Solution
One brain powering Threat Intelligence, Dark Web Monitoring, Attack Surface Management, Brand Protection, and Supply Chain Intelligence, because when everything thinks together, accuracy follows.
Watch Everything Connect
The Power of Consolidation
FAQs
How does the integration with Check Point affect the Cyberint platform’s roadmap and support?
After the acquisition by Check Point Software Technologies Ltd. (October 2024), Cyberint platform has been integrated into Check Point’s Infinity architecture.
What this means for customers:
-
You’ll see tighter linkage between external risk management capabilities and Check Point’s broader product ecosystem, meaning more data and faster fixes.
- You will be able to consolidate your cyber tech stack even further. Intelligence, prevention, and response operate through a single ecosystem rather than a patched-together stack.
Can I still engage with Cyberint as a standalone contract or do I have to go through Check Point?
The platform formerly branded “Cyberint” is now positioned as part of Check Point’s External Risk Management (ERM) offering.
Yet, you can still buy External Risk Management as a standalone offering, speak to External Risk Management salespeople and analysts and have your own External Risk Management customer support rep.
What exactly constitutes “external cyber risk” and which risk vectors does the platform cover?
“External cyber risk” means vulnerabilities and threats coming from outside-in e.g. internet-facing assets, cloud storage misconfigurations, leaked credentials, third-party vendor exposures, impersonation of your brand, deep & dark web activity.
-
Key risk vectors covered by the platform:
-
Attack surface management: discovery of assets (domains, subdomains, IPs, cloud storage) plus exposure detection (open ports, misconfigurations etc).
-
Threat intelligence / deep & dark web: monitoring what is being said, leaked, sold, or impersonated about your organization.
-
Brand protection: detection of fraudulent websites, social media impersonation, etc. ﹙implied by the platform messaging﹚
-
Third-party / supply-chain risk: risks arising from vendors or technologies you depend on.
-
Which modules can I activate/pay for separately (e.g., brand protection, supply-chain intelligence) vs. all-in-one?
The platform supports modular architecture, with Attack Surface Management (ASM), Threat Intelligence, Supply Chain Intelligence, Brand Protection offered separately.
But the solution offers the most value when these modules are bought together as they combine to reduce false positives, increase prioritization and are much more cost efficient when bought together.
How do you avoid flooding us with low-value alerts (false positives) and ensure actionable intelligence for our team?
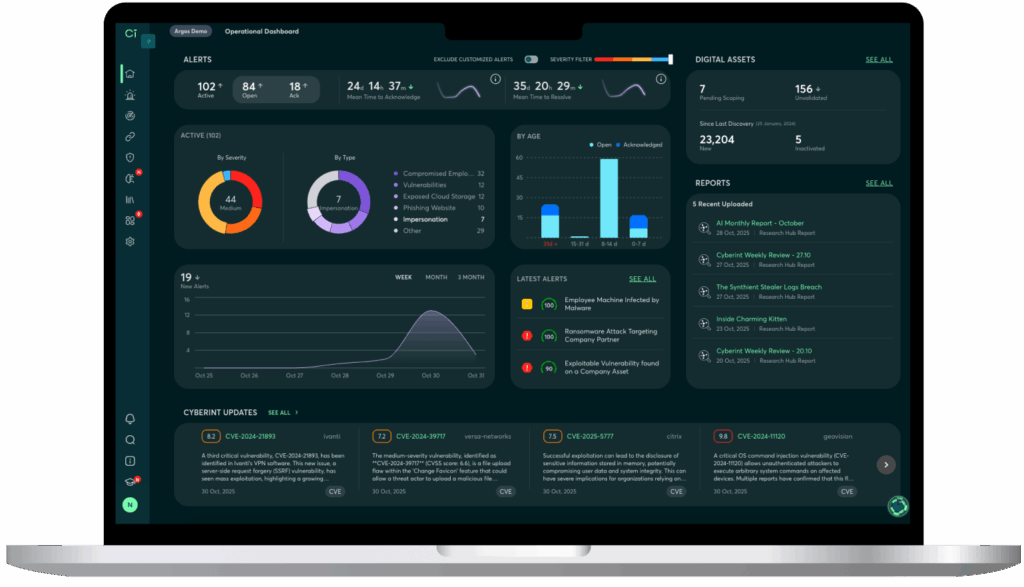
The platform emphasizes “Impactful Intelligence” and we live by that promise with a 93% true positive rate. Not only that, but each alert is enriched with context (code, screenshots and more), meaning not only are the alerts accurate but they are designed to be actionable.
Techniques used:
- Continuous monitoring and correlation of intelligence (not just raw feeds).
- The platform combines multiple data streams (Check Point’s global network data + Cyberint’s intelligence + OSINT) for higher confidence in IOCs.
- Risk-scoring asset and exposure; focusing on prioritisation rather than noise.
- Correlation between Attack Surface Management and Threat Intelligence – We only alert when intelligence matches your real assets, not generic internet noise.
- Credential-leak filtering based on your password policies
- If the leaked password format doesn’t match how your org structures passwords, we suppress it. No pointless “password123” alerts for accounts that can’t possibly be yours.
- Weighted multi-source confirmation: Intelligence signals from dark-web forums, marketplaces, Check Point telemetry and OSINT must reinforce each other before elevating an alert.
- Automated deduplication across sources – One leaked mention shouldn’t become five alerts. Correlation logic merges duplicates automatically.
- Human analysts verify ambiguous dark-web intel, stolen data samples and high-risk takedown-eligible items before you ever see them.
These are only some of the ways we make sure our alerts are true positives.
What’s the onboarding timeline — how quickly can we get up and running and see value?
We can deliver actionable intelligence within 20 minutes after setup. Since it’s an agentless SaaS offering (no on-prem installation), deployment time is faster than typical enterprise installs.
Full value (dashboarding, integration, remediation workflow) may take a few days to a couple of weeks depending on your complexity, as AI optimizes to your needs and the information feeds into the solution to enable a high true positive rate.