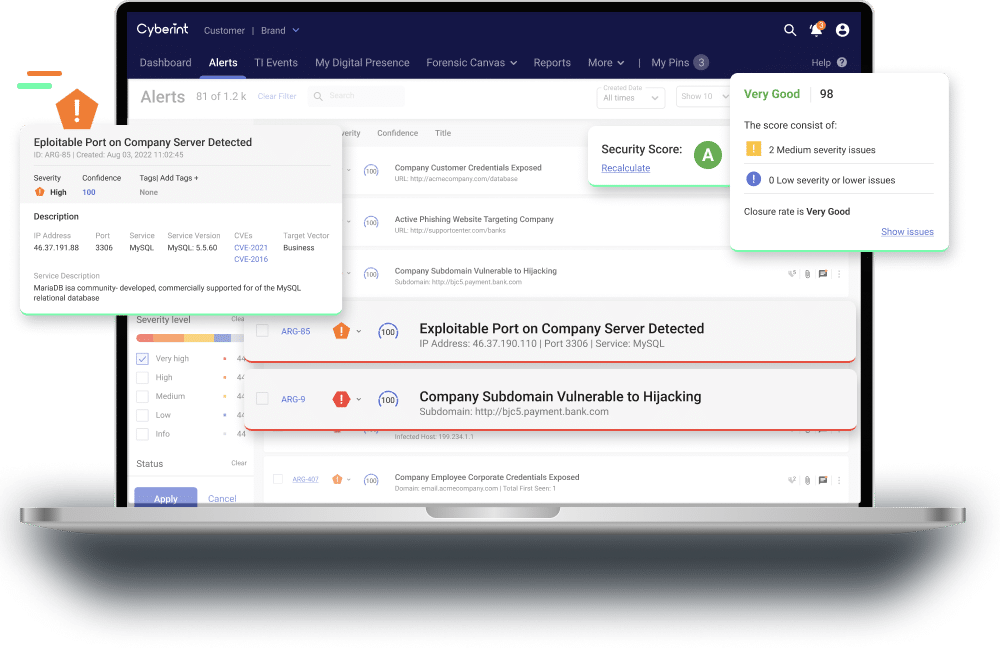
Impactful Intelligence To Continuously Manage & Mitigate External Cyber Risks
Attack Surface Management proactively discover, monitor and protect your organization’s digital assets.
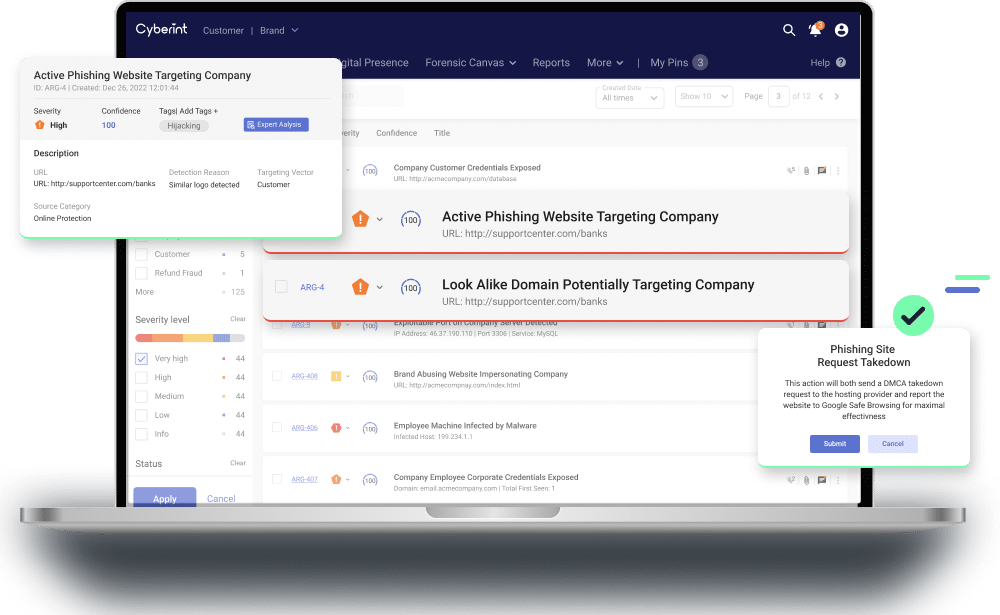
Detecting and blocking phishing and impersonating sites attacking your employees and customers.
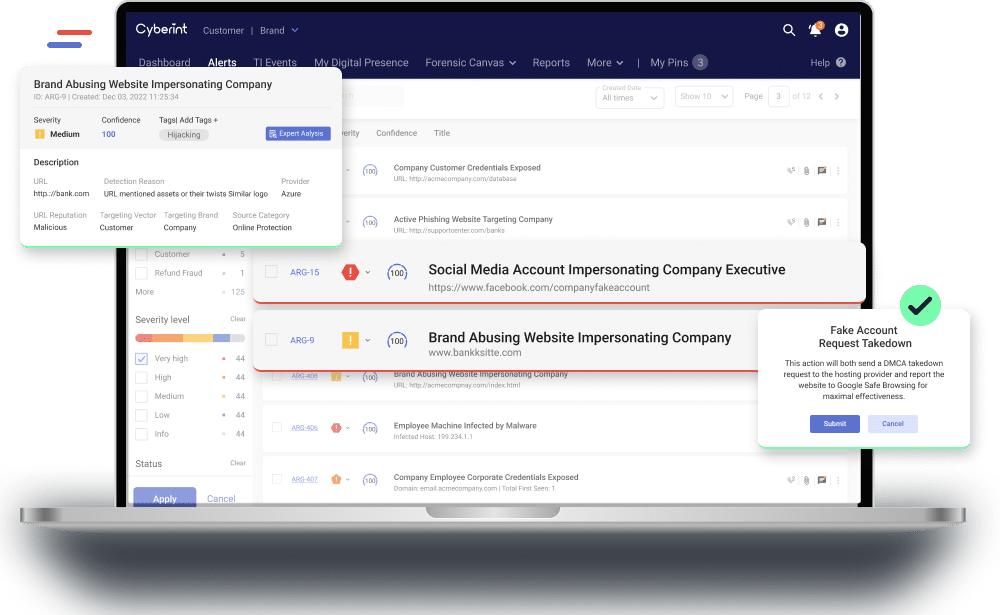
Identify fake accounts, 3rd party imposters and illegal trading that impact the brand and lead to cyber attacks.
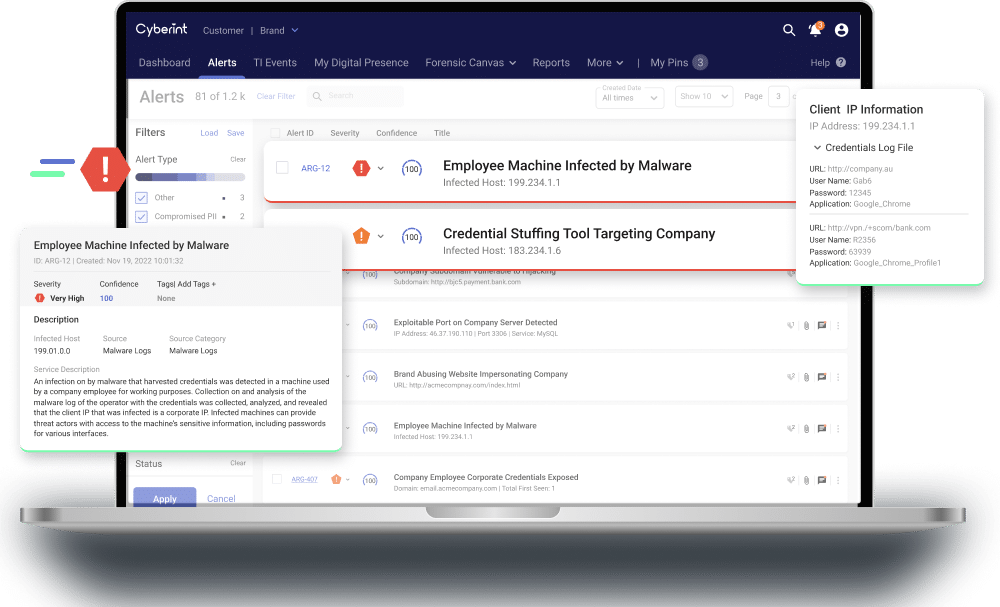
Prevent account takeover (ATO) and ransomware with real-time leaked data detection.
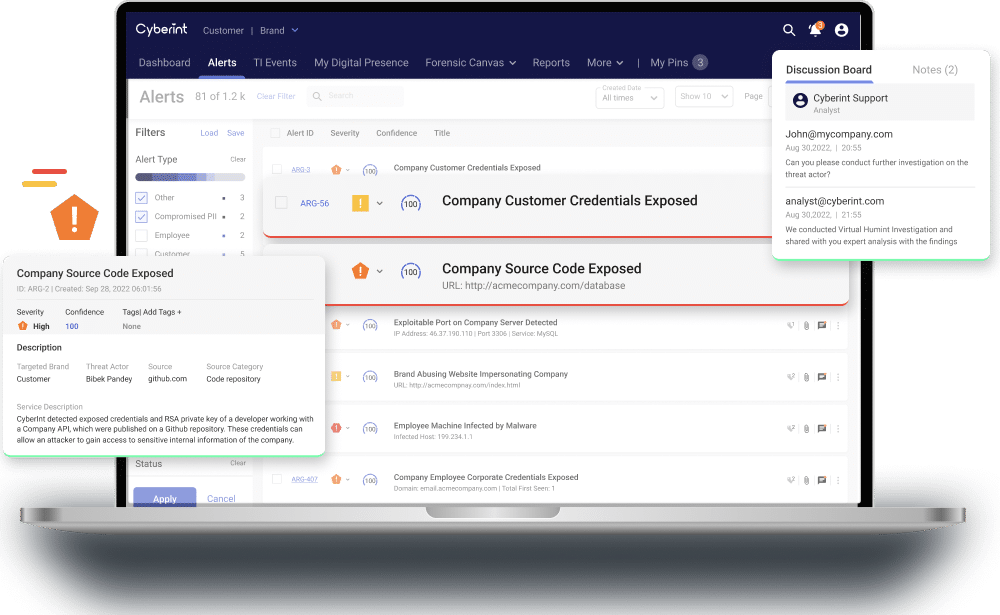
Identify malicious malware, applications or source code targeting the organization’s systems and technology.
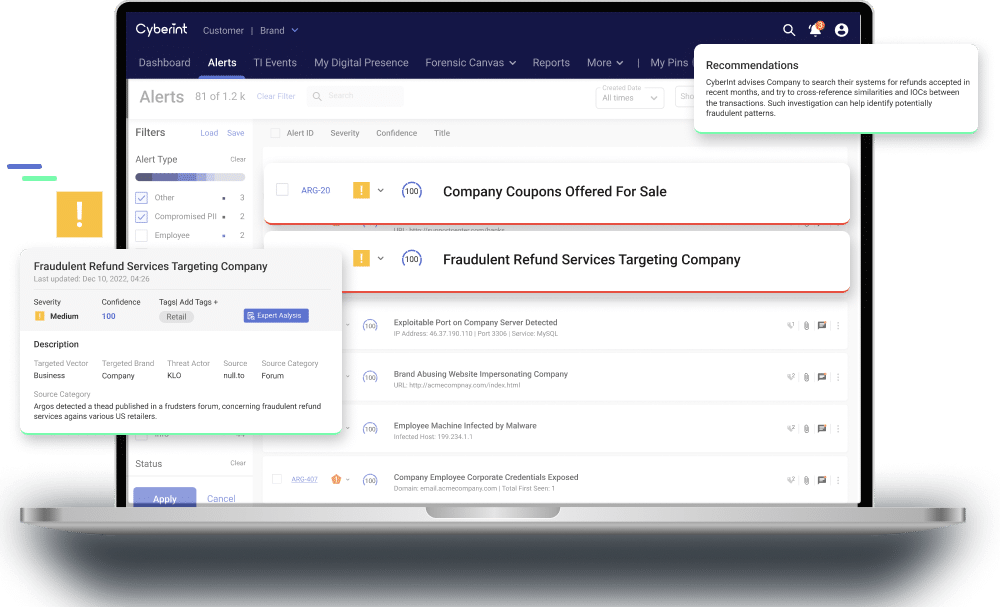
Identify and help mitigate internal or external fraudulent attempts reducing financial loss.
Cyberint Updates
-
Cyberint Named as Frost & Sullivan’s ‘Company of the Year’ in the Global External Risk Mitigation and Management Industry
Cyberint’s holistic approach offers unmatched visibility, in-depth threat insights, and continuous risk monitoring with an unparalleled market understanding, according to Frost & Sullivan.
-
-
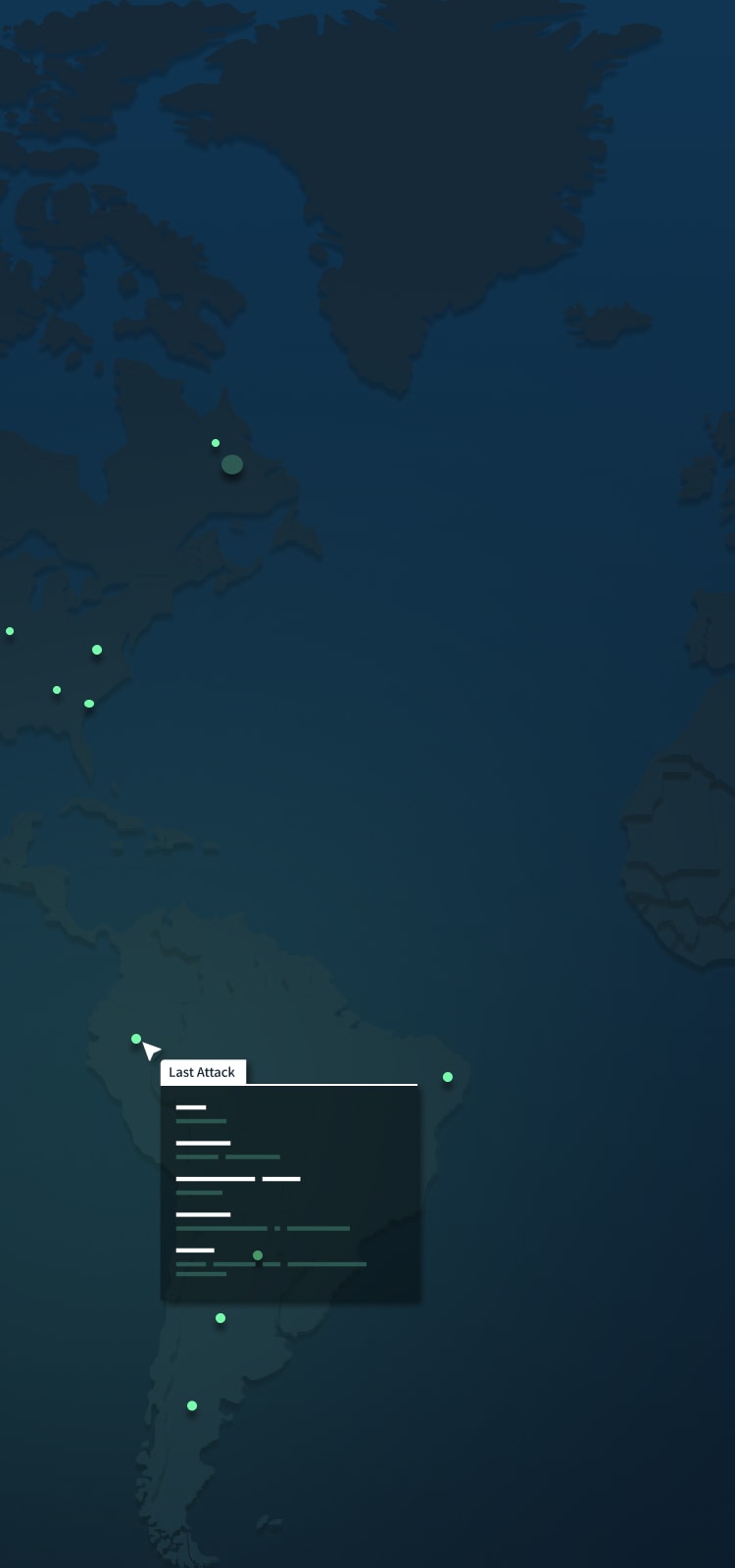

An Open Database Of Global Ransomware Activity
Turn your security into a business enabler!
Uncover your compromised credentials from the deep and dark web.
Fill in your business email to start.
Impactful Intelligence.
Groundbreaking Efficiency.
Real-time threat intelligence, tailored to your attack surface