expertise to participate in activities like email spamming and spreading false information.
This underscores the need for cybersecurity methods to adapt quickly.
Moreover, not only have hacktivists diversified and advanced their methods, but their toolkit has also expanded. Throughout the conflict, hacktivists utilized a range of strategies, from Distributed Denial-of-Service (DDoS) attacks to data breaches. This expansion is attributed to the widespread availability of tools, including numerous free or paid botnet services, scripts, stealers, and even ransomware, shared on platforms such as Telegram channels and hacker forums. The diverse array of tools at their disposal indicates an increasing level of sophistication among hacktivists, posing a significant challenge for those in the field of cybersecurity.
In a recent spear-phishing campaign, which amid the conflict between Israel and Hamas, the Iranian state-backed threat operation MuddyWater, also known as Mango Sandstorm and Static Kitten, targeted two Israeli organizations. This initiative involved the distribution of N-able’s Advanced Monitoring Agent remote administration tool. The campaign employed a “multi-stage social engineering” process, guiding recipients to open infected files from links within emails. Subsequent to infecting the victims, MuddyWater operators accessed the compromised devices using the administration tool, initiating reconnaissance on the targeted entities.
Allegedly, AnonGhost took advantage of a vulnerability in the real-time rocket alert app’s Application Programming Interface (API). Details about the purported attack were disseminated on the group’s official Telegram channel. The accompanying screenshot in the initial post indicates that AnonGhost disseminated false messages to the app’s users, proclaiming the imminent arrival of a “nuclear bomb.” “After successfully exploiting an API vulnerability, malicious actors managed to transmit spam messages within the app’s chat.
They assert that these messages should have reached ‘all 10k to 20k users of this application,’ as stated by researchers.
In addition, on November 16, the group attacked more Israeli websites and posted on their Telegram channel:
SIEGEDSEC
The hacking group SiegedSec asserts that it has directed its efforts towards Israel’s government infrastructure and Shufersal, the largest supermarket chain in the country. They have disrupted multiple devices and acquired entry into documents associated with the Israeli airline Israir, encompassing internal investigations and reports.
Furthermore, the group declared that they have successfully breached the database of Cellcom, a prominent telecommunications company in Israel. They claim to have gained entry to the customer support panel, providing access to approximately 180,000 customer records and support tickets that potentially contain sensitive and personal information. Despite this, Cellcom has not yet responded or confirmed the occurrence of the attack or any resulting damage to their assets.
Anonymous Global has declared an increase in their team as part of their ongoing campaign against Israel, recognized as #OpIsrael. The joining groups to the operation are: ‘Cyber Army Palestine’, ‘Cyber Toufan’, ‘Garnesia Team’, ‘Islamic Cyber Team Indonesia’, ‘ChaosSec’, ‘WeedSec’, ‘Team Insane Pakistan’, ‘Team R70 Yemen’, ‘Moroccan Black Cyber Army’, ‘Mysterious Team Bangladesh’, ‘Team TYG Yemen’, ‘1915 Team’, and ’SiegedSec’.
A hacker group aligned with Iran, known as Cyber Av3ngers, has asserted responsibility for targeting an Israeli electric contractor on October 6, allegedly causing a blackout in the city of Yavne. Representatives from both the electric utility and the city have not officially confirmed the occurrence of the attack.
Adl Ali, a hacktivist group that emerged in late September 2022 amid widespread protests against the Iranian regime following Mahsa Amini’s death, entered the scene on October 10, claiming to have targeted Israeli infrastructure. The group overtly aligns with the interests of the Iranian regime, identifying itself as “Iran’s freedom-loving youth.” Thus far, their primary focus has been on conducting informational operations aimed at opposition entities and individuals.
The group initially garnered attention by asserting that they had acquired documents and chat records through a cyberattack on the Komala Party of Iranian Kurdistan, alleging the party’s involvement in a plot to undermine the Iranian state in the “Mahsa Amini case.”
Haghjhoyan, also known as the “Peace Seekers,” first surfaced in October 2023. It is identified as a pro-Iran hacktivist group that has been gradually disclosing small collections of data belonging to Israeli citizens via its recently established Telegram channel. On October 8th, the group proclaimed a successful breach of the Israeli Red Alert Emergency System. Subsequently, on October 13th, 2023, Haghjhoyan announced their infiltration of numerous critical infrastructure targets across Israel.
During this revelation, the group shared screenshots from their virtual network computing (VNC) sessions within various utility-centric targets. Files serving as ‘proof’ of this breach were also disseminated through the Haghjhoyan Telegram channel.
Between October 15th and October 19, 2023, the group continued to announce new leaks and attacks, including the claim of infecting “1000” Israeli computers.
Another hacktivist group, identifying as Soldiers of Solomon, has asserted bold claims regarding the infiltration and compromise of critical infrastructure in Israel. They also assert ownership of a tailor-made ransomware named Crucio. On October 18th, 2023, the Soldiers of Solomon publicized their attack through the revived BreachForums.
This announcement was also disseminated through their public Telegram channel, with the comprehensive message stating: “The Soldiers of Solomon have gained complete control over more than 50 servers, security cameras, and the smart city management system in the Nevatim military area. Upon obtaining access to these targets, we extracted 25TB of data and held them ransom using our customized Crucio ransomware (Ltd). Database Link: https://www.mediafire.com/folder/5fahf8k…/All+Files.”
The ‘proof’ package, hosted on MediaFire, encompasses the same screenshots provided in their Telegram channel.
The Cyber Toufan Operation group, establishing their Telegram channel on November 18, announced a substantial attack initiated on November 16, that is part of their efforts against Israel in the Iron Swords conflict.
The group targeted numerous Israeli companies, including government related entities. The breach stemmed from the group’s attack on Signature-it, one of Israel’s major data storage firms responsible for hosting various websites on its servers. Following the attack, the group provided additional details, claiming the destruction of over 1000 servers and critical databases.
Cyber Toufan Operation compiled a comprehensive list of affected victims, which can be found at the bottom of the blog. The group also declared their intention to release a leak from the victim list daily, having already disclosed breaches from Ace and Shefa Online companies. The Ace company leak comprised a 1.99GB database, while Shefa Online’s contained 5.7GB. Some websites belonging to the listed victims have been inaccessible since yesterday. The group published the leaked information on their official Telegram channel and in a dark web forum.
The Cyb3r Drag0nz Team, recognized for its history of launching DDoS attacks, cyber defacements, and involvement in data leak activities, is currently attributing multiple leaks and DDoS attacks against Israeli targets. Notably, they claim responsibility for a DDoS attack on the official website of the Israeli Air Force.
The Cyb3r Drag0nz Team asserts to have exposed data pertaining to over a million Israeli citizens through various leaks. Up to now, the group has disseminated numerous .RAR archives containing purported personal information about citizens across Israel.
Utilizing various social media platforms, including Instagram, Twitter, Telegram, FaceBook, and YouTube, the Cyb3r Drag0nz Team actively utilizes these channels to announce their targeting strategies and intrusions.
A certain group is involved in defacement attacks against Israeli websites, displaying a particularly offensive message featuring a Holocaust image. There is limited information available about this group; however, they maintain a Telegram channel that was previously known for selling exploits and has now shifted its focus to anti-Israel activities, aligning with the #OpIsrael hashtag commonly used by pro-Palestinian groups.
A pro-Palestinian group operating from Malaysia is actively utilizing social media platforms like Telegram, Twitter, and Instagram. This group engages in distributed denial-of-service (DDOS) and defacement attacks, recently concentrating on around 125 Israeli websites. Additionally, they assert to have breached Israeli telecommunication systems and share leaked databases.
Another group called Libyan Ghosts has started defacing small Israeli websites in support of Hamas.
According to a recent report by Cloudflare, during October 2023, starting from October 1, Cloudflare automatically identified and thwarted over 454 million HTTP DDoS attack requests directed at Palestinian websites utilizing Cloudflare. Although the figure below constitutes just a fraction of the attack requests observed against Israeli websites through Cloudflare, it represented a relatively larger proportion of the total traffic directed towards Palestinian websites employing Cloudflare.
Leading up to the Hamas attack, there were no observed DDoS attacks against Palestinian websites using Cloudflare. However, this changed on October 7, where over 46% of all traffic to Palestinian websites utilizing Cloudflare was associated with HTTP DDoS attacks.
By October 9, this percentage escalated to almost 60%, signifying that nearly 6 out of every 10 HTTP requests to Palestinian websites through Cloudflare were part of DDoS attacks.
In the preceding weeks, three Palestinian industries were targeted. The majority of HTTP DDoS attacks were aimed at banking websites, comprising nearly 76% of all attacks. The Internet industry was the second most targeted, accounting for 24% of all DDoS attacks, while a smaller share was directed at Media Production websites.
The full list of all threat actors involved with the cyber war between the sides:
A log file generated by malware (often stealers such as Aurora, RedLine, Vidar, and Raccoon) typically contains records or entries detailing the activities of a malicious software known as a “stealer.” The log file from a stealer may include various types of data and activities, depending on the specific functionality of the malware. Here are some common elements you might find in a log file generated by a stealer:
1. Stolen Credentials: This is a primary objective of stealers. Log files may contain usernames, passwords, and other login credentials stolen from the victim’s system.
2. Personal Information: Stealers often target personal information such as names, addresses, phone numbers, and email addresses stored on the infected device.
3. Financial Data: Some stealers focus on harvesting financial information, including credit card numbers, bank account details, and transaction records.
4. Browser History: Information about websites visited, login sessions, and browsing habits may be logged by stealers.
5. System Information: Details about the infected system, such as its operating system, hardware configuration, and IP address, may be recorded.
6. Keylogging Data: If the stealer includes keylogging functionality, the log file may contain a record of keystrokes, capturing everything the user types, including sensitive information.
Log files generated by stealers are concerning because they signify unauthorized access to and theft of sensitive data. From the beginning of the war, we observed an increase of almost 50% in the number of malware logs offered for sale that related to Israeli machines.
On October 30, SecurityJoes, an Israeli incident response company, shared findings regarding a new Linux wiper malware employed by pro-Hamas hacktivists during the Israel-Hamas conflict. This malware, currently tracked as the BiBi Wiper, was discovered by an incident response team assisting affected Israeli companies following a suspected Hamas-affiliated hacktivist group’s cyber intrusion.
The newly identified BiBi-Linux Wiper appears to be a highly specific cyberweapon designed to inflict damage on the infrastructure of these companies. Notably, this malware did not include a ransom note or command-and- control servers, leading responders to conclude that its sole purpose was data destruction.
Upon analysis, the incident response team found that the malware, named after the commonly-used nickname for the Israeli Prime Minister, “Bibi” (Benjamin Netanyahu), had the Prime Minister’s nickname hardcoded in the malware and in the extension of every destroyed file.
Additionally, a Windows variant detected by BlackBerry suggests that the threat actors are expanding the malware, targeting end-user machines and application servers. This indicates a shift in the attack strategy to include systems running on Windows, a widely used operating system.
| MD5 | e26bba0304f14ef96beb60376791d32c |
|---|---|
| SHA256 | 40417e937cd244b2f928150cae6fa0eff5551fdb401ea072f6ecdda67a747e17 |
| File Name | bibi.exe |
| File Size | KB (207872 bytes) 203.00 |
| File Type | Win PE x64 |
| Compiler | Visual Studio (2019) |
The timestamp on the BiBi-Windows Wiper indicates it was compiled on Saturday, October 21, 2023, just 14 days after the initial terror attack by Hamas. The malware is a x64 Windows portable executable compiled using Visual Studio 2019, with a file size of 203KB.
While the infection vector remains unknown, the malware checks the processor architecture and the number of threads in the victim’s system upon execution. To maximize destruction speed, the malware runs 12 threads with eight processor cores.
The wiping process excludes essential files (.exe, .dll, and .sys extensions), ensuring the computer’s basic operation. The targeted files are filled with random bytes, rendering them unusable and unrecoverable. The files are then renamed with a random sequence of letters and the extension “BiBi1” to “BiBi5.”
The malware also deletes shadow copies from the system, preventing file recovery unless offline backups are available. It disables the system’s trigger to call the Error Recovery screen on startup and turns off the Windows Recovery feature.
All CMD commands in the code use a right-to-left technique to bypass simple pattern detection rules commonly employed by legacy antivirus products. The BiBi-Windows Wiper relies on the Restart Manager and Rstrtmgr.dll to ensure the process completes.
A new version of the versatile ‘SysJoker’ malware has emerged, this time coded in Rust, a notable shift from its original C++ design. Initially unearthed in 2022 across Windows, Linux, and macOS systems, SysJoker evaded detection with in-memory payload loading and diverse persistence methods and remained undetected across all OS types on VirusTotal.
The new variant was linked to ‘Operation Electric Powder,’ an older cyber-attack series aimed at Israel, potentially connected to a Hamas-affiliated threat group known as ‘Gaza Cybergang’.The updated SysJoker, surfacing around the escalation of the Israel-Hamas conflict in 2023, employs intricate evasion tactics like random sleep intervals and custom encryption for its code strings.
Operating stealthily, it modifies the registry upon launch for persistence, communicates with a command and control (C2) server retrieved from a OneDrive URL, and executes commands via JSON-encoded instructions to download additional payloads.
While it still gathers system data, its newer version lacks previous command execution capabilities, possibly removed for a lighter, more covert profile. Two related samples named ‘DMADevice’ and ‘AppMessagingRegistrar,’were found, sharing operational traits, hinting at potential ties to ‘Gaza Cybergang’ through common attack techniques and patterns.
Attackers have extensively employed the RedLine Stealer malware to gather stored credentials from various applications, including browsers and the Windows Credential Manager. Numerous instances of fake installers for well-known software have been identified as carriers for the RedLine Stealer malware.
With this tool, the process of extracting and storing credentials from any application becomes notably straightforward. Once deployed, the malware scans the affected endpoint for a range of sensitive information, including Crypto Wallets, Browser Login Credentials, Cookies, VPN client credentials, and Instant Messaging Applications.
The screenshots posted on the Haghjhoyan Telegram channel reveal filenames that contain unseen and seen information, suggesting the utilization of malware. Based on the information shared by the threat actor, it seems they are employing these games as social engineering bait, manipulating individuals on social media platforms such as Discord, WhatsApp, and Telegram to download trojanized versions of the applications.
The strategy involves targeting users of highly popular games like Roblox, Minecraft, and FIFA, enticing them with the prospect of free ‘mod’ packages, proving to be an effective means to reach a broad audience within the general public.
According to SentinelOne investigation, Valuable insights can be derived from the leaked data itself. For instance, examining the stealer log output in the leaked file “IL-ISRAEL-25PCS-2023.rar” pertaining to ICS targets reveals a format that strongly suggests the utilization of Redline Stealer or a comparable type of malware.
This inference gains further support when we scrutinize another leaked screenshot provided by the threat actors. In this particular screenshot, the execution of the malware is showcased. Notably, the file name associated with the launched executable corresponds to the SHA1 hash of the malware. The SHA1 hash, represented as 0b0123d06d46aa035e8f09f537401ccc1ac442e0, is a publicly available sample of Redline Stealer dating back to 2019 and is not exclusive to the specific attacks and campaigns under consideration.
According to SentinelOne, In a separate screenshot shared by Haghjhoyan, there are indications suggesting the utilization of another malware tool known as PrivateLoader. The file “Subinfeudated Oat.exe” depicted in the aforementioned image serves as an example of PrivateLoader.
This tool, somewhat commonplace, is frequently employed as a means to download and execute additional malware payloads. Loaders like PrivateLoader or Smoke Loader enable lower-tier actors to circumvent basic detection controls such as traditional antivirus (AV).
By examining these instances, we can establish a connection between the use of PrivateLoader and Redline Stealer in the anti-Israel malware attacks orchestrated by Haghjhoyan. Present intelligence suggests that the data leaked by Haghjhoyan, obtained via Redline, is recent and authentic, having not been previously disclosed in the public domain. Additionally, it’s noteworthy that Haghjhoyan opted to make their Telegram channel private on October 24th, 2023.
In 2021, Anonymous declared a cyber war against Russia after the Ukraine invasion, with similar tactics seen in the Israel-Hamas conflict. Main attacks:
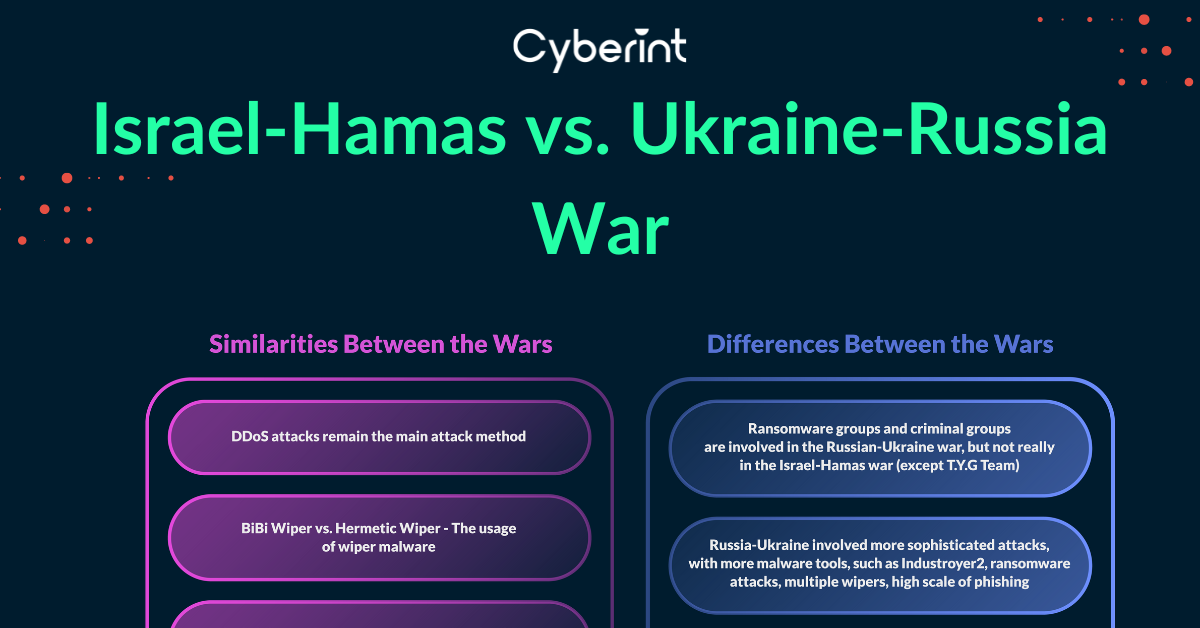
We saw the involvement of Russian and Ukrainians threat actors in the war of Israel Hamas, focusing on Hacktivists mostly from the Hamas and its supporters side, and a bit state sponsored groups. The biggest difference between the wars in the cyber field, is the involvement of other group types, such as crime syndicate groups (Ransomware), and other criminals.
Global Involvement The Russia-Ukraine war has drawn more global attention and involvement due to its impact on European security and international relations. The Israel-Hamas conflict, while receiving international attention, is more regionally focused.
Destructive malware has seen extensive use by Russian threat groups, particularly following Russia’s invasion of Ukraine in February 2022, with notable wiper malware such as DoubleZero, HermeticWiper, IsaacWiper, WhisperKill, WhisperGate, CaddyWiper, and AcidRain being employed.
HermeticWiper, a newly identified destructive malware variant, is designed to infiltrate Windows devices and incapacitate them by destroying files, corrupting the Master Boot Record (MBR), and affecting physical drives of Ukrainian organizations. Notably, HermeticWiper shares similarities with WhisperGate, a previous wiper-style threat utilized in cyberattacks against Ukraine. Moreover, HermeticWiper is associated with PartyTicket, a decoy ransomware often deployed alongside wiper threats.
Unlike BIBI WIPER, HermeticWiper does not establish communication with remote Command & Control (C2) servers for data exfiltration, employ reversible encryption algorithms, or use ransom notes to coerce victims into making payments. Instead, it causes harm by overwriting files with useless data, impacting both the data and the operating system.
The code base of HermeticWiper indicates a deep understanding of volume formats and their handling, despite differences in code quality. Both campaigns, however, have had a devastating impact on all systems where they were executed.
Additionally, HermeticWiper incorporates a decoy ransomware, PartyTicket, as part of its strategy.
In April 2022, researchers identified Industroyer2, a malware specifically crafted to target industrial control systems within Ukraine’s energy grid. It marked an advancement of the same malware that disrupted Kyiv’s power grid in 2016, albeit for a brief period. As of now, this stands as the sole publicly disclosed instance of malware potentially designed to induce a physical impact in Ukraine (it’s important to note that many potentially impactful cyber incidents remain undisclosed due to their classified nature).
Incident responders successfully neutralized the Industroyer2 malware before its pre-programmed timer could activate. This incident underscores the potential of cyber operations to inflict physical damage, but it also highlights their limitations, as the impact was thwarted before any harm could occur, negating potentially years of malware development.
The cyber attacks conducted by Russia and Ukraine involved a greater volume of activities, especially from the Russian side, including increased usage of malware, phishing, and disruptions to communication and internet infrastructure compared to the cyber warfare between Hamas and Israel.
Moreover, throughout this period, Russian state actors and affiliated threat actors persistently tried to compromise Ukrainian communication, transportation, energy, defense, administrative, and diplomatic systems and services. Additionally, Russia’s Federal Security Service (FSB) groups have been engaged in cyberattacks and intelligence activities targeting Ukraine.
On March 9 alone, the Quad9 malware-blocking recursive resolver intercepted and mitigated 4.6 million attacks against computers and phones in Ukraine and Poland, surpassing the European average by more than ten times. Cybersecurity experts observed a notable increase in phishing and malware attacks against Ukrainians through the blocked DNS queries originating from Ukraine. They also highlighted that the Polish numbers were elevated due to the presence of 70%, or 1.4 million, Ukrainian refugees in Poland at that time.
Before the outbreak of hostilities, Russia made numerous efforts to create a pretext for war. These efforts included multiple information operations on platforms like Telegram and Twitter, attempting to portray Ukraine as the aggressor while framing Russia as acting in self-defense. Across both traditional and social media, Ukraine and the US faced accusations of clandestinely developing biological weapons in undisclosed laboratories—a narrative recycled from the 1980s and previously used during Russia’s invasion of Georgia in 2008.
Additionally, videos depicting alleged Ukrainian sabotage of Russian targets and supposed shelling of a kindergarten by Ukraine emerged online just days before Russia’s invasion. However, these attempts to influence public perception were swiftly debunked by the Open Source Intelligence community through forensic analyses of the material. The US intelligence community also proactively countered Russian narratives in an effort to preemptively debunk them.
On the other hand, Since the Hamas attack on Israel on October 7, and even more so since the start of the Israeli strikes on Gaza, social networks have been accused of siding either with the Palestinians or, more often, with Israel. There have been accusations of “censorship” or, at the very least, unequal treatment. As early as October 10, Elon Musk, the chairman of X (formerly Twitter), posted a meme on his personal account mocking the “mainstream media,” which, he claimed, simultaneously accused his platform of being “an anti-Semitic cesspool” and “a Zionist propaganda machine.”
Social media platforms, including X (formerly Twitter), have become breeding grounds for misinformation during the Israel-Hamas war. These platforms, now under Elon Musk’s ownership, host a plethora of unverified claims and outright falsehoods propagated by both anonymous and supposedly “verified” users. In these digital arenas, propaganda and false information often spread more rapidly than the truth.
A notable case involves X user “Sprinter,” initially blocked for disseminating pro-Russian disinformation. Under Elon Musk’s ownership, Sprinter was reinstated and received a blue verification checkmark. The user went on to falsely assert that the Wall Street Journal had reported U.S.-made bombs being dropped on Gaza’s Al-Ahli Hospital. Ironically, this false claim garnered nearly six times more views than the authentic tweet from the Wall Street Journal about the same incident earlier that day.
According to the internet monitoring group NewsGuard, almost three-fourths of the 250 most popular tweets containing misinformation in the first week of the conflict were posted by verified users. Jack Brewster, a report author, noted that unlike past wars involving a significant number of automated accounts, the current wave of disinformation is primarily driven by “overwhelmingly real individuals.”
The cyberattack on Viasat, occurring between 5 am and 9 am EEST on February 24, appears to have had the objective of disrupting Ukrainian military networks. These networks utilized Viasat’s infrastructure for communication services. The attack was likely targeted at specific elements of military command and control in Ukraine.
Executed on Viasat’s KA-SAT satellite broadband modems, the incident resulted in the incapacitation of thousands of modems in Ukraine, including those crucial for military and governmental agencies. This led to a significant breakdown in internet communication. In a coordinated announcement on May 10, 2022, several Western governments presented evidence implicating Russia in the attack, linking it to their invasion.
The cyber conflict between Israel and Hamas is predominantly driven by hacktivist groups and state-sponsored entities on both sides. Iran sponsors groups like MuddyWater, and there are other groups associated with Hizballah that target Israel. On the Israeli side, cyber intelligence groups such as 8200, military units, and Ministry of Defense units are actively engaged in defense and countermeasures. Moreover, The activities of APT groups continue to come to light as time goes by, unlike hacktivists.
In contrast, the Russia-Ukraine war involved a broader range of threat actors, including ransomware groups and various cybercriminals who aligned with different factions and participated in attacks on diverse assets.
AgainstTheWest (not active anymore) a double-extorsion ransomware group, which is in charge of data leak campaigns in the US and China, also sided with Ukraine and already made some significant custom-made ransomware campaigns against Russia and published all the relevant information in their internal Telegram group.
While many threat groups are looking to make their appearance and show the world, they are active on the battlefield, some groups might regret coming out to the spotlight. One of them is CoomingProject (not active anymore), a French threat group that announced that they would retaliate if Russia becomes the target of cyberattacks.
Unfortunately for the ransomware gang, assembled in 2020, this announcement caught the attention of AgainstTheWest, a group that support Ukraine, attention, and the later was able to compromise and leak the identification of CoomingProject members, allegedly six young adults that are based in France. They have made the announcement on both their Telegram channel and their Twitter account.
Conti group is one of the most talented ransomware groups at the moment and they had the highest number of successful campaigns in 2021. Ever since the beginning of this campaign, we have monitored the reaction of Conti and Lockbit2.0 to the matter, trying to see and understand which side they are going to take. The story of Conti is complex when it comes to this conflict. The first announcement included a firm stance against Ukraine while Conti said that they fully support Russia.
While their Tor site looks confident, it seems that inside the group the announcement hit massiv waves given an emotional effect on the Ukrainian members of the group and sooner than later they have published a rephrase of their announcement declaring that they will support the Russian Federation only against the West and will not side with any government.
Several hours after the announcement Ukrainian researcher leaked highly sensitive data of the group including their training plans for newcomers, full Jabber conversation history from the last 13 months including affiliates and operators, Toolkit source code with a promise that more content is on the way.
The massive leak in particular and the way Conti decided to handle this conflict, in general, have caused severe damage to the group and give us some understanding regarding the group’s members’ maturity and professionalism. In cases in which the default languages of the victim’s machine are from Kazakhstan, Uzbekistan, Azerbaijan, Belarus, and Russia, the stealer will not proceed with its actions.
In contrary to most threat groups, including Conti, Lockbit2.0 have handled the situation differently and did not wanted to make any irrational decisions. With great anticipation from the cyber security community, Lockbit2.0 have made their announcement yesterday with one simple message – This is an apolitical business and no sides will be taken.
Figure 21 //
It seems that Lockbit2.0 is looking to make the best out of Conti’s and other ransomware group situations that are taking part in the conflict and looking to add more victims to their leak site with four new victims since the announcement and eight overall since the weekend. Furthermore, some speculation suggests that Lockbit2.0 is looking to buy the Emotet/Trickbot botnet one of Conti’s main delivery methods. This strategic buy might cause additional damage to Conti’s recovery.
Since the onset of the conflict, there has been a noticeable redirection of focus among major Russian-affiliated hacktivist groups, such as KillNet and Anonymous Sudan. They have shifted away from their usual narrative targeting Ukraine and Western countries to an increasingly extreme narrative against Israel.
These groups, along with those directly associated with them, actively share, repost, and quote various forms of derogatory content aimed at Israel and Israeli interests. They draw connections and parallels between Israel, Zionism, and Nazism—a narrative that was previously prevalent in their discourse about Ukraine. In the initial days of the war, KillNet post an alleged explanation in Hebrew (Using Google Translate) for their shift in attention from Ukraine to Israel.
It is important to highlight that among all the hacktivist groups, Anonymous Sudan, affiliated with Russia, was the first to engage in the conflict. They asserted that as early as Saturday morning, October 7, the Israeli public alarm system Tzeva Adom was rendered inactive by their actions. The group wholeheartedly dedicated themselves to the anti-Israeli cause and subsequently declared their successful disruption of the Jerusalem Post website.
Furthermore, Anonymous Sudan and KillNet established a joint channel for collaborative activities against Israel, though as of yet, there have been no claims of actual attacks posted in that space:
Anonymous Sudan and KillNet established a joint channel for collaborative activities against Israel.
While the name might suggest that the threat group is associated with Anonymous, it is not aligned with mainstream or Western-based Anonymous groups or OpRussia.
Anonymous operates in a decentralized manner, allowing anyone to claim affiliation with the Anonymous banner. Typically, Anonymous is known for its anti-political stance, but in this instance, Anonymous Russia expresses support for the Russian invasion of Ukraine and targets those who support Ukraine.
The group primarily focuses on defacements, data leaks, and denial-of-service attacks, acting in coordination with Killnet. Some of their notable targets include the European Parliament, U.S. airports, and U.S. government websites during midterm elections. The threat group is highly active on social media, consistently amplifying messages posted by other KillNet-affiliated groups.
Anonymous Russia was involved in attacks against Israel websites, from the beginning of the war between Israel-Hamas.
Not every Russian-origin group has adopted a distinctly anti-Israeli stance. The Cyber Army of Russia is seeking input from its users to determine its position, as depicted in the figure below.
The IT Army of Ukraine declared its support for Israel, but there are no indications that they will take any action.
Certain groups seek chaos, as indicated by ThreatSec, stating that they do not align with any specific side but expressing their intent to target Israel nonetheless.
The Russia-Ukraine war involves state actors, with Russia being a nation-state involved in military aggression. On the other hand, the Israel-Hamas conflict involves a non-state actor (Hamas) and a nation-state (Israel). As we saw, ransomware groups, and other threat actors are involved within the Russia-Ukraine war, not like in the Israel-Hamas war.
In the figure below, we can see the main differences and similarities between the wars in the cyber security field and the digital world in general.
Pro-Palestinian cyber activists have expanded their focus beyond Israel, targeting nations perceived as Israeli allies in the conflict against Hamas. The cyber operations primarily involve informational and retaliatory tactics, with limited reported damage. Target selection is influenced by the established focus areas of these groups and evolving geopolitical events.
As the war between Israel and Hamas, named “Iron Swords,” began on October 7, it also marked the start of increased cyber engagements from various threat actors. The ongoing war between Israel and Hamas has led to an expansion of cyber operations beyond the immediate theater of war. Hacktivist groups adapt their strategies to reflect unfolding geopolitical tensions, leveraging cyber tactics to influence public perception and national policies.
While the direct damage from these cyberattacks remains relatively contained, the broader implications highlight the need for robust cybersecurity measures. Nations and organizations must recognize the complex interplay between physical conflicts and their digital counterparts, necessitating a proactive approach in cyber defense to safeguard against cascading effects. The digital front is as critical as the physical one in the theater of modern conflict.
0b0123d06d46aa035e8f09f537401ccc1ac442e0
a25e93b1cf9cf58182241a1a49d16d6c26a354b6 8ade64ade8ee865e1011effebe338aba8a7d931b
| MD5 | e26bba0304f14ef96beb60376791d32c |
|---|---|
| SHA256 | 40417e937cd244b2f928150cae6fa0eff5551fdb401ea072f6ecdda67a747e17 |
| Malicious RedAlert APK Download URL | hxxp://redalerts[.]me/app.apk |
|---|---|
| Malicious RedAlert APK Command and Control | hxxp://23.254.228[.]135:80/file.php |
| Malicious RedAlert APK | 5087a896360f5d99fbf4eb859c824d19eb6fa358387bf6c2c5e836f7927921c5 |
izocraft[.]com
cricket-live[.]net
sports-et-loisirs[.]net
leaf-japan[.]net
london-sport[.]net
anime-con[.]net
gsstar[.]net
lrxzklwmzxe[.]com
im-inter[.]net
acs-group[.]net
dslam[.]net
it-franch-result[.]info
delooyp[.]com
tophatauc[.]com
gmesc[.]com
seomoi[.]net
jasondixon[.]net
alqassam[.]ps
nikanps[.]top
hamrah.nikanps[.]top
modir.nikanps.top
admin.nikanps[.]top
user.nikanps[.]top
nikanpsx[.]top
hz.nikanpsx[.]top
nikanpsx.hopto[.]org
isabeljwade[.]icu
francescatmorrison[.]icu
jayyburrows[.]icu
jessicakphillips[.]icu
185.209.31[.]193
176.114.6[.]214
91.107.188[.]236
91.107.129[.]43
198.54.117[.]210
5.45.81[.]22
04880196c8927d7fcaf32d6cc55f5b7a33858f65de70a968efc0ea8d9f7221c2
Cyberint’s impactful intelligence solution fuses real-time threat intelligence with bespoke attack surface management, providing organizations with extensive integrated visibility into their external risk exposure.
Leveraging autonomous discovery of all external-facing assets, coupled with open, deep & dark web intelligence, the solution allows cybersecurity teams to uncover their most relevant known and unknown digital risks – earlier.
Global customers, including Fortune 500 leaders across all major market verticals, rely on Cyberint to prevent, detect, investigate, and remediate phishing, fraud, ransomware, brand abuse, data leaks, external vulnerabilities, and more, ensuring continuous external protection from cyber threats.

©1994–2026 Check Point Software Technologies Ltd. All rights reserved.
Copyright | Privacy Policy | Cookie Settings | Get the Latest News
Fill in your business email to start


