


There is a war going on. We see a twist in the cyber world considering recent events. While some groups take sides, whether in favor of Russia or Ukraine, some groups have gone MIA, and others are completely ignoring and continuing with their usual business model. And then we have Conti, which, as it appears, took the biggest tumble.
Conti is one of the most popular ransomware groups of our era. With around 600 successful campaigns in 2021 and total revenue of around $2.7 billion in cryptocurrency, Conti has become a massive crime organization and a consistent threat for every sector and region worldwide.
As the Russia-Ukraine conflict has gone beyond missiles and tanks to DDoS attacks, Conti was in a position where they could have picked a side or stayed silent. As we suspected, Conti chose to side with Russia, and this is where it all went south.
As mentioned, Conti had a massive impact on the cybersecurity world and stoked fear within every organization worldwide. It’s only natural for an organization of this scale, especially when observing a Ransomware-as-a-Service (RaaS) business model, to employ a variety of people from a variety of nationalities. Although it is true that the group mostly comprises people from the Russian region, it seems that some are also from Ukraine.
Once Conti’s senior management published the announcement about siding with Russia in the conflict (Figure 1), a chain of events unfolded that paved the way for Conti to the end its operations.

A few hours after the announcement, an alleged security researcher (presumably a former member of the team), who probably didn’t agree with Conti’s decision and might have had a strong connection to the Russian-Ukrainian conflict, decided to leak and expose every piece of information he could gather from the past two years.
The researcher opened a Twitter account (Figure 2) named @Contileaks and, every couple of hours, published new leaks about the group’s operations, chat history, training program, tools source code, guides, management guidelines, and of course, the source code of Conti’s ransomware malware.
The leaked details revealed Conti’s day-to-day work, negotiations with victims, discussions about strategies, cooperation with Emotet and Trickbot, government arrangements, affiliate payments and recruits, some names, and a very strong suggestions as to who the key members are and what Conti was really all about.
Conti’s conversations contained over 100K messages over the course of about two years, from June 2020 until recent days.
From these conversations, we were able to identify around 400 team members. As mentioned, the conversations include many aspects of the group’s operations.
Cyberint’s Research Team was able to map the conversations (Figure3) between the members of the team, thus identifying the key members and each one’s role.
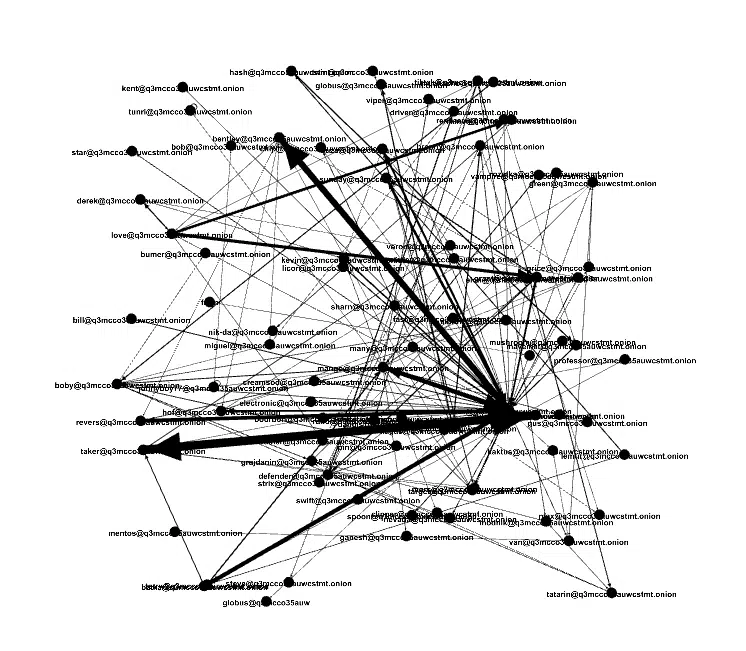
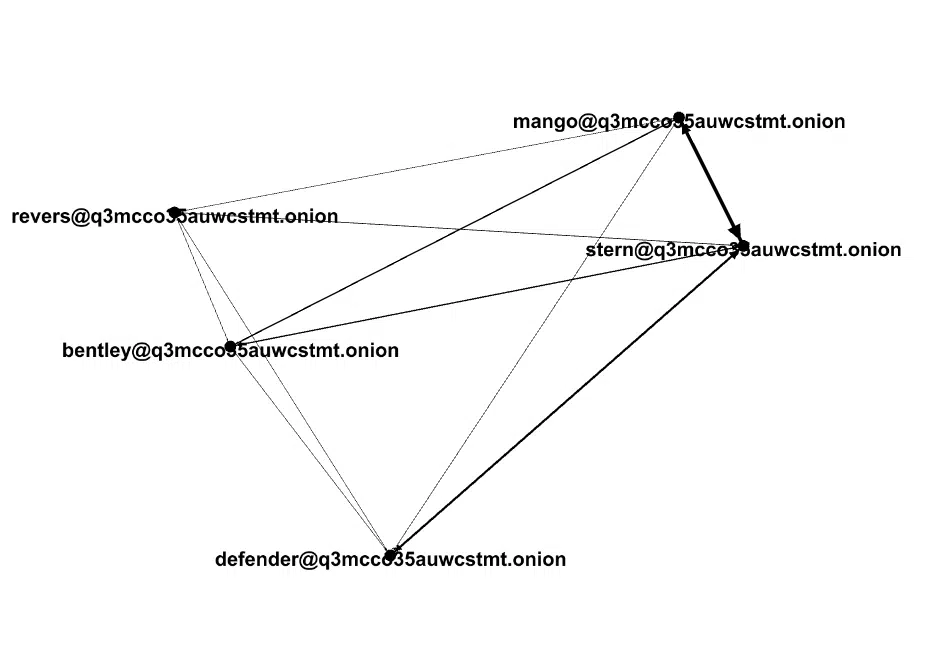
Although the leak contained many conversations, some which were irrelevant or “not work-related”, we were able to map the key members who had the most influence and communications with other members (Figure 4).
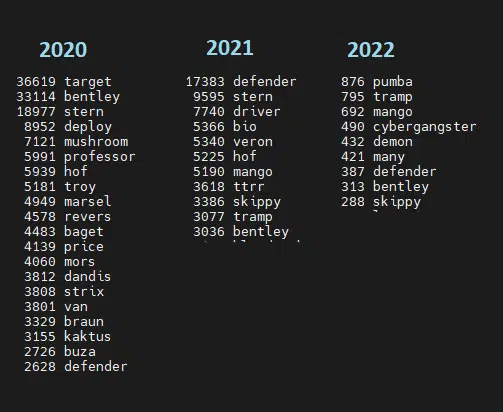
To get a better and more relevant view, we searched for the key members each year from 2020 to 2022 (Figure 5), which also helped us see the dominant newcomers.
This showed us, for example, that a new player in Conti’s team, Tramp, appears to be overlooked when we look at the total chatter, but emerges among the top chatter when it comes to 2022 alone.
As some of the figures within the group remain popular over time, we were able to find evidence that shed some light on their position and responsibilities within the organization.
It seems that Stern is one of the founding fathers of the group (Figure 6), some suggest he is also part of, or at least was a part, of Ryuk. Following Stern’s conversations, we can see he’s an experienced member who has direct contact with the Emotet group, talks a lot with other senior management figures within the organization, and, overall, doesn’t do too much technical work, but is very skilled and seems like a hands-on CEO.
Defender also seems like a high-ranking member of the organization, although the nature of his conversations mostly revolves around logistics and money management.
We witnessed Defender broadcasting memos and logistics messages to all the members of the group, and being asked for funds for paying infrastructure suppliers such as servers, licenses, and more.
We have seen particular cases where people took his advice on negotiations, but this is not his main role.
In terms of legitimate organizations, if we look at Stern as a hands-on CEO, Defender could easily be the COO.
Buza was mentioned in many conversations including Stern with a very curious member. In this conversation, Stern explained that Buza is some sort of a technology leader of the group.
Looking at Buza’s conversations with others, it seems like he manages the developers and their projects. We connected Buza to at least seven developers.
Conti includes several sectors and positions, but its core talents are the developers. As the product is changing rapidly and adaptability is required when it comes to new vulnerabilities and techniques, the skills required from the developers are major.
Although there are many developers, Mango and Bentley appear to be the more experienced and skilled of the bunch, and might even operate as hands-on mid-level managers.
Bentley and Mango communicate often about the development process as Bentley often takes part in the development of the malware cryptor. Bentley and his team apparently ensure that they are undetected by all or at least most AV vendors.
Mango and Bentley also have weekly meetings where Bently presents Mango with the stats about the improvements his team made.
As mentioned, in their efforts to improve their evasion techniques, Conti recruited skilled reverse engineers whose purpose was to reverse the ransomware software in order to improve their fingerprinting and crypting so the defense mechanisms wouldn’t be able to identify it.
One of the more experienced reversers and Conti veteran is Revers. This member mostly talks to the experienced developers and their team leaders, giving them his take on how the malware looks in terms of protection services.
Revers is the manager of other reverse engineers like Meatball.
Tramp is fairly new to Conti, and it seems that he arrived around July 2021.
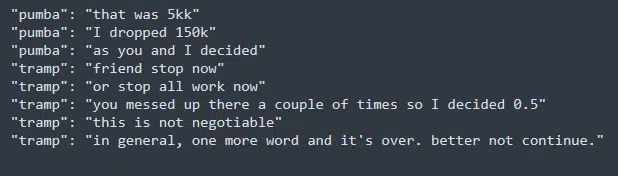
Looking at his conversation with other members, Tramp is no Red Teamer or developer, but rather a Team Leader of some kind. He is also in charge of distributing money to his team. In some cases, we have seen him taking charge of negotiation processes, and telling others what to say to the victims’ negotiators and what tone to use.
Even though Tramp is new to Conti, it seems that he knows his way around everything. This might suggest that he is not new to the industry, and it is possible that he was recruited from another group.
In addition, Tramp is very assertive when it comes to managing his people and looks very dominant, while in some conversations he refuses to pay an affiliate a certain amount and at some point even threatens to not pay him at all. At this point, the affiliate folds and accepts Tramp’s verdict, which points to his authority in the matter (Figure 7).
For years, major threat groups have been structuring themselves as major legitimate software companies, and Conti is no different.
Even though their activities were highly anonymous and had strict rules, they managed to create important sections for the group’s operations such as Business Development, RND, Finance, and even an HR department comprised of at least 2 people, “Viper” and “Salamandra”, who are in charge of recruitments, general questions, and even onboarding new members and introducing them to their team leads (Figure 8).
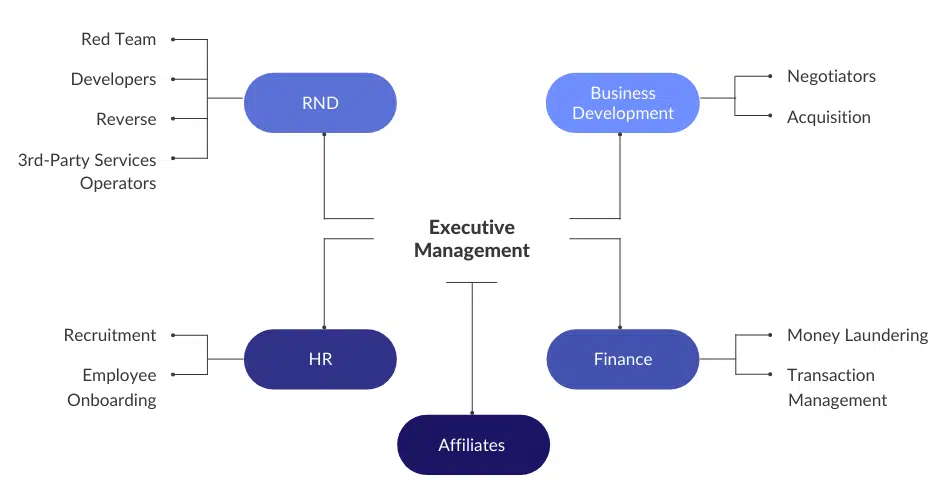
The business model and skill demanded from modern threat groups, especially ransomware, can’t be anything less than this. If we were able to get a peek inside other threat groups of this scale, e.g., Lockbit2.0, we would expect to see the same structure.
One of the “known” cyber security facts is that some countries have an “underground arrangement” with some groups encouraging the group to continue with their business as long as they share some of their findings with the government.
As Russia has been accused of sponsoring threat groups in the past, we thought we could learn more about Conti’s relationships with the Russian government from the leaked chats.
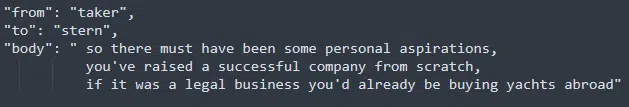
In one of the conversations in mid-2020, we found a conversation between Stern and a new member named Taker, that was pretty curious, and asked several great questions. One of the questions asked was regarding Conti’s arrangements with the government that allowed the group to be able to operate freely (Figure 9).
When it comes to the relationship with the government, Conti is in a position in which the Russian government is not cooperating with them, but they are aware that they might be one day.
Of course, ultimately there is always a possibility that Stern didn’t want the new member to know about what was really going on, so he bent the truth and focused on fin7 and fin8. But based on this conversation goes, Conti did not get any instructions from the government.
The relationship between Conti, Emotet, and Trickbot is no secret, while the latter two deploy Conti.
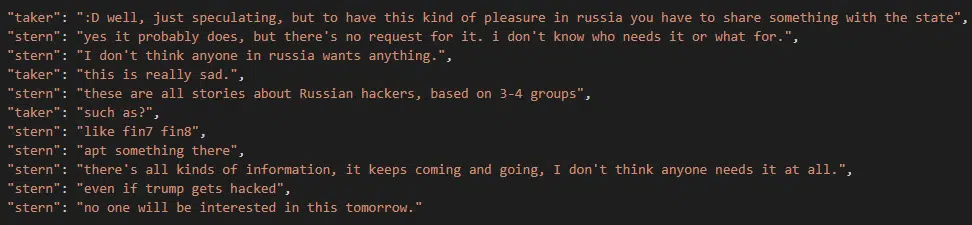
Looking at the leaked conversation, we could see that Conti’s veterans have a close and consistent relationship with the two as Stern admits he knows the operators and even praised Emotet for their support and solid product (Figure 10).

Furthermore, we saw that at least two Conti members claim to have direct access to the Emotet crimeware platform.
Overall, it seems that the Emotet infrastructure is already an integrated part of Conti.
Conti developed a training section that contains over 40 GB of educational material from assembly and coding, all the way to hacking materials, including e-books and videos. Unfortunately, they mainly used legitimate leaked courses and they did not take any part of them.
Like a legitimate software organization, Conti members maintained a strict policy when it comes to documentation (Figure 11). Multiple documentation files were found, all written in Russian, explaining each module in detail, including cheat sheets and step-by-step instructions for any scenario a member might come across, from initial infection to lateral movement.

One of the most interesting findings in the guides was a section about the importance of the members of the group monitoring and looking for how top security researchers and security firms perceive them.
The cyber security community closely observes and monitors actions of all types of threat groups, and now we understand that they study us, just as much as we study them. The goal is to see how much attention the group receives and how obvious or “trackable” their actions are. To cut a long story short, the cyber-security community has served Conti as their OpSec.
While most of the attention was turned to the leaked ransomware software, other tools and malware were found among Conti’s resources.
One of Conti’s common techniques is to use CobaltStrike. Looking at the leaked software files, we were able to find edited CobaltStrike tools and Russian-written manuals (Figure 12) for less-sophisticated threat actors and members who don’t know how to use the module. The manuals consist of step-by-step guides on how to use CobaltStrike in the context of a ransomware campaign.

Surprisingly, another module that was leaked was an XMRig module, with a hard-coded wallet.
XMRig is a high performance, open source, cross platform CPU/GPU miner, based on the stratum protocol. This is a legitimate mining tool often used by threat actors as a way to perform crypto mining activity on a compromised machine, and take advantage of compute power to create revenue.
While Conti is not known for adding mining to their campaigns, it might be a new application that we haven’t seen before, or it might be a code that was leaked and served few members for their “side hustle” beyond being part of the Conti group.
Without a doubt, the most important and devastating leaked information for the group is Conti’s ransomware code.
At first, the Ukrainian researcher who leaked all the information did not want to leak the code, claiming that if the code is leaked, other threat actors will abuse it, leading to more victims.
After some pressure asserted by the cyber security community, the researcher decided to leak the code (Figure 13).

The code consists of the main modules – Locker and Decryptor.
LOCKER
Like most ransomware families, Conti uses known algorithms such as chacha20 as their encryption algorithm. The key for the encryption is dynamically created.
As the Locker module is the most complex, it is packed with anti-debugging mechanisms and other tools such as process-killer, memory-patching, hooking, filesystem iterator, network scanner, and more.
DECRYPTOR
The Decryptor is straightforward. The module itself contains other modules that will operate the filesystem iterator and network scanning it demands in order to go over the encrypted files and decrypt the content.
As more information was leaked by @ContiLeaks, the group rapidly adapted to the situation.
The day after the first wave of leaks, Conti went took a “business as usual” approach and published a few more victims.
After they saw the reaction of the cyber security community, analyzing every leaked byte and every word written in the past two years, it seems that Conti’s senior management decided to mitigate the damage and tried to cover any tracks that might lead to any members of the group, especially seeing as some members were fully leaked, including faces and real names (Figure 14).

After the main leaks, the last conversations that were leaked showed that the decision was made to go off the grid for some time. It seems that the key members of the group are making efforts to ensure that all relevant files are deleted, all links shared within the conversations are dead, all servers used for the organization’s infrastructure are down.
Conti members were witnessed talking about the leak and trying to understand who the Ukrainian researcher is. They do believe, however, that he is a true member of the group who went rogue.
Although Conti’s leak site is still operating and new victims have been added, we can’t define if these are new victims, or victims they already compromised before the leak. One way or another, Conti will turn their efforts in the coming days or weeks to rebuilding their infrastructure and relocating all their communication channels and sources very carefully, so the Ukrainian research does not infiltrate this infrastructure as well.
Conti has suffered immeasurable damage caused by this massive leak, both professionally, with the source code revealed, and operationally, when it comes to the anonymity and hiding from law enforcement.
This historical leak offers us a rare opportunity to fully understand what one of the most nefarious groups of recent years looked like from within.
While the code leak will, undoubtedly, help us determine and identify Conti ransomware operations and steps when trying to mitigate their actions, it will also, like any open-source code, open the door for other skilled ransomware groups such as AvosLocker, Karakurt, BlackCat and more, to improve their systems and techniques, and even create a better product.
At the moment, we cannot determine if the group will return as a whole, or the members will split into different groups, or try to join Conti’s biggest competitor, Lockbit2.0.
Although this is a significant event in the cyber-security community, this might not be the last time we hear of Conti, or Conti’s ransomware.
©1994–2026 Check Point Software Technologies Ltd. All rights reserved.
Copyright | Privacy Policy | Cookie Settings | Get the Latest News
Fill in your business email to start


